Digital chaotic encryption method based on chaotic number spectrum
A chaotic encryption and encryption method technology, applied in the field of information security, can solve problems such as difficulty in adapting to computer data encryption, and achieve the effect of superior security and confidentiality performance and information processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
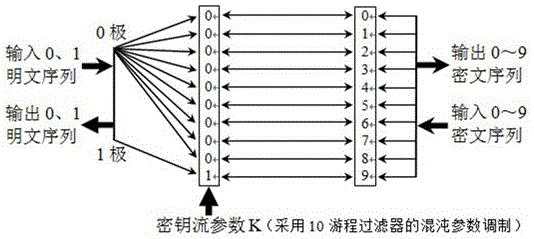
[0062] Such as figure 1 Shown, a kind of digitized chaos encryption method based on chaotic number spectrum, described encryption method comprises the following steps:
[0063] Step 1: Send encoded plaintext data, and convert the plaintext data into binary array code 01;
[0064] Step 2: Discretize and map the binary array code 01 obtained in Step 1 into chaotic code 0000011111;
[0065] Step 3: The chaotic code 0000011111 obtained in Step 2 is fuzzified and mapped into a serial number code 0123456789;
[0066] Step 4: Encode the serial number 0123456789 obtained in Step 3 to construct ciphertext data 0-9;
[0067] Step 5: The ciphertext data 0-9 obtained in Step 4 is transmitted to the receiver through an open channel.
[0068] Wherein, there is also step six: inverting the ciphertext data obtained in step five into serial number codes.
[0069] Among them, there is also a step seven, which is to reversely map the serial number code in step six into a chaotic code.
[0070...
Embodiment 2
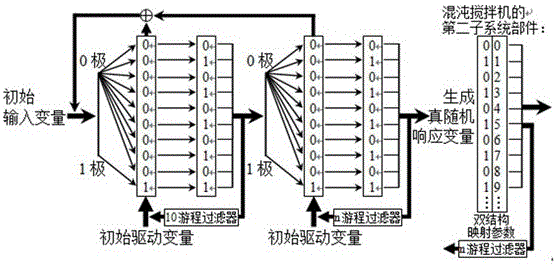
[0073] Such as figure 2 As shown, the method of this embodiment lies in the dual-system chaotic key stream generator, which is suitable for synchronous communication schemes in real-time signal processing occasions, and has basically the same secure communication functions and application fields as modern serial ciphers.
[0074] A kind of digital chaos encryption method based on chaos number spectrum, described encryption method comprises the steps:
[0075] Step 1: Send the coded plaintext sequence, and convert the plaintext sequence into binary array code 01;
[0076] Step 2: Discretize and map the binary array code 01 obtained in Step 1 into chaotic code 0000000001;
[0077] Step 3: The chaotic code 0000011111 obtained in Step 2 is fuzzified and mapped into a serial number code 0123456789;
[0078] Step 4: Encoding the serial number obtained in Step 3 0123456789 to construct a ciphertext sequence 0-9;
[0079] Step five: transmit the ciphertext sequence 0-9 obtained in...
Embodiment 3
[0088] see image 3 , a kind of digital chaos encryption method based on chaos number spectrum, described encryption method comprises the following steps:
[0089] Step 1: Send encoded plaintext data, and convert the plaintext data into a binary array code, such as 0101010101;
[0090] Step 2: The binary array code obtained in step 1 is sequentially mapped into the first-level chaotic code 0000000001 through the first-level discretization, and then fuzzy-mapped into the first-level serial number code 0101010101 through the n(10) run filter;
[0091] Step 3: The serial number code 0101010101 obtained in step 2 is mapped into the second-level chaotic code 0000000001 through the second-level discretization, and then fuzzy mapped into the second-level serial number code 0101010101 through the n(10) run filter;
[0092] Step 4: Encode the second-level sequence number obtained in Step 3 to construct ciphertext data through the chaos mixer;
[0093] Step 5: The ciphertext data obta...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com