An intrusion detection data processing method, device, and system
An intrusion detection and data technology, applied in the information field, can solve the problems of difficult to achieve interactive verification between different data, difficult coordination, and more labor and time consumption, so as to improve the efficiency of intrusion detection, reduce the difficulty of coordination, and facilitate automation. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
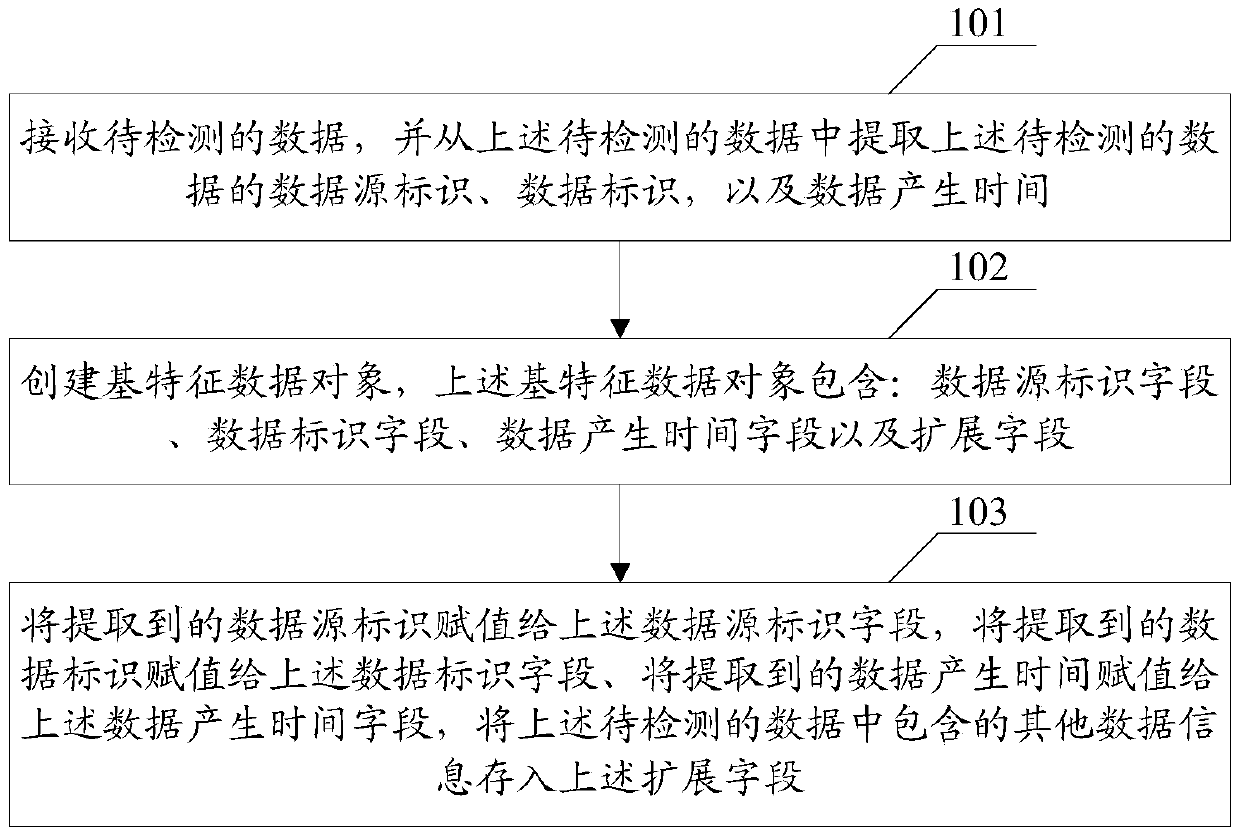
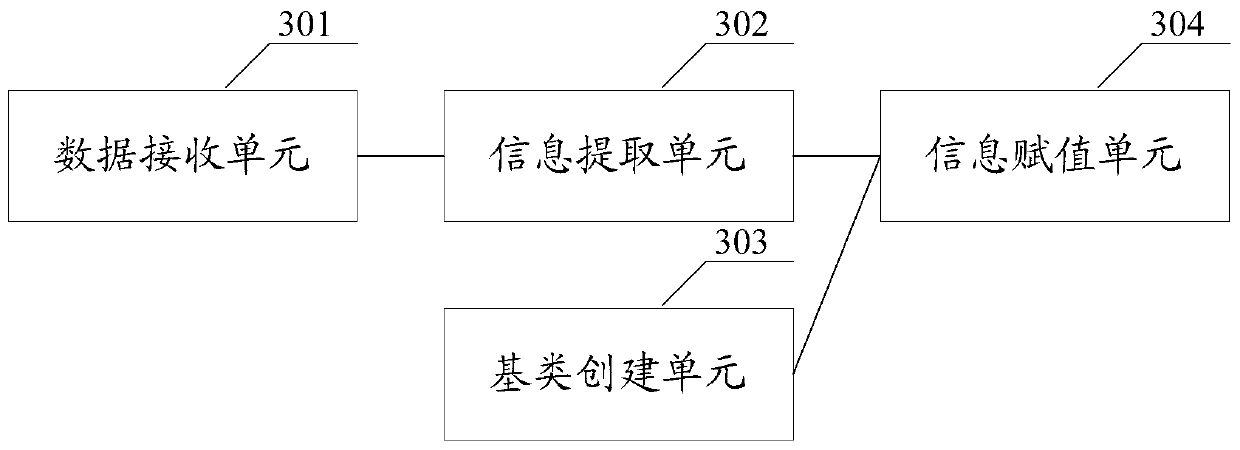
[0117] Example 1. User execution commands collected by the host, standardized process:
[0118] 1. The data collected by the host is as follows: For example, a record is collected from the host 10.123.18.9. as follows:
[0119] Command: cat; parameter: cat / etc / passwd; user: test; execution directory: / root;
[0120] Process id: 3349, parent process: bash. Execution time: "2014-3-10 12:00:00".
[0121] 2. Through the standardization of the standardization center, the host ID "10.123.18.9" is transformed into an unsigned integer: 152206090, parameters: cat / etc / passwd hit rule 110 (check system key files); execution time "2014-3-1012:00 :00", normalized to unixtime:1394424000. After normalization of the whole data:
[0122]
[0123]
[0124] 3. The data records after the aforementioned standards are judged as high-risk access after the intrusion detection system analysis (IDS1). Add an analysis record in the "content" field. After IDS1 analysis, add "ids_name": "IDS...
example 2
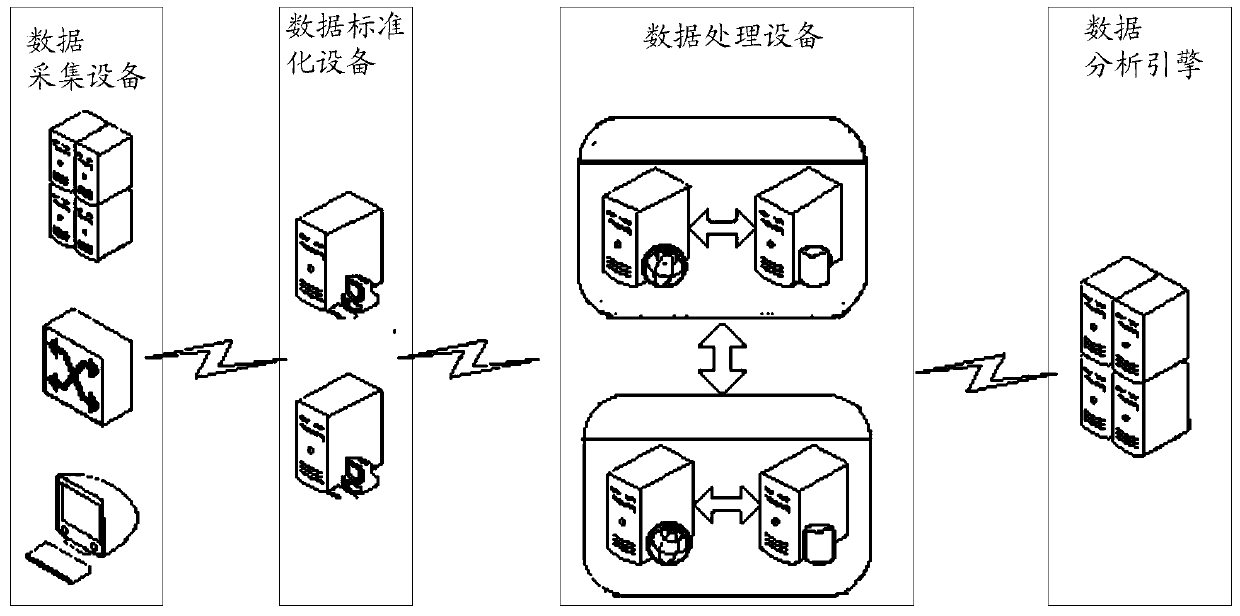
[0127] Example 2. Access records httplog collected by network switches, standardized process:
[0128] 1. The httplog data collected by the network switch is as follows: For example, switch 10.123.18.9 collected a Get request. as follows:
[0129] Request time: "2014-3-10 12:00:00".
[0130] reqtype: GET
[0131] "src": "127.0.0.1",
[0132] Access domain name: x.xx.com
[0133] CGI: getinfo
[0134] cookie:**************; Among them, the following parameters:
[0135] para:appVer=1.0.2.5109&b_uid=${((#context["xwork.MethodAccessor.deny MethodExecution"]=new java.lang.Boolean(false), #_memberAccess["allowStaticMethodAccess"]=true,
[0136] #a=@java.lang.Runtime@getRuntime().exec('cat
[0137] / etc / passwd').getInputStream(), #b=new java.io.InputStreamReader(#a), #c=new java.io.BufferedReader(#b), #d=new
[0138] char[51020], #c.read(#d), #kxlzx=@org.apache.struts2.ServletActionContext@getResponse().getWriter(), #kxlzx.println(#d), #kxlzx.close() ))}&cKey=SEWVS43B1D7708...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com