A network configuration method, related device and system
A technology for network configuration and configuration information, applied in the field of communication, can solve the problems of being unable to resist active attacks, low universality, and high requirements for terminal processing capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
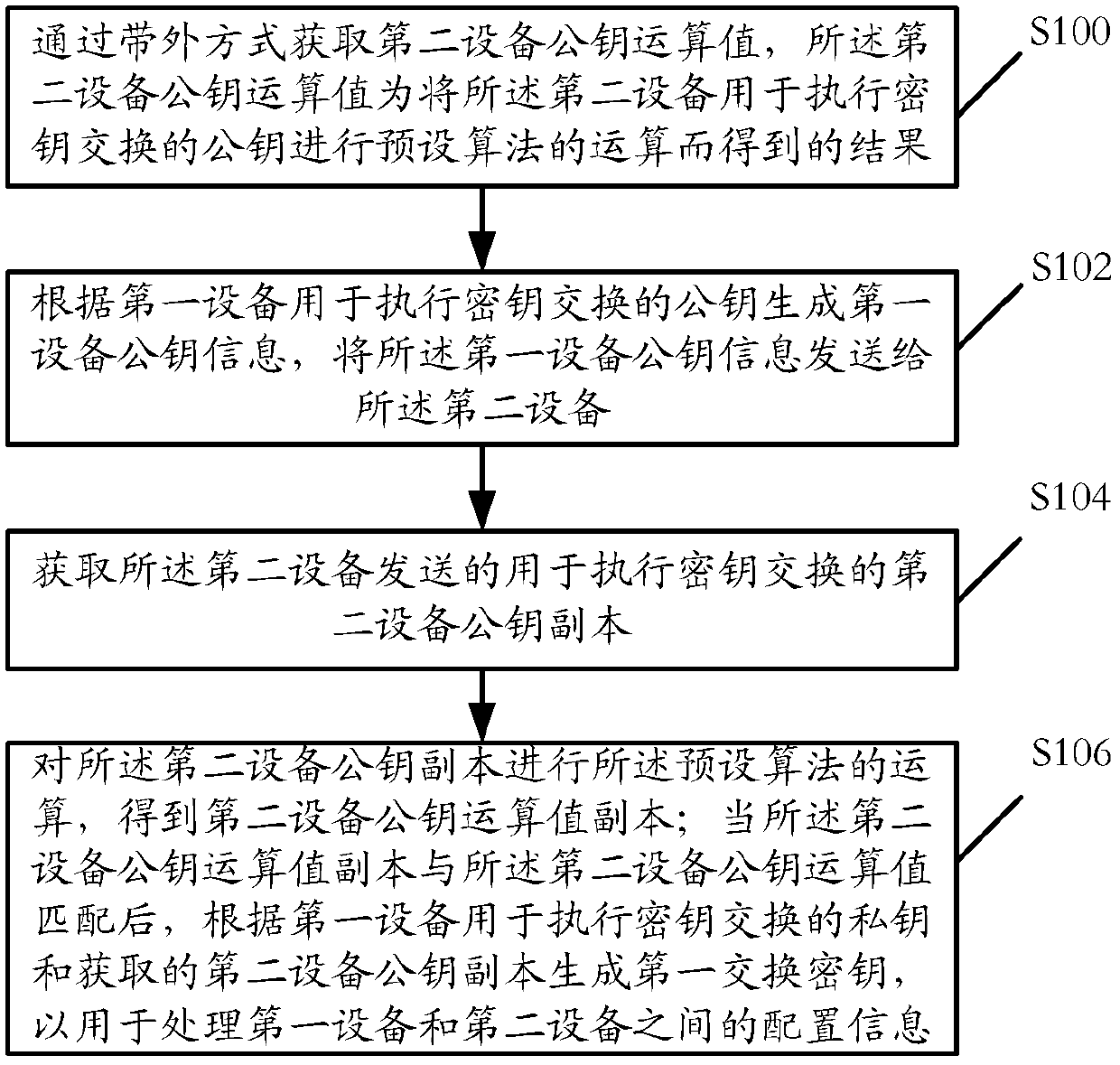
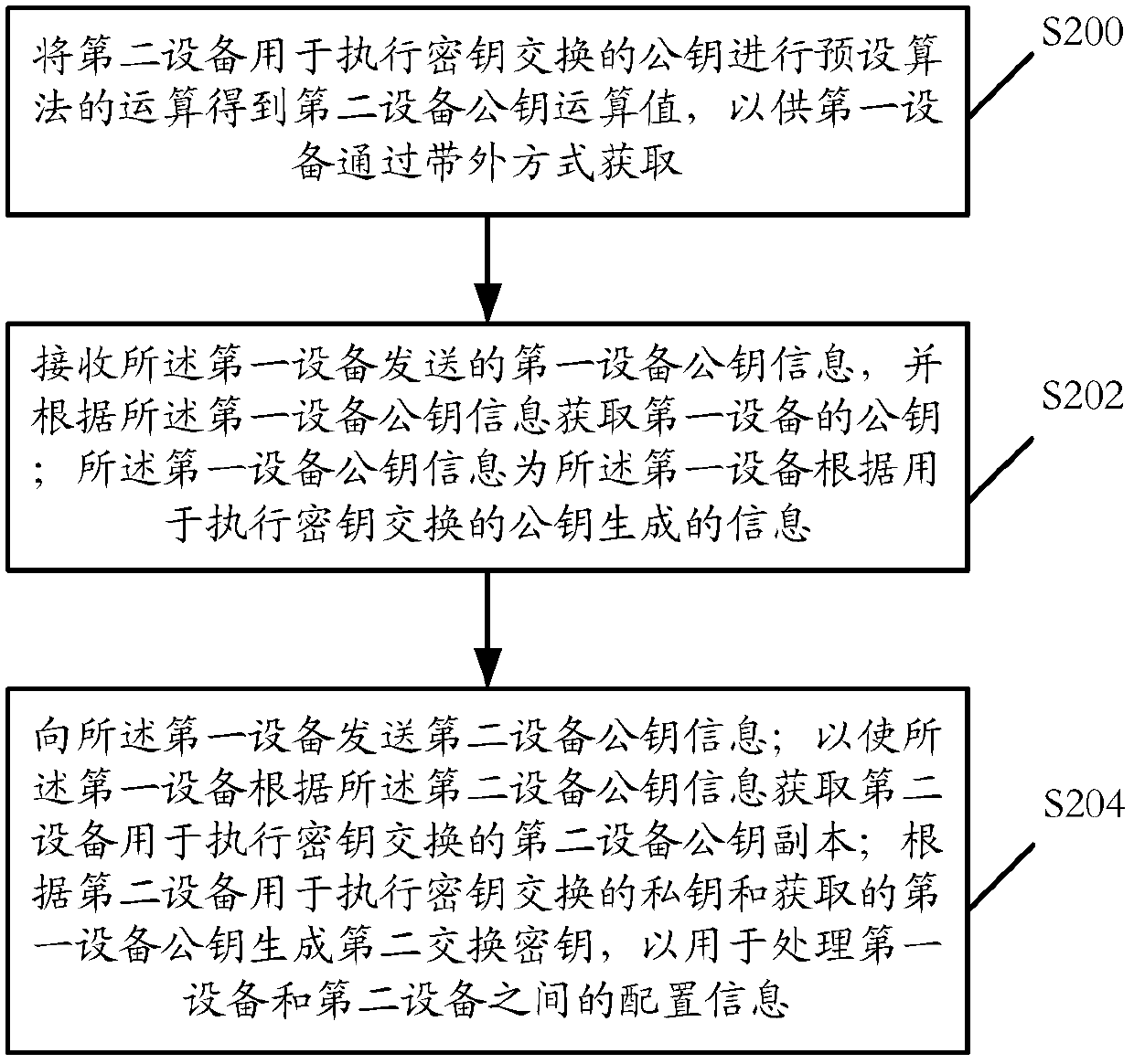
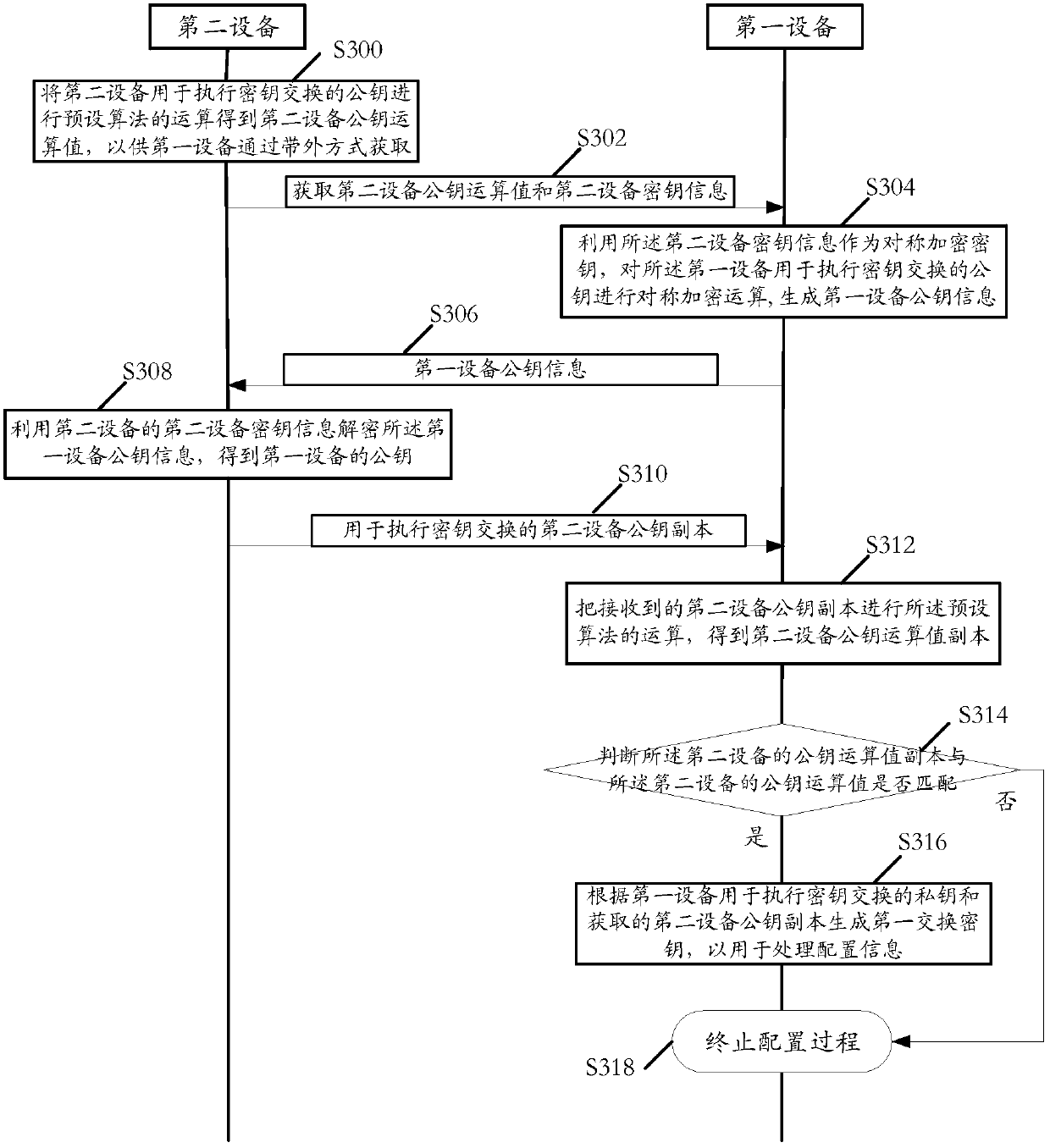
[0239]Step S300: The second device uses the public key used by the second device to perform the key exchange to perform the operation of the preset algorithm to obtain the operation value of the public key of the second device, which is obtained by the first device in an out-of-band manner;
[0240] Specifically, the second device holds its own public-private key pair, that is, the second device private key (assumed to be a Key second device) and the second device public key (assumed to be a PKey second device); The operation algorithm performed by the key can refer to figure 1 The operation algorithm described in step S100 in the embodiment will not be repeated here; it can be understood that the operation value of the second device public key (assumed to be the operation value of the second device PKey) in the embodiment of the present invention can also be calculated by the above algorithm The obtained public key operation derivative value (assumed to be the Pkey second dev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com