A network isolation method, system, network card and application based on transparent computing
A technology of transparent computing and network isolation, applied in transmission systems, electrical components, etc., can solve the problem of no additional protection, and achieve the effect of simple structure, low cost, and guaranteed security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
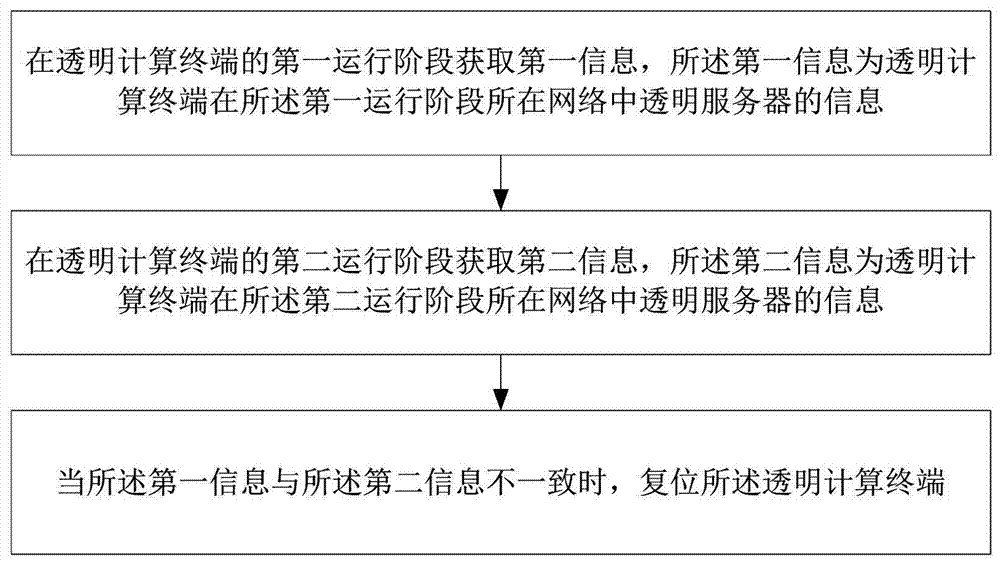
[0040] Such as figure 1 As shown, the network isolation method based on transparent computing in this embodiment includes: S1. Obtaining first information in the first operation stage of the transparent computing terminal, the first information is the transparent server in the network where the transparent computing terminal is located in the first operation stage information; S2. Obtain the second information in the second operation stage of the transparent computing terminal, the second information is the information of the transparent server in the network where the transparent computing terminal is in the second operation stage; S3. When the first information is inconsistent with the second information , reset the transparent computing terminal.
[0041] In this embodiment, the first operation phase and the second operation phase are the operation phases of the transparent computing terminal before the split node event occurs and after the event ends, which are determined ...
Embodiment 2
[0052] The isolation method of this embodiment is basically the same as that of Embodiment 1, except that steps S1, S2 and S3 are executed by a processor independent of the operating system of the transparent computing terminal. After step S1, when the preset split node event starts, isolate the connection between the transparent computing terminal and the network; after the preset split node event ends, execute step S2; in step S3, when the first information and the second information When consistent, restore the connection between the transparent computing terminal and the network.
[0053] In this embodiment, since steps S1, S2 and S3 do not depend on the operating system of the transparent computing terminal, including the super operating system and the instance operating system, an independent processor obtains the information of the transparent server from the network, including the IP address and UUID code. Therefore, when a preset split node event is triggered, the co...
Embodiment 3
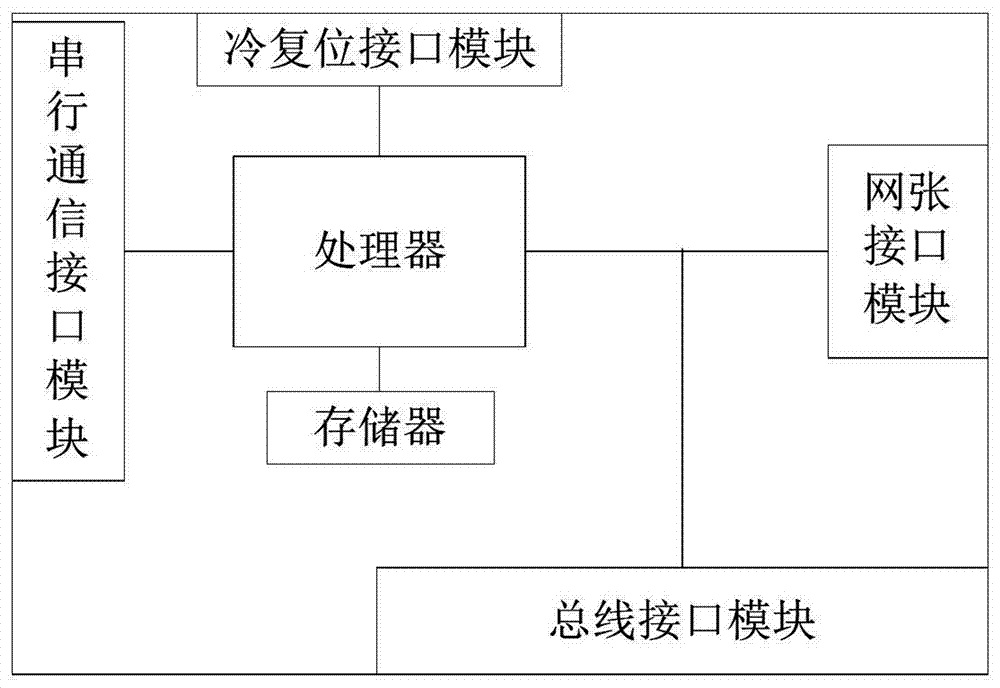
[0064] The isolation method of this embodiment is the same as that of Embodiment 2, and the isolation system of this embodiment is the same as that of Embodiment 2. The isolated network card of this embodiment is basically different from that of Embodiment 2, the difference is that: Figure 4 As shown, the isolation network card also includes an isolation controller, the processor is connected to the network interface module through the isolation controller, and the bus interface module is connected to the network interface module through the isolation controller; the isolation controller is used to disconnect or restore the network according to the control of the processor Connection between the interface module and the bus interface module.
[0065]In this embodiment, through the isolation controller, the connection between the transparent computing terminal and the network can be disconnected in time after the preset split node event is triggered, and until the network is r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com