Construction method and system for Java program trusted execution environment
A construction method and execution environment technology, applied in the field of establishing a trusted execution environment for application programs, can solve the problems of insufficient security of Java programs of computer systems, integrity damage such as Java bytecode tampering, memory tampering, etc., to meet the security requirements. and trustworthy requirements, protect integrity, improve security and the effect of trustworthy requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings, but the present invention can be implemented in various ways defined and covered by the claims.
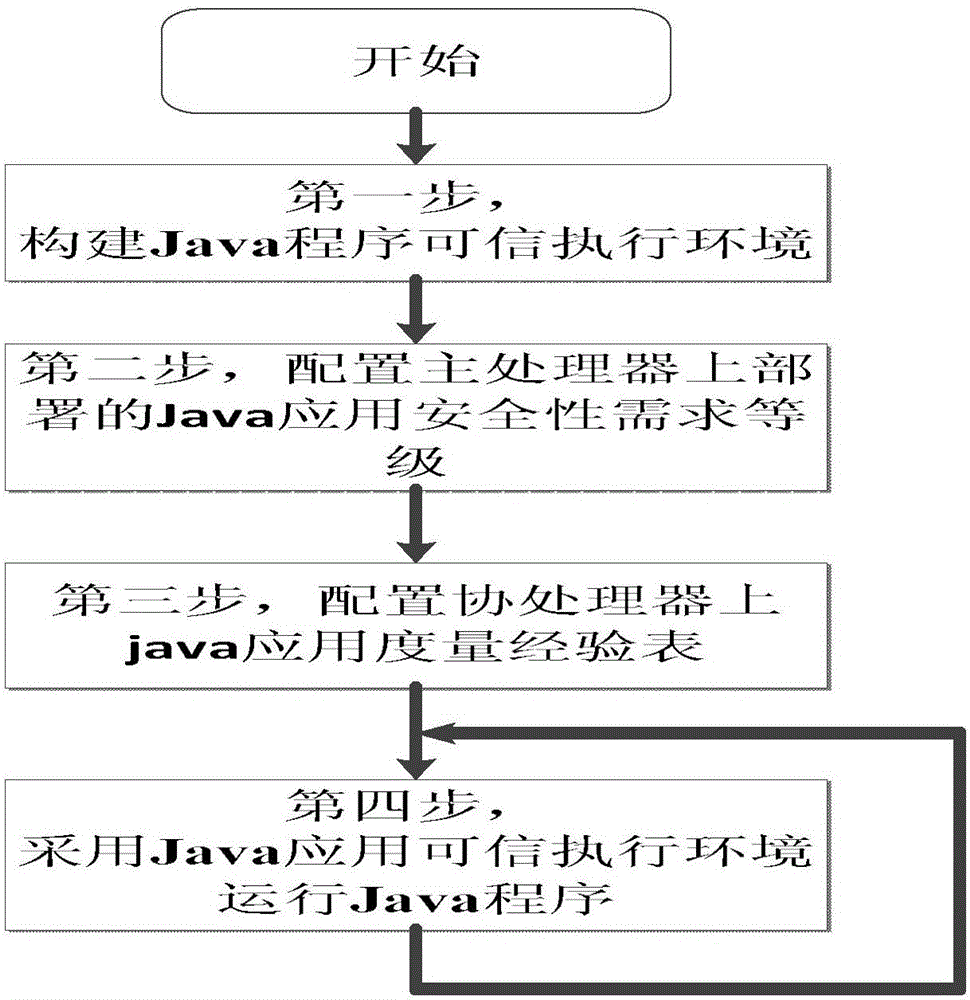
[0043] figure 1 Is the overall flow chart of the present invention; The present invention comprises the following steps:
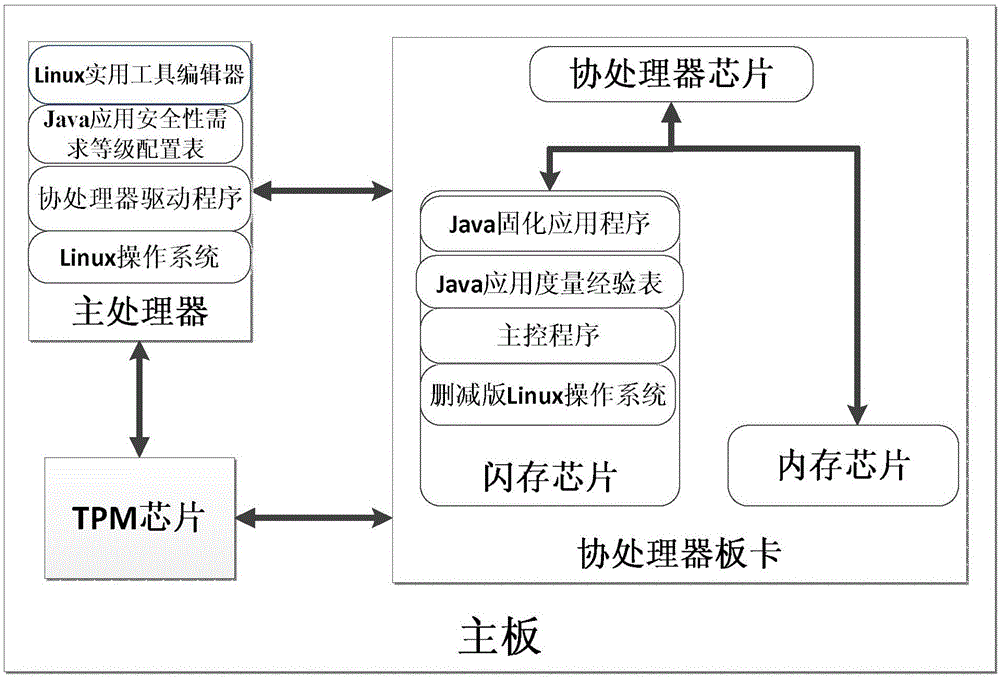
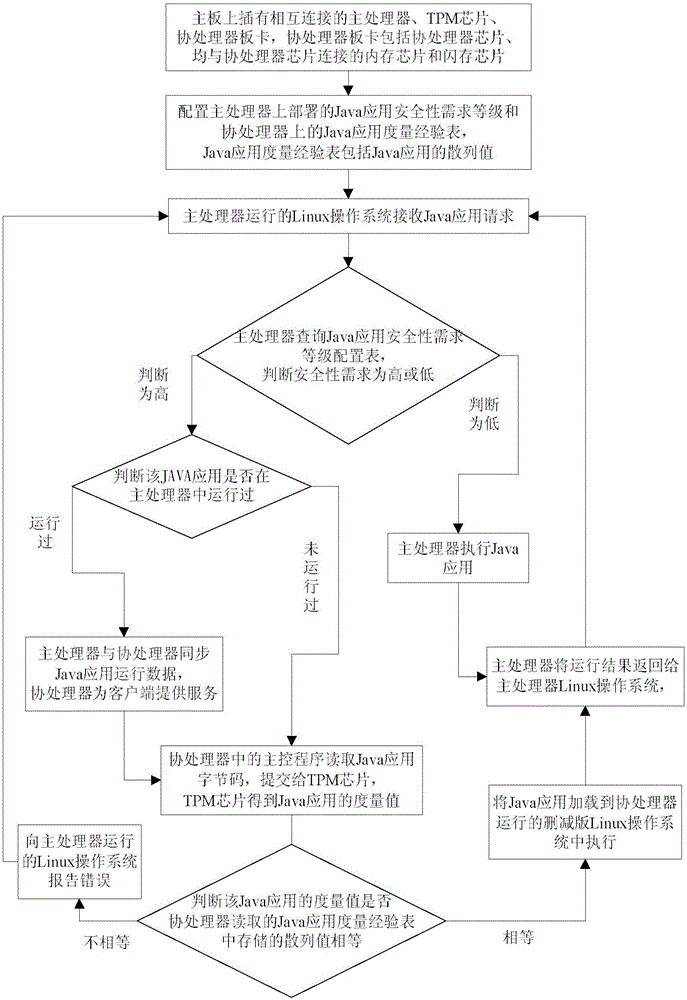
[0044] The first step is to build a Java program trusted execution environment. The Java program trusted execution environment is composed of a coprocessor board, a main processor, and a TPM chip. The coprocessor board, the main processor, and the TPM chip are all inserted into the motherboard. .
[0045] The memory chip requires more than 1GB of running memory, and the flash memory chip requires more than 4GB of solidified flash memory.
[0046] The second step is to configure the security requirement level of the Java application deployed on the main processor.
[0047] The third step is to configure the Java application measureme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com