Routing method for wireless sensor network based on LEACH protocol
A wireless sensor, network technology, applied in network topology, wireless communication, advanced technology and other directions, can solve the LEACH protocol security vulnerabilities and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
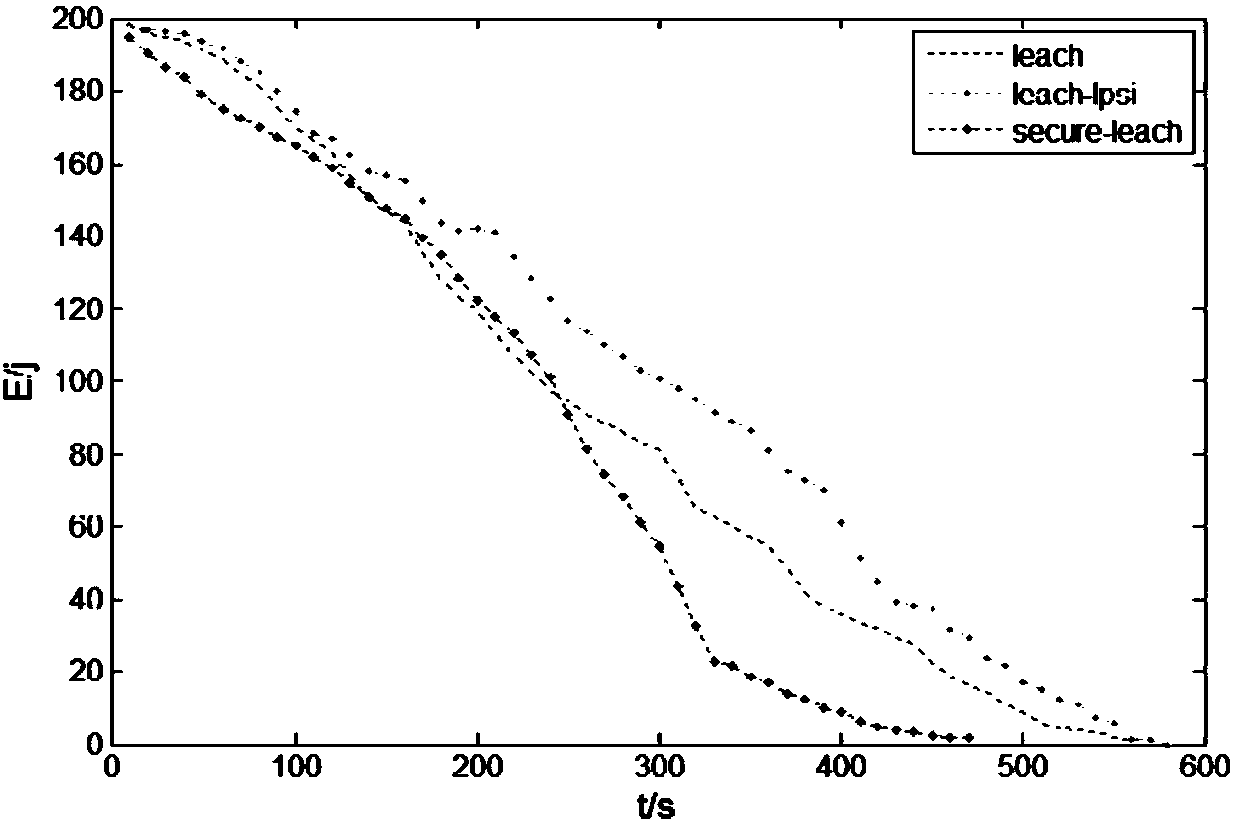
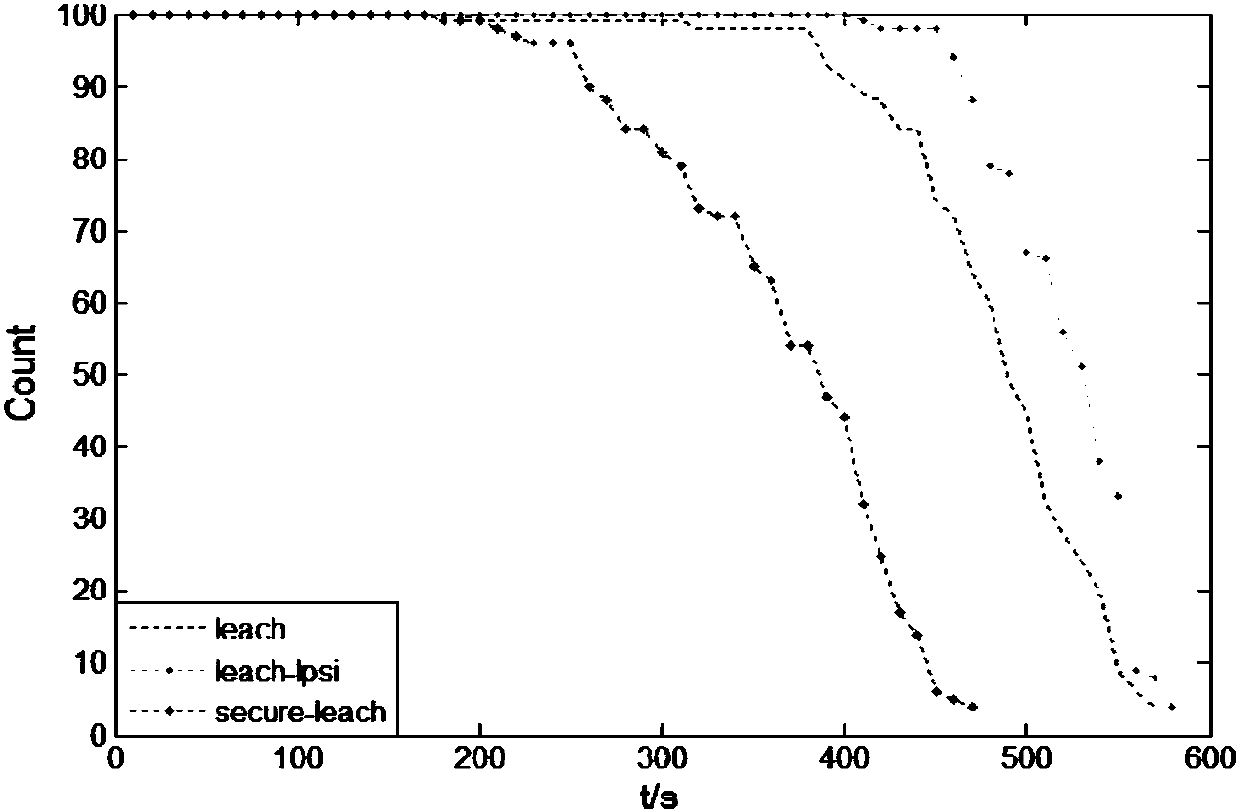
Method used
Image
Examples
Embodiment
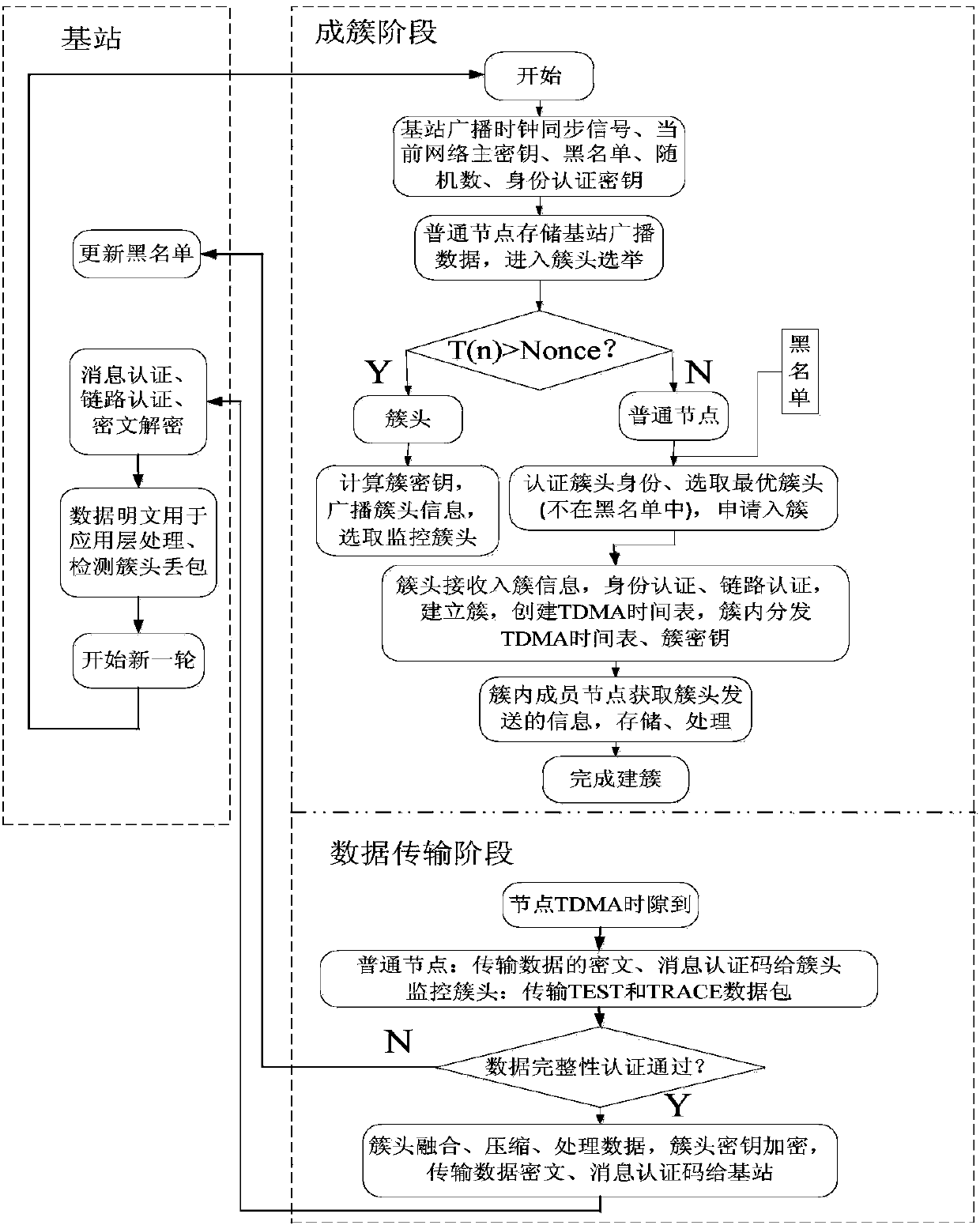
[0119] like figure 1 As shown, in this embodiment, a wireless sensor network routing method based on the LEACH protocol, the steps are as follows:
[0120] S1. Initial deployment of all nodes in the entire network; the initial deployment includes the generation of base station key chains, the distribution of node identities in the entire network, and the storage of symmetric key security algorithms.
[0121] S2. Enter the authentication broadcast stage: the base station broadcasts data including security control information to the entire network and periodically updates the security control information. The security control information includes a random number, and the node obtains the security control broadcast by the base station After the information is sent, the correctness of the security control information is verified, and the currently stored security control information is updated after the verification; after the authentication broadcast stage ends, step S3 is entere...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com