Openflow-based flow depth correlation analysis method and system
A technology of correlation analysis and flow analysis, which is applied in the field of computer networks, can solve problems such as failure to meet security event behavior analysis and analysis requirements of multiple dimensions of network traffic, and achieve the effect of satisfying security event behavior analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
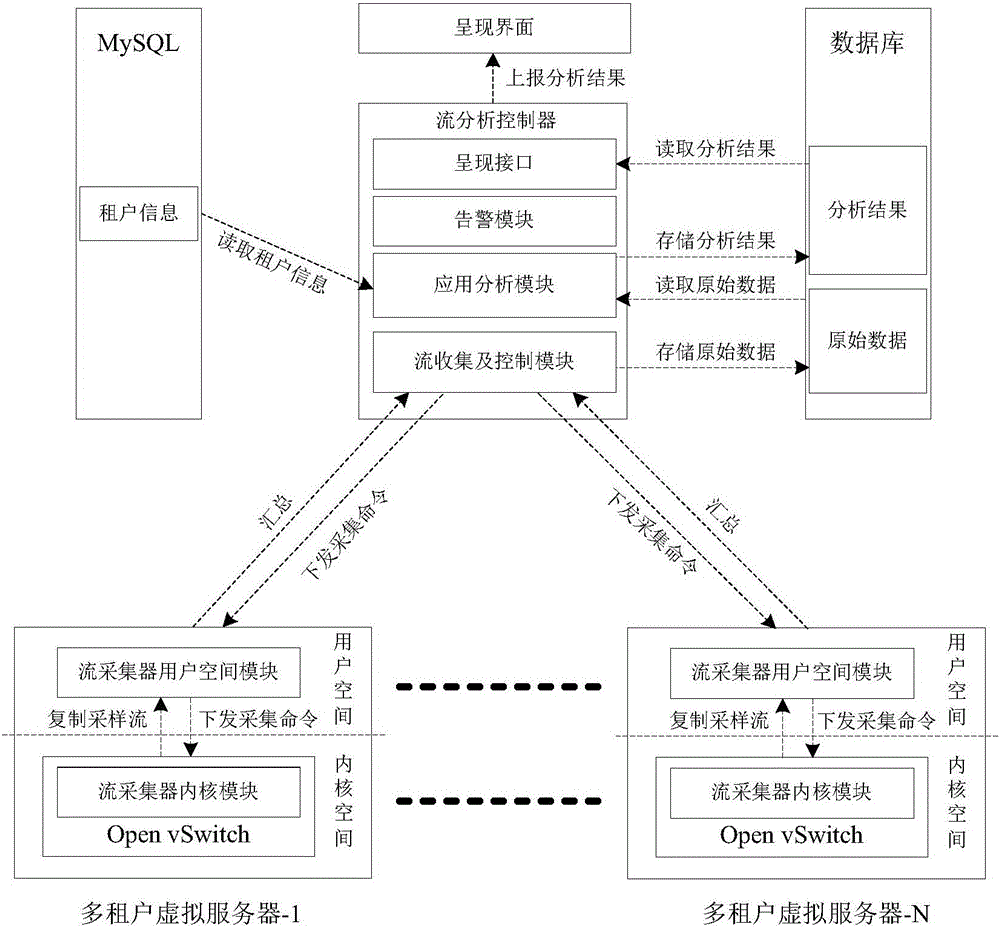
Image
Examples
Embodiment 1
[0088] Example of SYN Flood attack detection on a virtual network in a cloud environment:
[0089] There are a large number of users in the cloud environment. Because the resources rented by these users share a large resource pool, once a cloud host has a security problem, such as becoming a bot for hackers to attack, it will have a great impact on the business of other users in the cloud. influences. Utilizing the present invention can provide convenient means for cloud operators to quickly and effectively know where and how attacks occur.
[0090] Taking a cloud host in a cloud environment as a hacker's hacker (a computer remotely controlled by a hacker) and starting to launch a SYN Flood attack to the external network as an example, this embodiment can quickly identify the attack behavior:
[0091] 1) The cloud host captured by the hacker launches a SYN Flood attack;
[0092] 2) In order to cover up the attack behavior, hackers forged a large number of fake source address...
Embodiment 2
[0100] Examples of security vulnerability scanning and detection in cloud environments:
[0101] A cloud host in the cloud environment has a security risk, and a port scan is performed on the virtual machine inside the cloud platform. The flow analysis controller calls the application analysis module to analyze the received flow information, finds that the connection frequency initiated by the cloud host exceeds the threshold, calls the alarm module to notify the administrator, and generates a report to display on the interface. Specifically include:
[0102] 1) A host starts port scanning to other hosts, sniffing machines with security vulnerabilities in the cloud.
[0103] 2) The scanning packets sent by the attacking host to each host are not many, and it is difficult to find security abnormal behaviors through large-scale traffic analysis and inspection, which will be covered up by a large number of normal traffic.
[0104] 3) The stream acquisition module records all tr...
Embodiment 3
[0110] Examples of business dynamic expansion decision-making in cloud environment:
[0111] With the dynamic expansion of the business in the cloud environment, the amount of resources cannot meet the business needs and needs to be adjusted dynamically. Using the method of this embodiment, accurate quantitative analysis can be realized, and the feedback can be fed back to the cloud platform according to the established strategy, so that the amount of resources can be dynamically adjusted. Specifically include:
[0112] 1) The user deploys the business system, regularly obtains connection statistics and reports them to the controller.
[0113] 2) The information reported to the controller includes multiple information such as normal connection, connection not established normally, bandwidth usage rate, and concurrent connection.
[0114] 3) The stream acquisition module records all traffic, and imports it from the kernel to the user space module, and then passes it to the st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com