BMC U-boot trusted starting control method
A boot control and trusted technology, applied in the field of BMCU-boot trusted boot control, can solve problems such as program tampering and integrity damage, and achieve the effect of improving core competitiveness, strong practicability, and easy promotion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
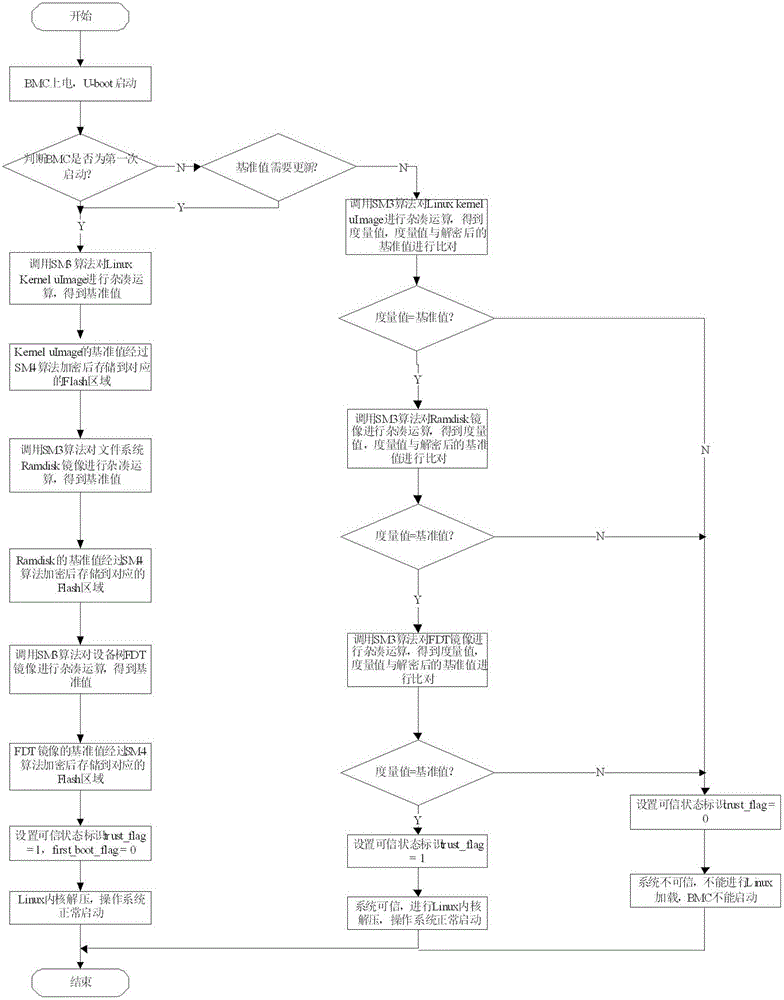
[0023] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
[0024] as attached figure 1 Shown, the present invention proposes that the present invention proposes a kind of method that realizes BMC U-boot credible start-up control, has adopted domestic SM3, SM4 cryptographic algorithm, in U-boot start guide system process, to Linux kernel mirror image, file system mirror image and The device tree image is used to measure and judge the trusted state to ensure the integrity of the program, and finally establish a trusted execution environment for the BMC system platform.
[0025] In this method step, my country's commercial cryptographic algorithms SM3 and SM4 are used, SM3 is a cryptographic hash algorithm, and SM4 is a symmetric cryptographic algorithm, and the combination of the two algorithms can ensure the security of the system;
[0026] During the startup process of BMC U-boot, the trusted function...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com