Multi-process access memory database system
A database and multi-process technology, applied in the field of multi-process access to memory database systems, can solve problems such as the inability to meet high-speed access efficiency, and achieve the effects of improving writing efficiency, reducing latency, and reducing coupling.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
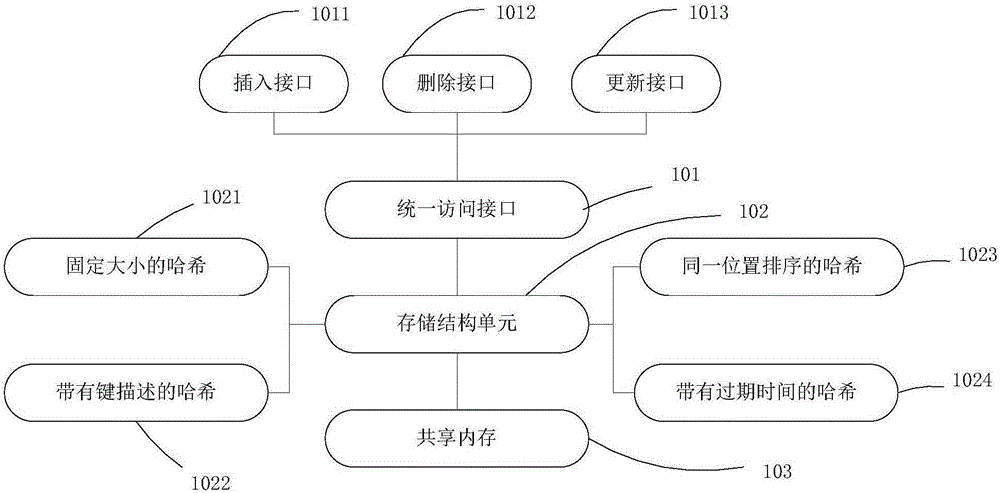
[0036] This system is a non-relational database system based on a shared-memory in-memory database. The general structure of the system is as follows figure 1 As shown in the figure, the system provides an interface for adding, deleting, modifying and other main functions of the database to access data of the key-value pair (key-value) type.
[0037] Specifically, the multi-process access memory database system includes a unified access interface 101 for application programs to perform access operations, and a storage structure unit 102 for extending the database storage engine. This system does not provide port monitoring and network access, but directly provides a unified access interface 101 for processes.
[0038] More specifically, the unified access interface 101 includes an insert interface 1011 , a delete interface 1012 , and an update interface 1013 . The application program can be operated through the corresponding interface. The unified access interface 101 not on...
Embodiment 2
[0054] The difference between this embodiment and the above-mentioned embodiment is that this embodiment is the principle and process of executing the deletion request for the user, such as Figure 5 shown.
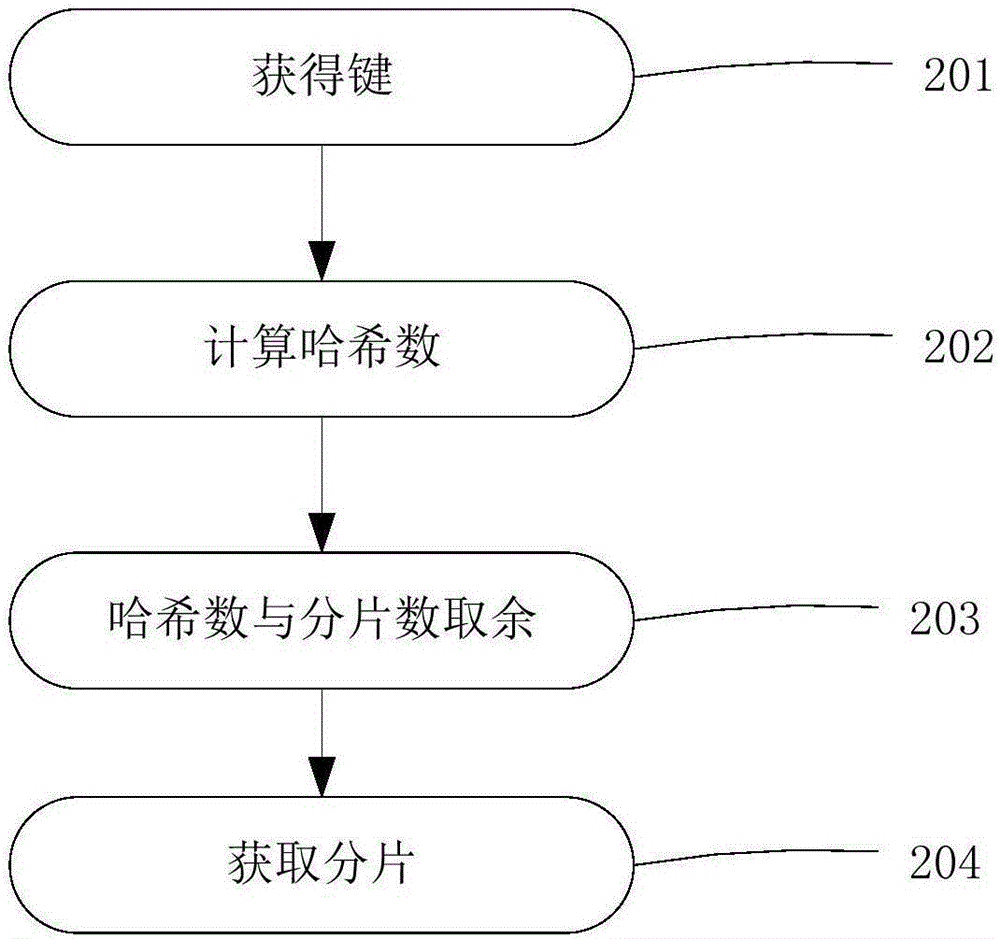
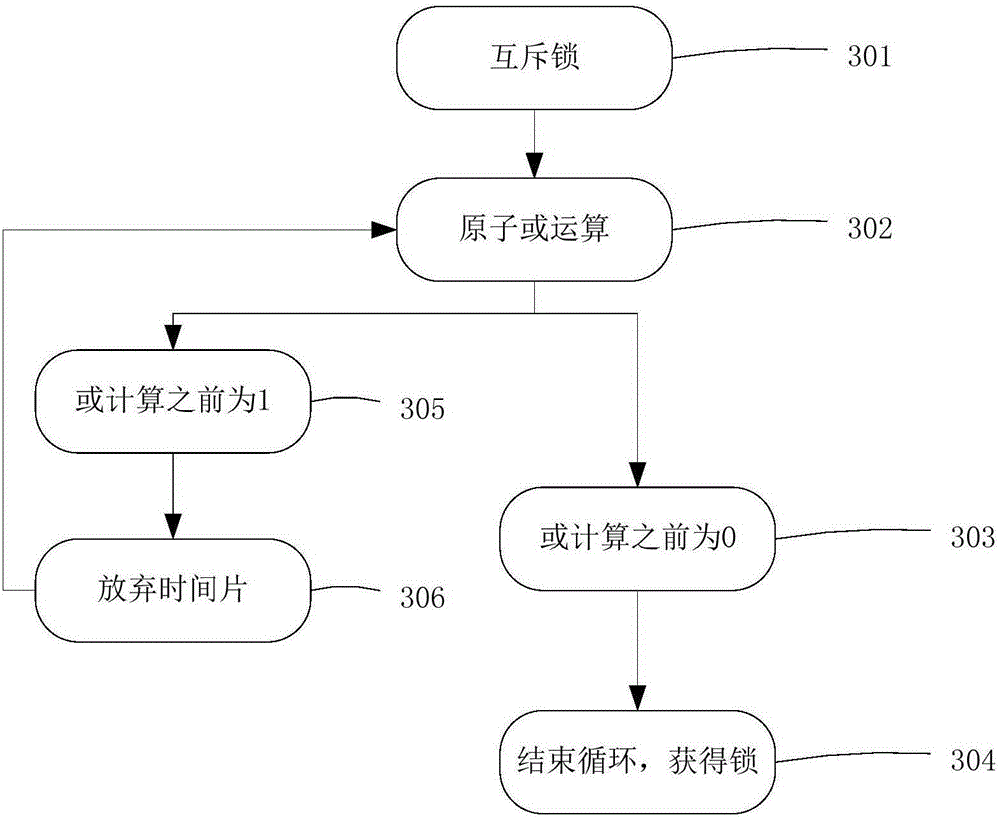
[0055] The delete operation first requires a mutex service, and the process is as follows image 3 As shown, it will not be repeated here. After acquiring the lock, there will be no other additions, deletions, or modifications at the same time. Traverse all key-value pairs (key-value) in bucket position 501 to find out whether the key to be deleted exists. If the target key is not found in step 502, immediately release the lock 503 and exit, and this deletion operation fails. If the target key is found in step 504 and exists, the value pointer 505 to be deleted is obtained, and the update bit is set 506 .
[0056] The update bit is then set to flag the query operation, as described above. At this time, step 507 is executed to delete the target key at the bucket locati...
Embodiment 3
[0059] The difference between this embodiment and the above-mentioned embodiment is that this embodiment is the principle and process of performing an update request for the user, such as Figure 6 shown.
[0060] The update process is similar to the delete process. When the user initiates an update request, the mutex service is first performed. The process is as follows image 3 As shown, it will not be repeated here.
[0061] Traversing all key-value pairs in the bucket location, if the key does not exist, release the lock and end the update process. After obtaining the current value pointer 601, update the value pointer 602 at the target key position, but the previous value pointer cannot be released at this time, and there may be a query operation in use, and then the update bit is set 603. Then obtain the reference count pointer 604, update the reference count pointer 605, and execute step 606, wait for the reference count pointer to return to 0, and then release the re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com