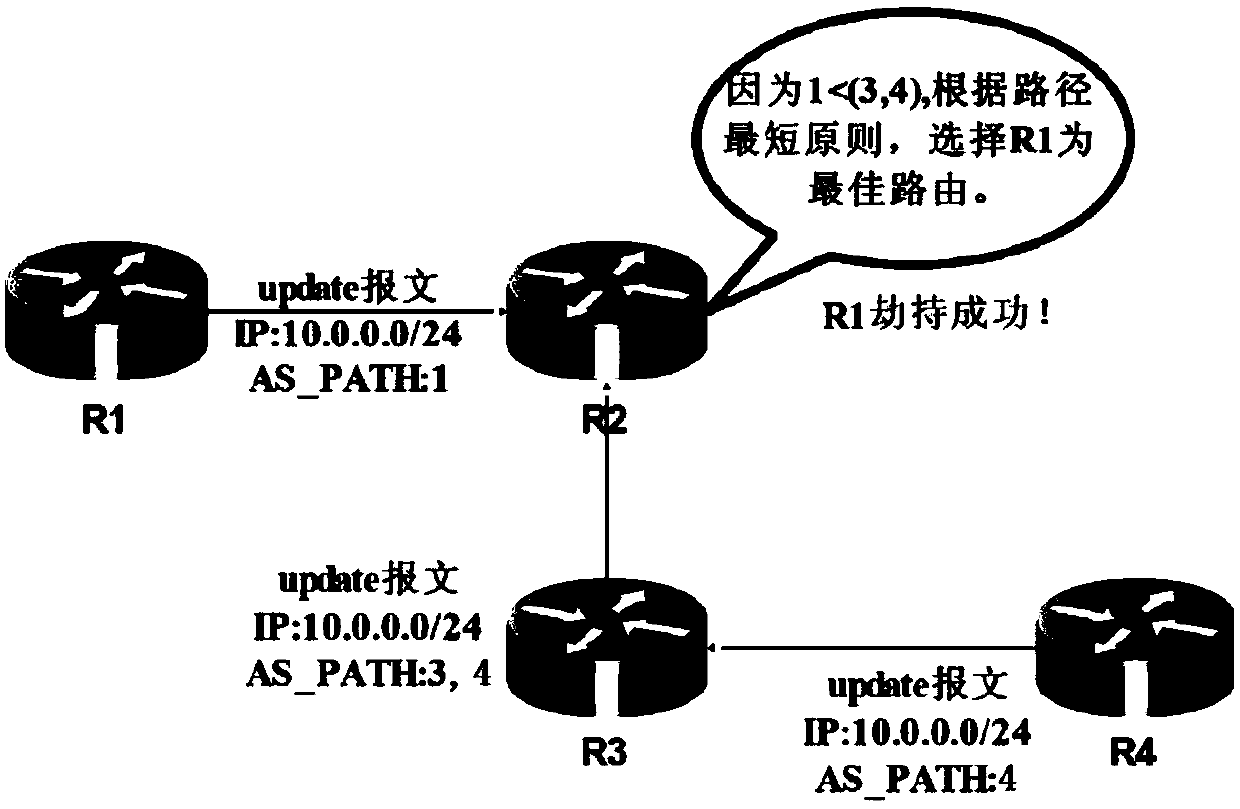
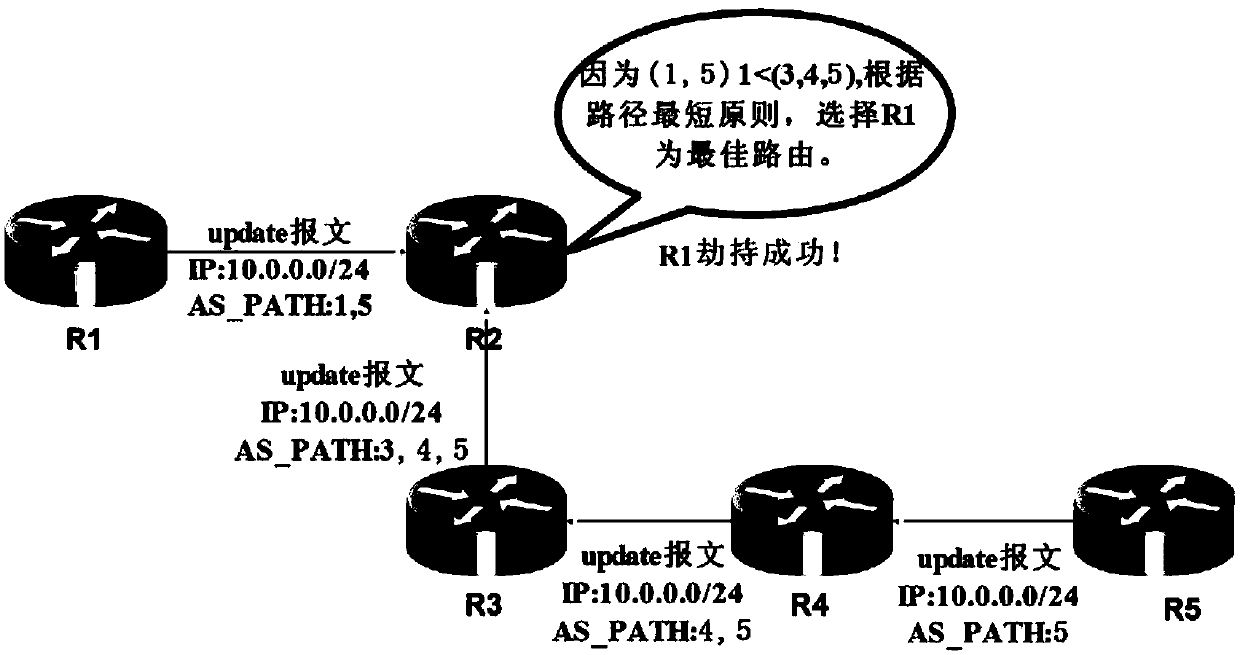
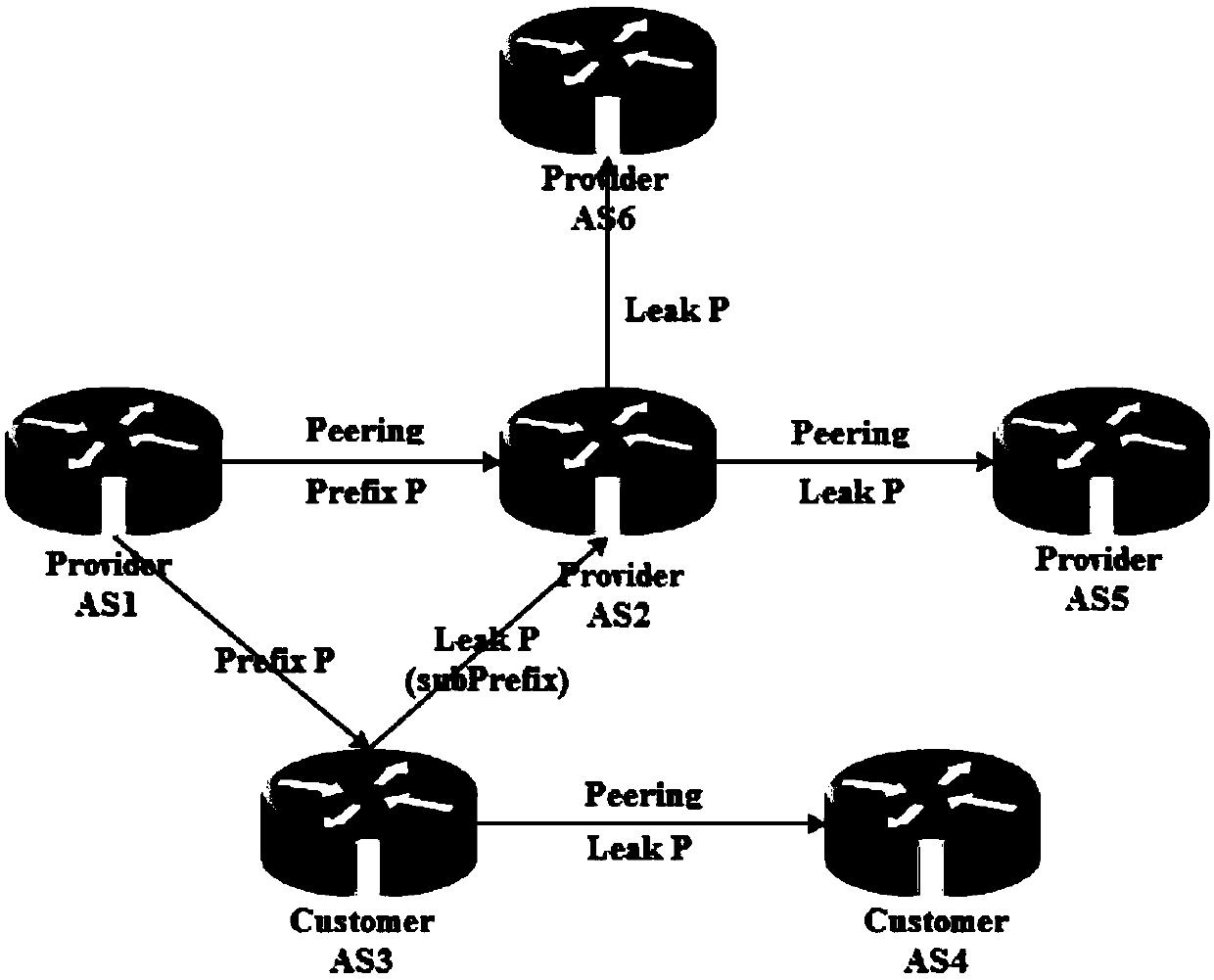
A method to simultaneously solve prefix hijacking, path hijacking and route leaking attacks
A routing and prefix technology, applied in the field of computer networks, can solve problems such as route leakage attacks, reduce usage, reduce routing load overhead, and prevent AS_PATH path hijacking attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] In order to make the above objects, features and advantages of the present invention more obvious and understandable, the present invention will be further described below through specific embodiments and accompanying drawings.
[0053] The invention improves the RPKI data synchronization scheme, extends the ASPolicyCert certificate format in the soBGP mechanism, and then effectively combines the two, thereby proposing a method that can simultaneously solve prefix hijacking, AS_PATH path hijacking, and route leakage attacks way of the problem.
[0054] For the current RPKI data synchronization scheme, the flow of the improved scheme designed by the present invention is as follows Image 6 Shown:
[0055] (1) Router R1 applies for an ROA certificate from the RP.
[0056] (2) R1 attaches the ROA certificate to the update message as part of the path attribute of the update message.
[0057] (3) R1 sends the update message containing the ROA certificate to the peer route...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com