Method for encrypting SSR password
A password and user password technology, which is applied to encryption devices with shift registers/memory and key distribution, can solve problems such as insecurity, achieve the effect of preventing brute force cracking and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0022] A method for implementing SSR password encryption, characterized in that: the method uses salt value encryption and iteration count encryption, wherein salt value encryption refers to adding a salt value before the user password, and this value is randomly generated by the system. Only the system knows, and then MD5 encrypts the combination of the salt value and the password, so that hackers cannot determine the password even if they query the hash value dictionary; the iteration count algorithm is an iterative digest algorithm that continues to repeatedly generate the digest generated for the first time The summary is to perform count times of MD5 operations, which can effectively prevent hackers from brute force cracking. Greatly improved the security of password encryption.
Embodiment 2
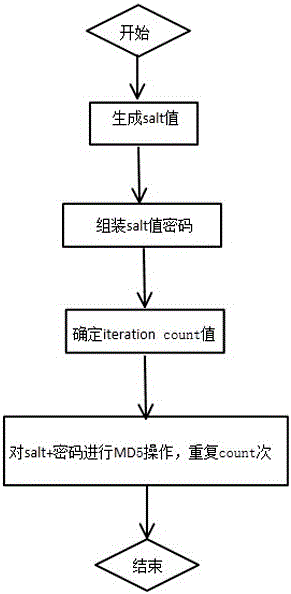
[0024] Such as figure 1 As shown, on the basis of embodiment 1, the method operation steps described in this embodiment are as follows:
[0025] Step 1: Generate a salt value. There is a different salt for each user. Record the corresponding relationship between the user name and the salt in the database. Using the randomly generated salt can effectively avoid "Birthday attacks (Birthday attacks, another type commonly used by hackers) means of attack)”;
[0026] Step 2: Receive the user password, and add the salt value generated in the first step before the password;
[0027] The third step: determine the iteration count value;
[0028] Step 4: Perform MD5 operation on the salt+password generated in the second step, and repeat this operation count times.
[0029] Step 5: Store the encrypted password ciphertext.
Embodiment 3
[0031] On the basis of Embodiment 1 or 2, the count value in this embodiment is 1000, and the salt value is 80bit characters.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com