Method for generating and verifying credible label based on asymmetrical encryption algorithm and system
An asymmetric encryption and verification method technology, applied in the direction of user identity/authority verification, etc., can solve problems such as poor security, poor versatility, and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
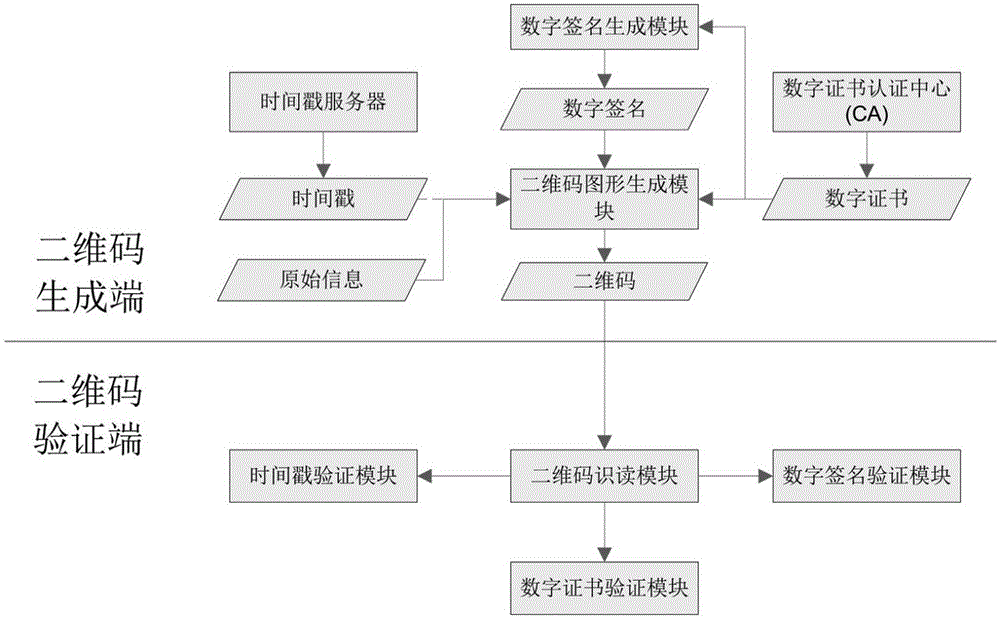
[0200] according to figure 1 , the specific embodiment of the present invention (one) is as follows:
[0201] Step 1: The certification center CA generates a digital certificate for the QR code service provider;
[0202] Step 2: The QR code service provider generates a digital signature through the digital signature module, and the timestamp server generates a timestamp for the QR code;
[0203] Step 3: The two-dimensional code generation module generates a two-dimensional code according to the original information of the two-dimensional code, digital certificate information, time stamp and digital signature, and appropriate generation parameters;
[0204] Step 4: When using or verifying the two-dimensional code, use the two-dimensional code reading module to correctly read the two-dimensional code, extract the information in it, and output it to the time stamp verification module, digital certificate verification module and digital signature verification module;
[0205] ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com