A Secure Login Method Based on National Secret Algorithm
A technology of secure login and national secret algorithm, which is applied in the field of secure login of network equipment, can solve problems such as large security risks, and achieve the effects of improving security, strong portability, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
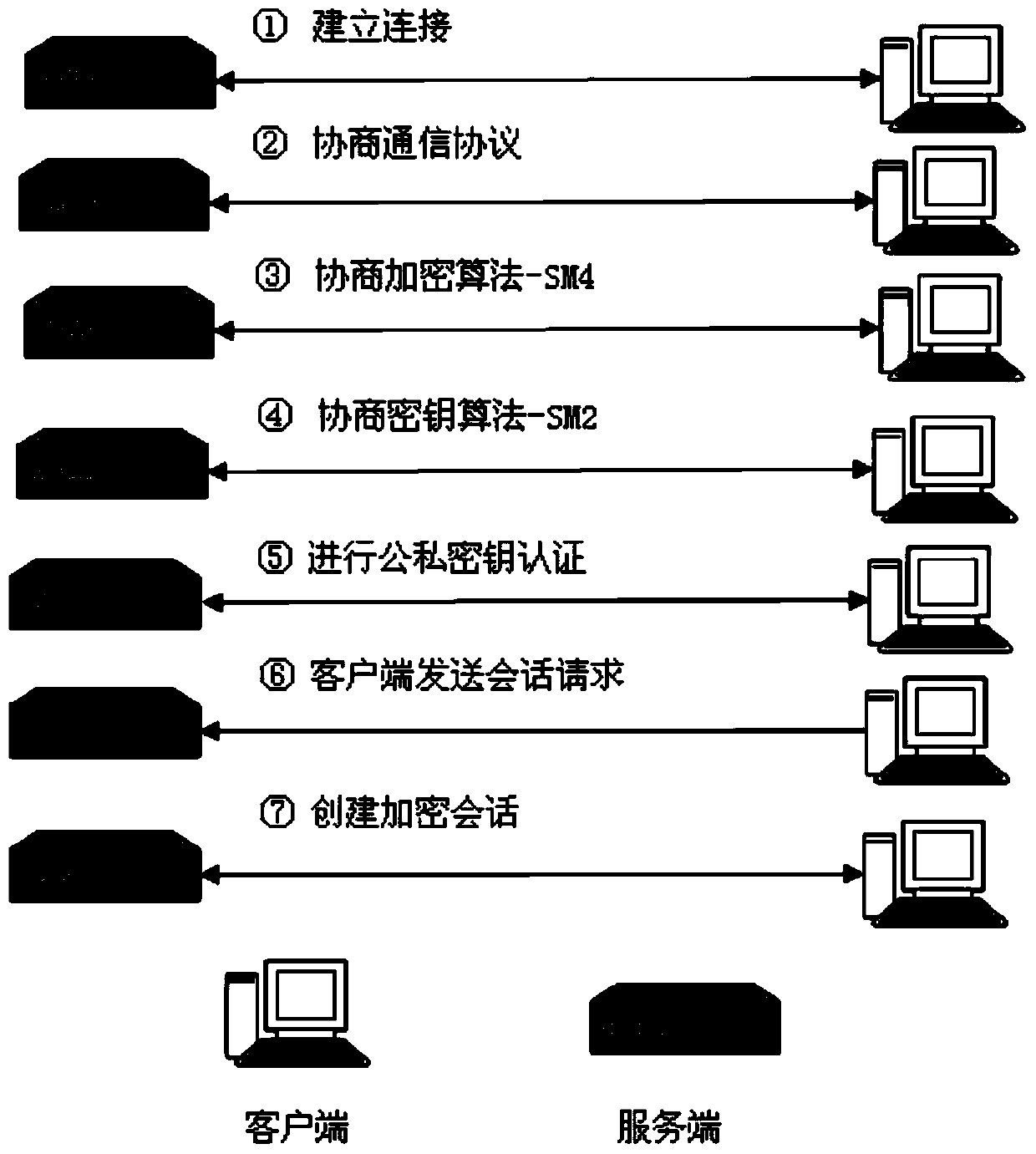
[0015] A secure login method based on the national secret algorithm. The device login software consists of two parts, the server and the client, which are installed on the embedded device and the debugging machine computer respectively, and the device and the computer are connected through the network port. The client logs in to the device remotely through the network, shielding the password authentication method with high security risks, and the software adopts the key verification method, and the user can log in to the device only after the client and server keys pass their respective verifications. Among them, the core key agreement and communication encryption are completely implemented based on the National Secret Algorithm.
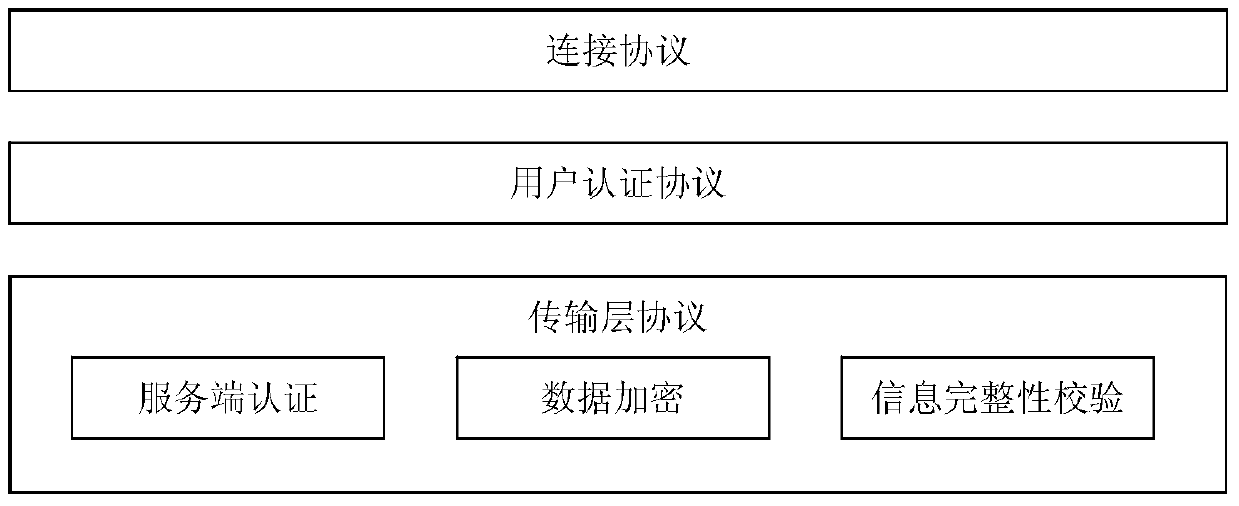
[0016] Such as figure 1 As shown, the communication protocol framework of secure remote login: Transport Layer Protocol (Transport Layer Protocol) provides server authentication, transmission data encryption and data integrity verification; User Aut...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap