Electronic data safekeeping system and method based on double and asymmetric encryption technology
An asymmetric encryption, electronic data technology, applied in the field of information security, can solve problems such as the inability to guarantee that the electronic data has not been tampered with, and the inability to guarantee that the electronic data has not been tampered with.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
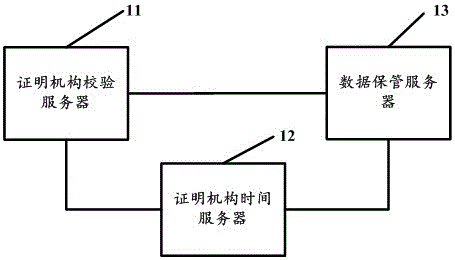
[0040] Embodiment 1 of the present invention provides an electronic data storage system based on double asymmetric encryption technology, such as figure 1 As shown, it is a schematic structural diagram of an electronic data storage system based on double asymmetric encryption technology according to Embodiment 1 of the present invention, including a certification authority verification server 11, a certification authority time server 12 and a data storage server 13;
[0041] The verification server 11 of the certification agency can be used to receive the electronic data submitted by the parties, and verify the received electronic data, request the time stamp from the certification agency time server 12 in real time, and calculate the electronic data and the time stamp. The combined MD5 value of the stamp is used to fix the electronic data to ensure that the electronic data submitted by the parties has not been tampered with, and the fixed electronic data and the time stamp are...
Embodiment 2
[0066] Based on the same inventive concept as that of Embodiment 1 of the present invention, Embodiment 2 of the present invention provides a method for storing electronic data based on double asymmetric encryption technology. For the electronic data storage system of technology, the specific implementation of this method can refer to the relevant description in the above-mentioned system embodiment one, and the repetition will not be repeated. The method mainly includes:
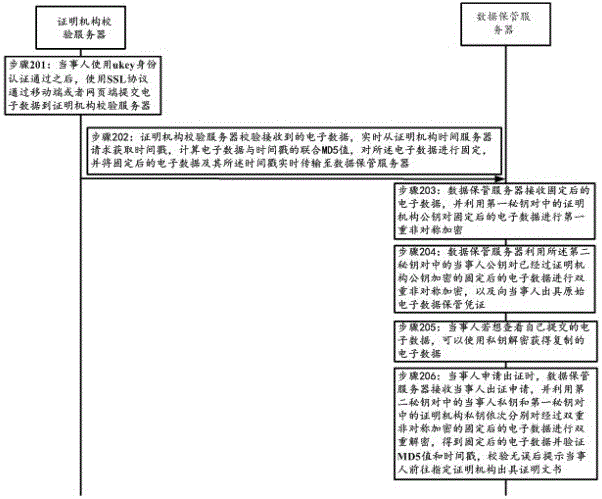
[0067] Step A1: The verification server of the certification authority receives the electronic data submitted by the party and verifies the received electronic data;
[0068] Step A2: request the time stamp from the time server of the certification authority in real time, calculate the joint MD5 value of the electronic data and the time stamp, and fix the electronic data;
[0069] Step A3: Transmitting the fixed electronic data and the time stamp to the data storage server in real time.
[0070] Further, t...
Embodiment 3
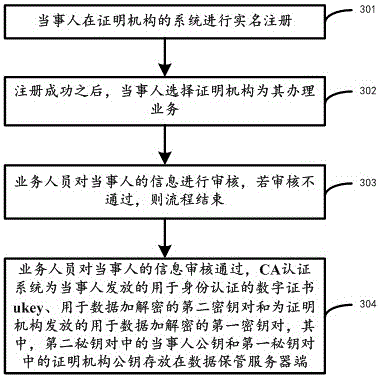
[0073]Based on the same inventive concept as that of Embodiment 1 of the present invention, Embodiment 3 of the present invention provides an electronic data storage method based on double asymmetric encryption technology. For the electronic data storage system of technology, the specific implementation of this method can refer to the relevant description in the above-mentioned system embodiment one, and the repetition will not be repeated. The method mainly includes:
[0074] The time server of the certification institution is synchronized with the external reference clock, and provides time stamp services for the verification server of the certification institution to ensure the reliability of the system time.
[0075] Further, the time server of the certification authority performs time synchronization with the external reference clock through the NTP protocol, and the time is accurate to milliseconds.
[0076] Embodiment 3 of the present invention provides an electronic da...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com