Data sharing control method based on block chain
A control method and data sharing technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of inconvenient management, increased data leakage, decentralization, etc., and achieve the effect of fast authentication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] This embodiment discloses a blockchain-based data sharing control method. In the case of no conflict or contradiction, the whole and / or part of the preferred implementations of other embodiments can be used as a supplement to this embodiment.
[0040] Common terms in this invention:
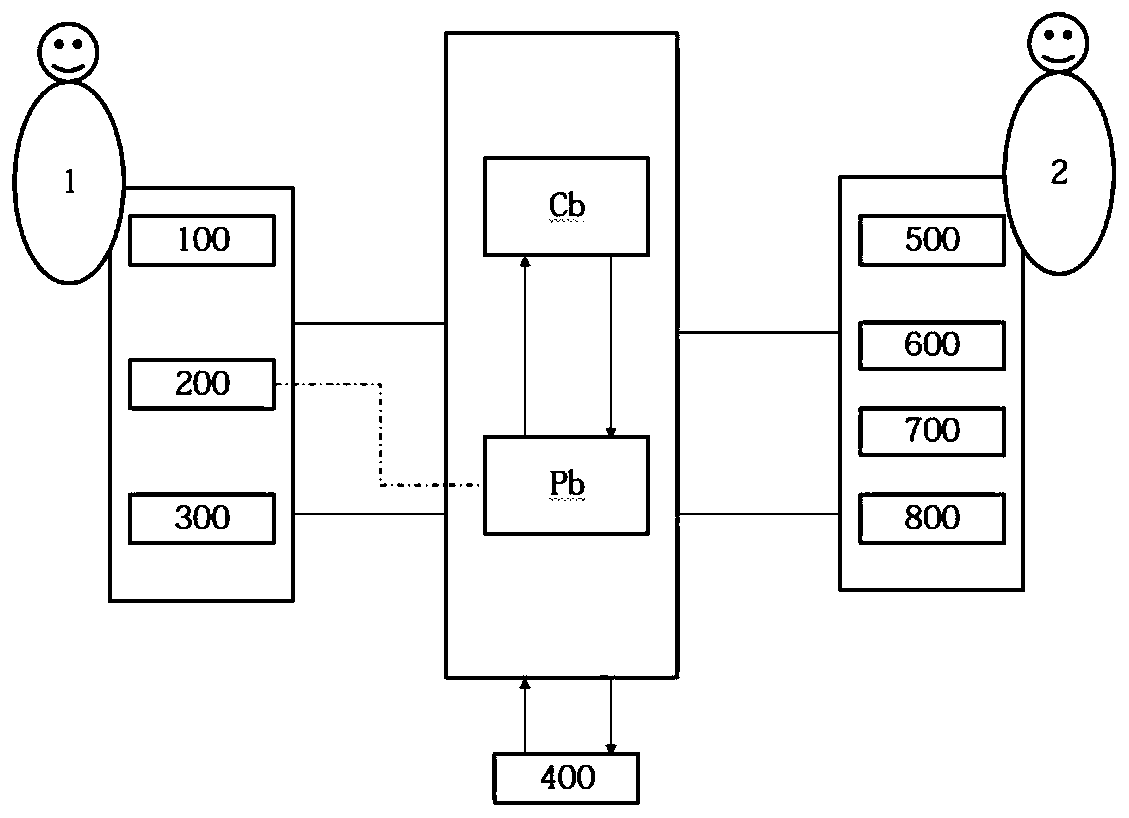
[0041] Data Owner 1 (Data Owner): The data sharing party can encrypt the data to be shared, create a private chain (control access to the data to be shared) and generate a private chain index file according to the attributes of the User. For example, data holder 1 can be a major securities firm, a hospital or a non-governmental organization.
[0042] Data visitor 2, (User): The party to whom the data is shared can download the shared data and need to obtain the ciphertext uploaded by the holder 1 to the private chain to use, view or change the shared data resource. For example, data visitor 2 could be a patient or a bank customer.
[0043] Private chain Pb: Refers to the blockchain whose...
Embodiment 2
[0064] This embodiment may be a further improvement and / or supplement to Embodiment 1, and repeated content will not be repeated here. In the case of no conflict or contradiction, the whole and / or part of the content of the preferred implementations of other embodiments may serve as supplements to this embodiment.
[0065] Such as figure 2 As shown, the data sharing control method specifically includes the following two steps: a data upload control step S1 and a data download control step S2.
[0066] The data upload control step S1 includes:
[0067] S11: Data holder 1 encrypts data resources that need to be shared.
[0068] S12: Data holder 1 creates a private chain Pb in the blockchain network.
[0069] S13: After the private chain Pb is created, the data holder 1 can generate an index file according to the attributes of the data visitor who needs to obtain the data resource.
[0070] S14: The data holder 1 packages the encrypted shared data resource together with the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com