Random encryption physical information block chain anti-counterfeiting method, system and device
A technology of physical information and random encryption, applied in the field of anti-counterfeiting, it can solve the problems of not taking the authentication carrier, forging authentication information, counterfeiting, and disconnecting authentication information.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
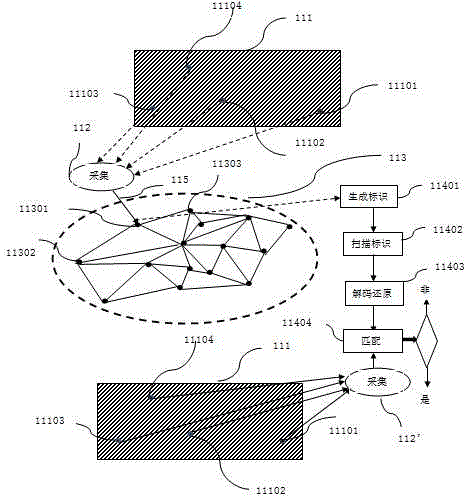
[0313] Such as figure 1 , 2 As shown, randomly collect specific physical information 11101, specific physical information 2 11102, specific physical information 3 11103, and specific physical information 4 11104 of the object 111 to be verified randomly, and transmit and store the above specific physical information in node 1 11301. Node 1 11301 Save the record and generate the identification 11401, the identification 11401 is placed on the object 111 to be verified, and the verifier decodes the scanned identification 11402 to restore 11403, and the specific physical information 11101, specific physical information 2 11102, Specific physical information 3 11103 and specific physical information 4 11104 are matched to identify authenticity.
[0314] The specific physical information 11101, the specific physical information 2 11102, the specific physical information 3 11103, and the specific physical information 4 11104 include the physical information of the specific area of ...
Embodiment 2
[0324] Such as image 3 , 4 As shown, the currency to be verified 121 is randomly collected specific physical information 1 12101, specific physical information 2 12102, specific physical information 3 12103, and specific physical information 4 12104, and the above specific physical information is transmitted and stored in node 12301, and the node 12301 Save the record and generate the identification 12401, the identification 12401 is placed in the currency 121 to be verified, and the verifier decodes and restores the identification 12403 by scanning the identification 12402, and the specific physical information 12101, Specific physical information 2 12102, specific physical information 3 12103, and specific physical information 4 12104 are matched to identify authenticity.
[0325] The specific physical information 12101, specific physical information 2 12102, specific physical information 3 12103, and specific physical information 4 12104 include currency one 121 specific ...
Embodiment 3
[0335] Such as Figure 7 , 8 As shown, the specific physical information 1 13101, specific physical information 2 13102, specific physical information 3 13103, and specific physical information 4 13104 of the bill 131 to be verified are randomly collected, and the above specific physical information is transmitted and stored in the node 13301, and the node 13301 saves Record and generate the identification 13401, the identification 13401 is placed on the bill 131 to be verified, and the verifier decodes and restores the identification 13403 by scanning the identification 13402, and the specific physical information 13101 and the specific physical information 2 13102 of the bill 131 to be verified , specific physical information 3 13103, specific physical information 4 13104, match and identify authenticity.
[0336] The specific physical information 13101, the specific physical information 2 13102, the specific physical information 3 13103, and the specific physical informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com