Integration encrypted storage tamper-proofing method and system
An encrypted storage and anti-tampering technology, which is applied in transmission systems, instruments, electrical digital data processing, etc., can solve the problems of personal privacy impact, data leakage, data tampering, etc., to improve storage efficiency, reduce calculation times, and reduce storage effect of space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
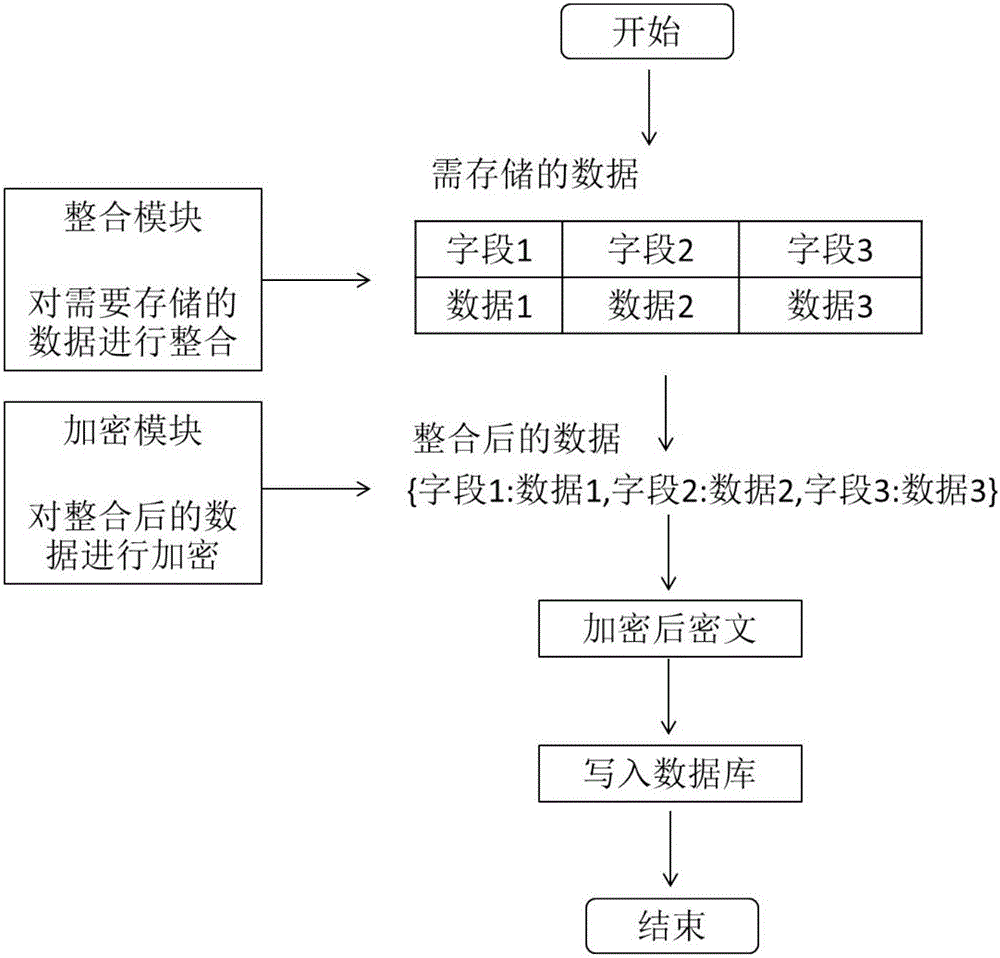
[0042] In one aspect, the present invention provides a tamper-proof method for integrated encrypted storage, the method comprising:
[0043] S1. Integrate multiple fields in the original data into one field according to preset integration rules;
[0044] S2. Read the encryption key, encrypt the integrated fields, and store the encrypted data in the database.
[0045] In a specific implementation, multiple fields are integrated and encrypted to reduce storage space and improve storage efficiency. Before encryption, the multi-fields that need to be stored are integrated into one field in a certain format. After the integrated fields are encrypted as a whole, the ciphertext is stored in the database. Although there are multiple fields to be stored, only one encryption calculation and one storage space are required. Thereby greatly reducing the number of encryption calculations, reducing storage space, and improving storage efficiency.
[0046] Preferably, the method also incl...
Embodiment 2
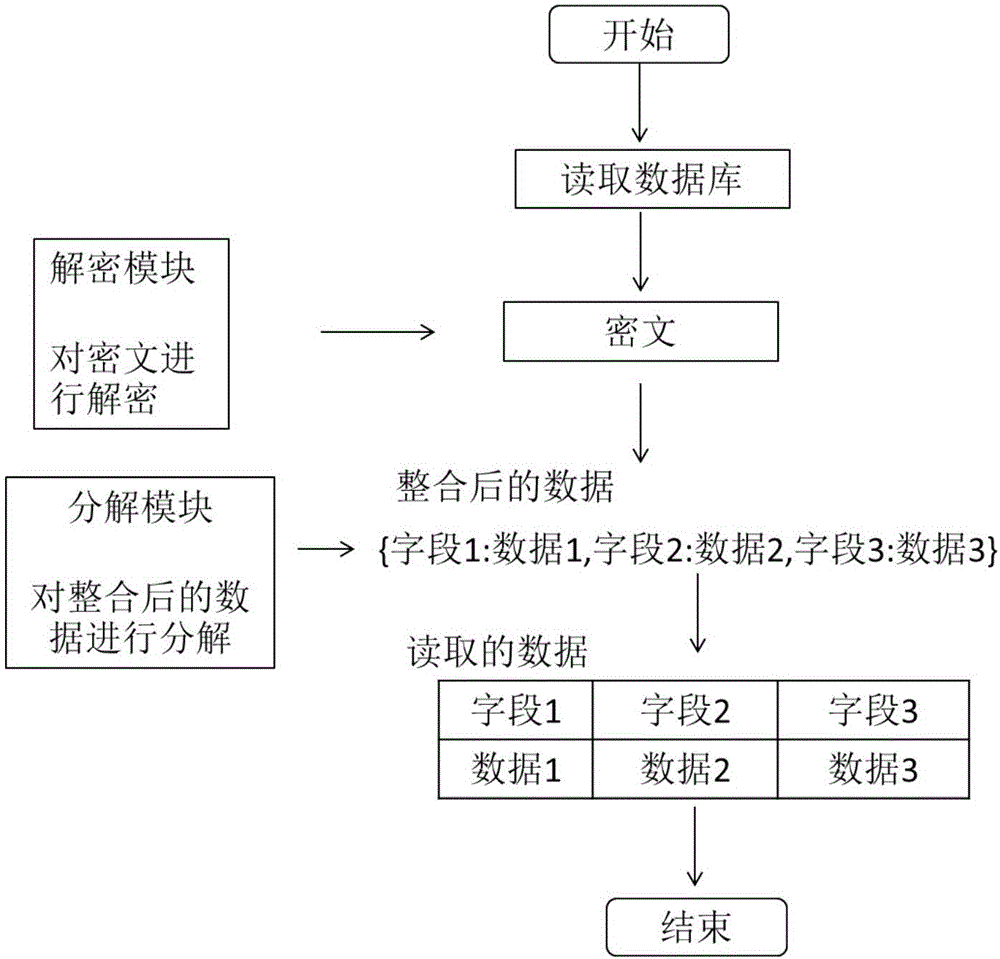
[0073] The decryption process is the inverse process of the above encryption process. Preferably, the decryption process is: first read the encrypted ciphertext, and then decrypt it from the ciphertext, so as to obtain the decrypted integrated fields. Then according to the integration rules, the data information corresponding to each field is read. Moreover, information such as fields and data cannot be found from the ciphertext. Therefore, in this method, the stored data information can be prevented from being tampered with.
[0074] In a specific embodiment, the data reading process of the present invention is as follows:
[0075] a) After the method starts, read out the stored ciphertext
[0076] b) Use the decryption module to decrypt the data in step a). In order to obtain the data in JSON format. An example of its decryption module function is as follows:
[0077] The first step is to read the decryption key in the decryption module.
[0078] In the second part, ca...
Embodiment 3
[0091] On the other hand, the present invention also provides a tamper-proof system for integrated encrypted storage, which is applied to the encryption of database data. The system includes: an integration module, an encryption module, a decryption module, and a decomposition module;
[0092] The integration module is used to integrate multiple fields of the original data into one field to obtain data to be encrypted;
[0093] The encryption module is used to encrypt the data to be encrypted;
[0094] The decryption module is used to decrypt the encrypted data stored in the database when reading encrypted data, and obtain the data to be encrypted;
[0095] The decomposing module is configured to decompose the data to be encrypted obtained after decryption into a plurality of fields to obtain original data.
[0096] In the two processes, four functional modules are involved - integration module, encryption module, decryption module and decomposition module. Its corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com