Chip authentication method, system, printer, consumable chip and consumable cartridge
A consumable chip, authentication method technology, applied in printing and other directions, can solve problems such as authentication method security loopholes, and achieve the effect of solving security loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
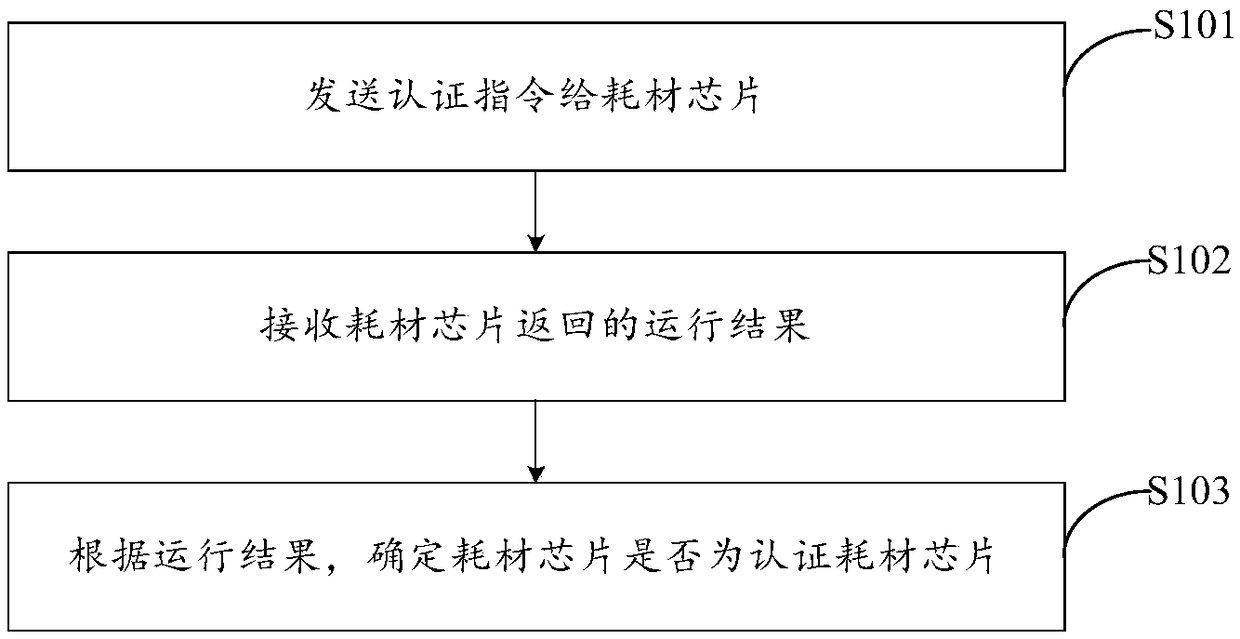
[0081] An embodiment of the present invention provides a chip authentication method, which is executed on a printer.
[0082] Specifically, please refer to figure 1 , which is a schematic flowchart of Embodiment 1 of the chip authentication method provided by the embodiment of the present invention, as shown in figure 1 As shown, the method includes the following steps:
[0083] S101. Send an authentication instruction to the consumable chip.
[0084] It should be noted that the authentication instruction includes a specified code, and the specified code is compiled according to the program compilation format of the authentication consumable chip.
[0085] In a specific implementation process, the authentication instruction may also include but not limited to: at least one of command, length, data and check.
[0086] S102, receiving the operation result returned by the consumable chip.
[0087] S103, according to the operation result, determine whether the consumable chip ...
Embodiment 2
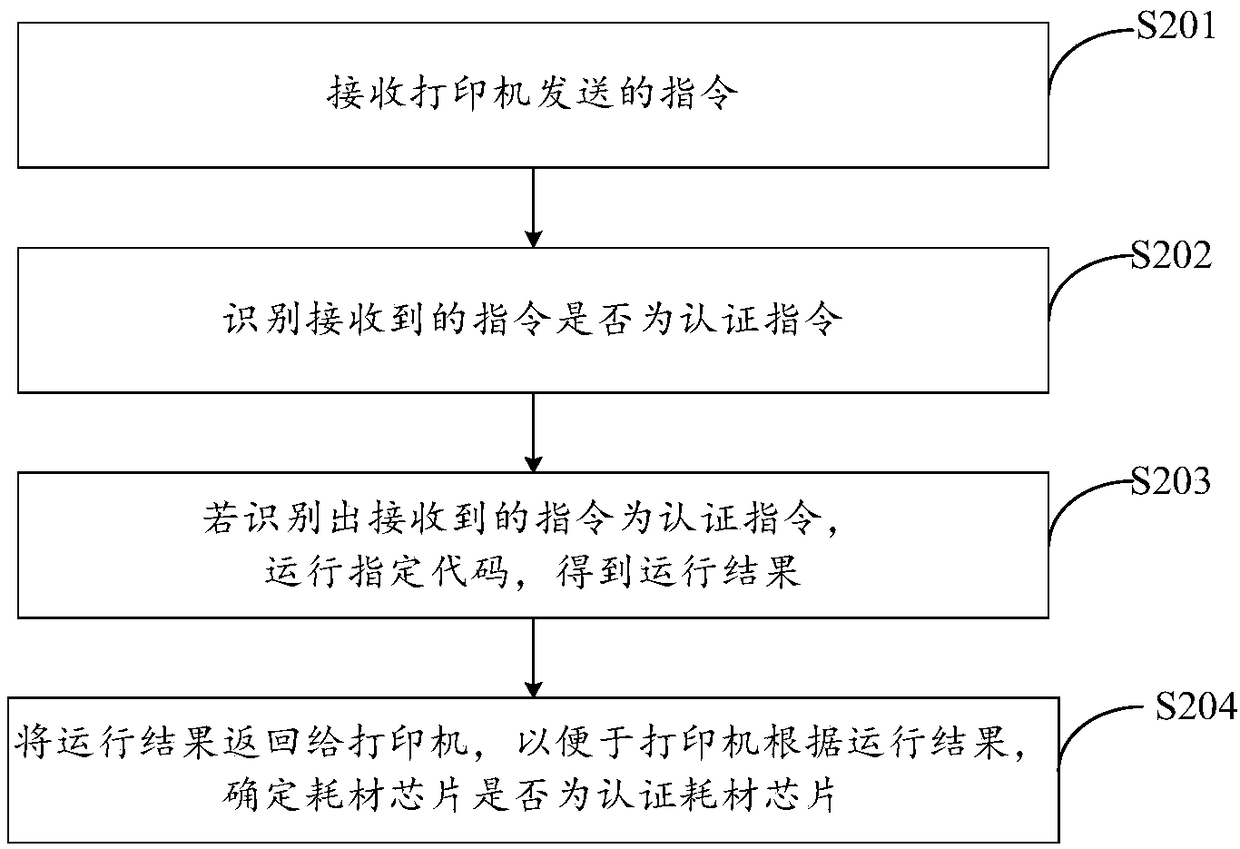
[0113] An embodiment of the present invention provides a chip authentication method, which is executed on a consumable chip.
[0114] Specifically, please refer to figure 2 , which is a schematic flowchart of Embodiment 2 of the chip authentication method provided by the embodiment of the present invention, as figure 2 As shown, the method includes the following steps:
[0115] S201. Receive an instruction sent by the printer.
[0116] S202. Identify whether the received instruction is an authentication instruction.
[0117] Specifically, the authentication instruction includes a specified code, and the specified code is compiled according to the program compilation format of the authentication consumable chip.
[0118] In a specific implementation process, the authentication instruction may also include but not limited to: at least one of command, length, data and check.
[0119] S203. If it is recognized that the received command is an authentication command, run a spe...
Embodiment 3
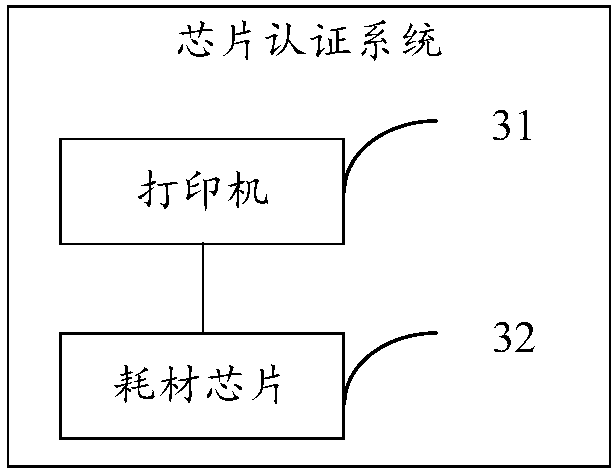
[0167] Based on the chip authentication method provided in the first embodiment above and the chip authentication method provided in the second embodiment above, an embodiment of the present invention provides a chip authentication system.
[0168] Specifically, please refer to image 3 , which is a functional block diagram of the chip authentication system provided by the embodiment of the present invention, such as image 3 As shown, the system includes:
[0169] The printer 31 is configured to send an authentication instruction to the consumable chip 32, the authentication instruction includes a specified code, and the specified code is compiled according to the program compilation format of the authentication consumable chip 32;
[0170] Consumables chip 32, configured to receive instructions sent by the printer 31;
[0171] The consumables chip 32 is also used to identify whether the received instruction is an authentication instruction;
[0172] The consumable chip 32...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com