Attribute encryption scheme for cipher text having equal comparability
A technology of attribute encryption and ciphertext, which is applied in the field of attribute encryption scheme and cryptography, which can solve the problems of inconvenient storage structure and achieve the effect of ensuring security and reducing public key management and verification overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
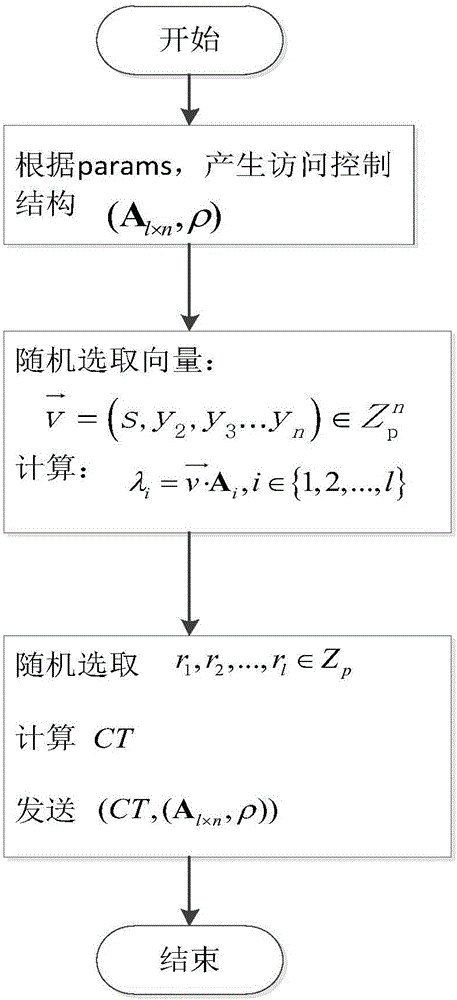
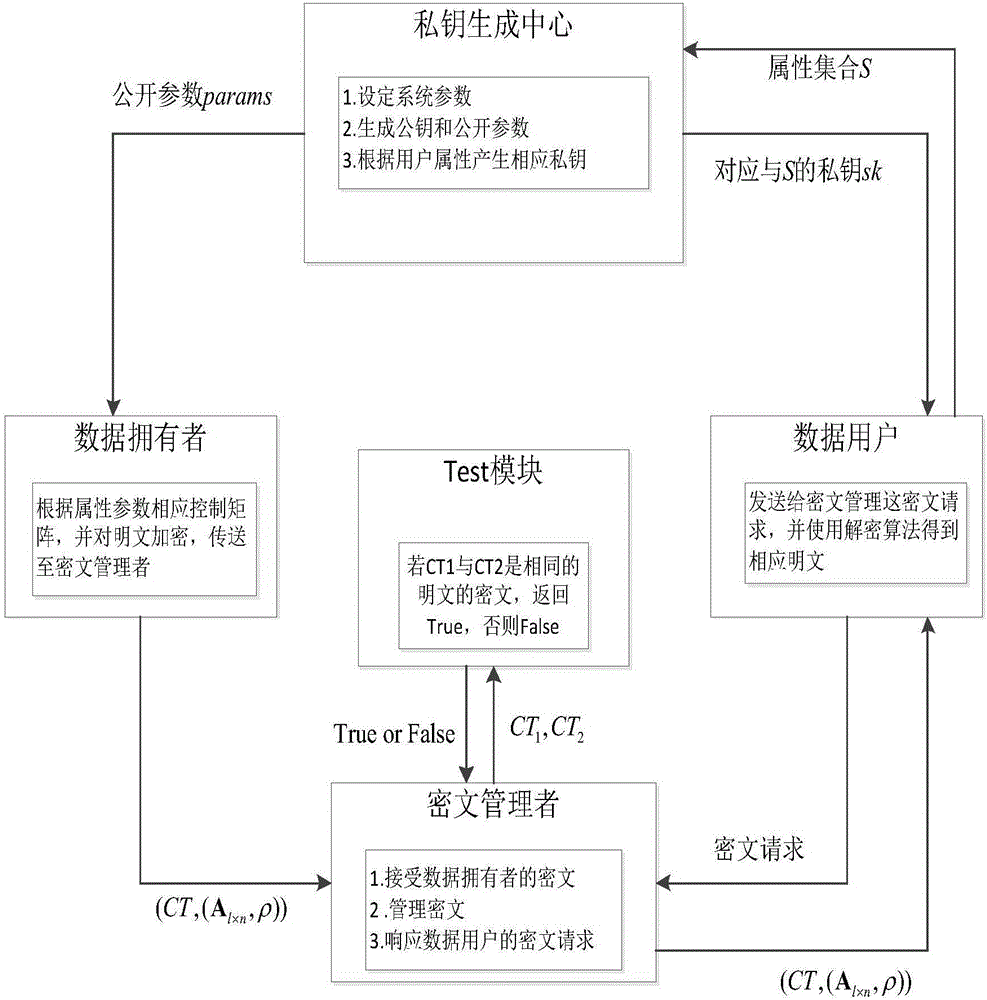
[0023] see image 3 , the specific execution steps include setting the system security parameters, key space, message space, and public parameters by the private key generation center, and generating the public key in the attribute set. The specific description is as follows:
[0024] (1) System initialization
[0025] (1.1) Let the system security parameter be λ, p be a large prime number, G 1 Represents a cyclic additive group of order p, g∈G 1 means G 1 generator, G 2 Represents a cyclic multiplicative group of order p. e represents the bilinear map G 1 ×G 1 →G 2 . Define a safe Hash function H, H means from G 2 map to G 1 A secure hash function for U elements h representing user attributes 1 ,h 2 ,...,h u ∈G 1 . The user private key key space is K∈G 1 , the encrypted message space is G 1 . Denotes a finite field Z p = {0,1,...,p-1} The set obtained by removing zero elements.
[0026] (1.2) The private key generation center is randomly selected Calcul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com