Malware detection visualization method and system based on malicious network traffic lexicon
A technology for network traffic and malware, applied in instrumentation, computing, electrical digital data processing, etc., can solve problems such as user transparency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0101] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0102] The present invention can meet the following basic requirements:
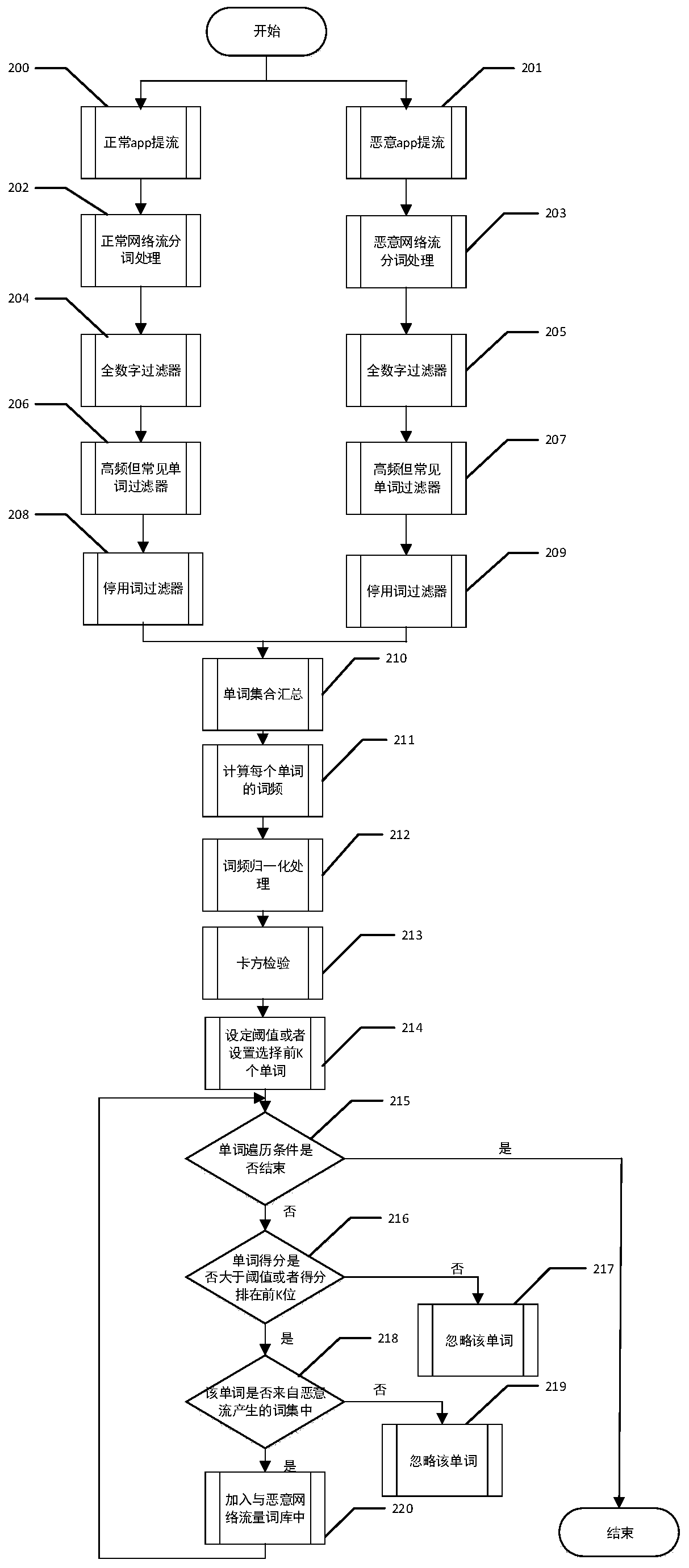
[0103] (1) A malicious network traffic lexicon is established, which can be applied to malware detection methods.
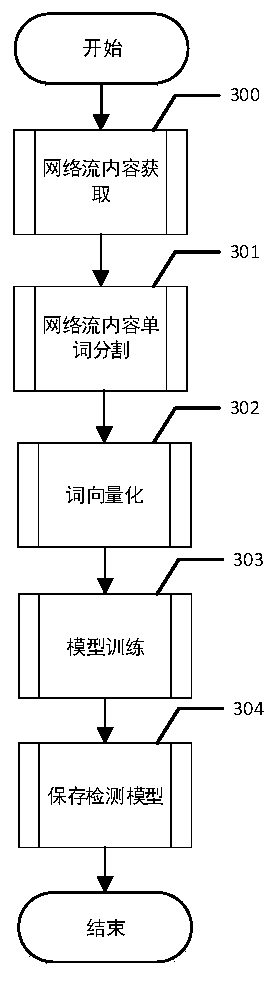
[0104] (2) Using the malicious network traffic lexicon established by myself, combined with the method of machine learning, a detection model was established.
[0105] (3) Visually display the malicious words in the network traffic generated by the predicted malicious app, and display the importance of each word in the malicious traffic in an intuitive form.
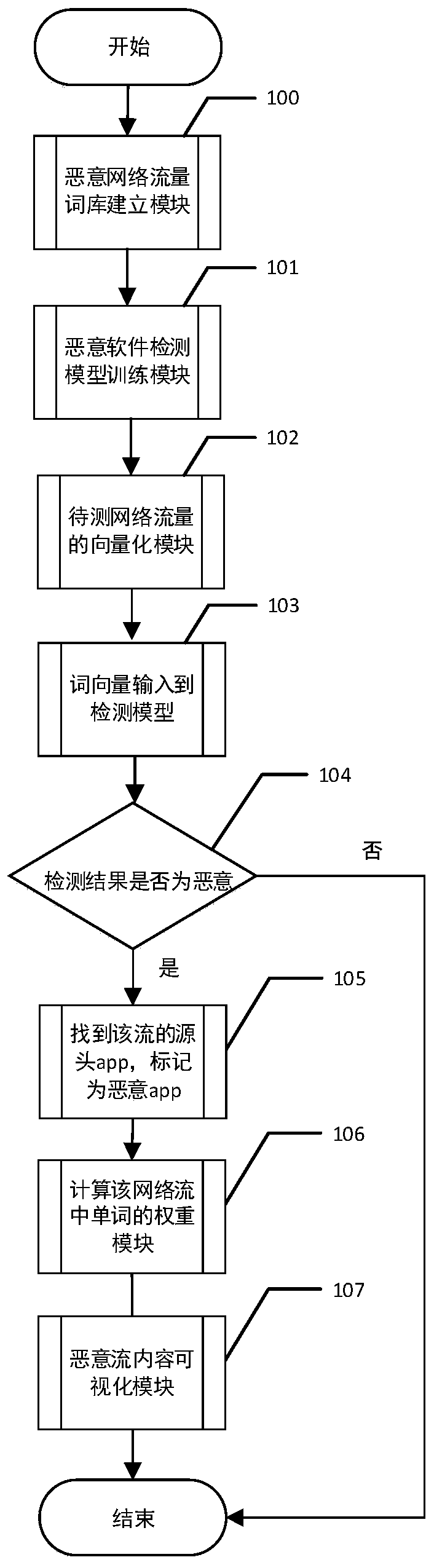
[0106] Such as figure 1 As shown, the malware detection result visualization method based on the malicious network traffic lexicon includes the following steps:
[0107] Step 100, a malicious network traffic lexicon building module. Through this module, a lexicon of malicious network traffic can be obtained...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com