Lightweight file remote encryption method under mobile cloud computing environment
A computing environment, encryption method technology, applied in the computer field
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
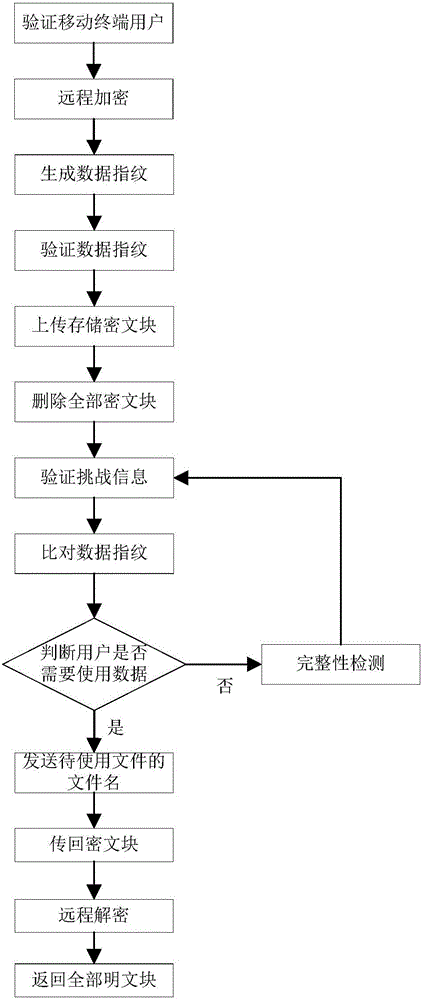
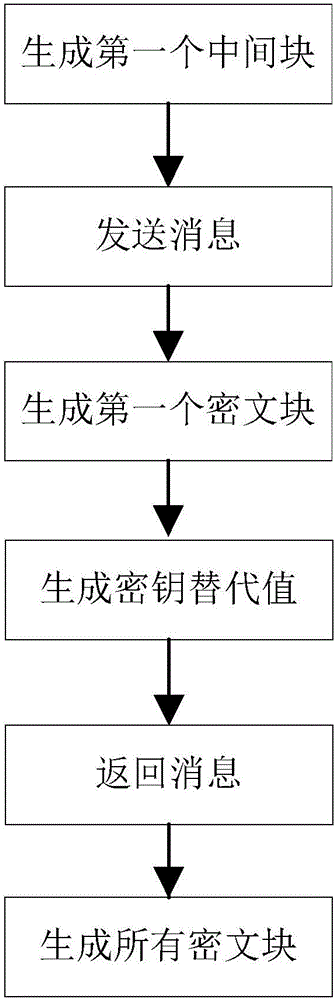
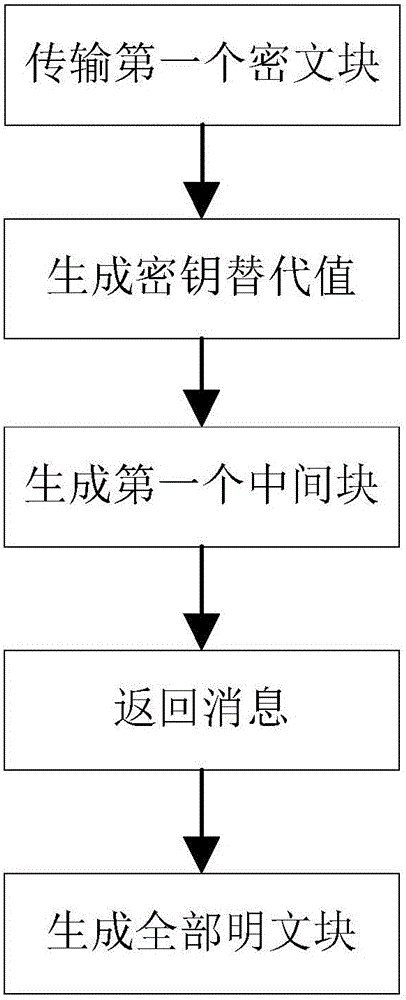
[0093] The present invention will be further described below in conjunction with the accompanying drawings.
[0094] Refer to attachedfigure 1 , to further describe the specific steps for realizing the present invention.
[0095] Step 1, verify the mobile terminal user.
[0096] Using the user authentication method, the private cloud authenticates the mobile terminal user.
[0097] The specific steps to implement the user authentication method are as follows:
[0098] Step 1, the mobile terminal sends the mobile terminal user identification code ID, password psd, the file name fn of the file to be encrypted, the privacy level PrivLevel and the time stamp t of the file to be encrypted 1 Encrypt with the public key of the private cloud, and send the encrypted message to the private cloud.
[0099] In the second step, the private cloud decrypts the received message with its own private key, and obtains the mobile terminal user identification code ID and password psd.
[0100]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com