Service request processing method, terminal browser and anti-attack server
A technology of business requests and processing methods, which is applied in the field of Internet security, can solve problems such as not being able to intercept attacks in time, and achieve the effect of reducing the processing burden and preventing attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
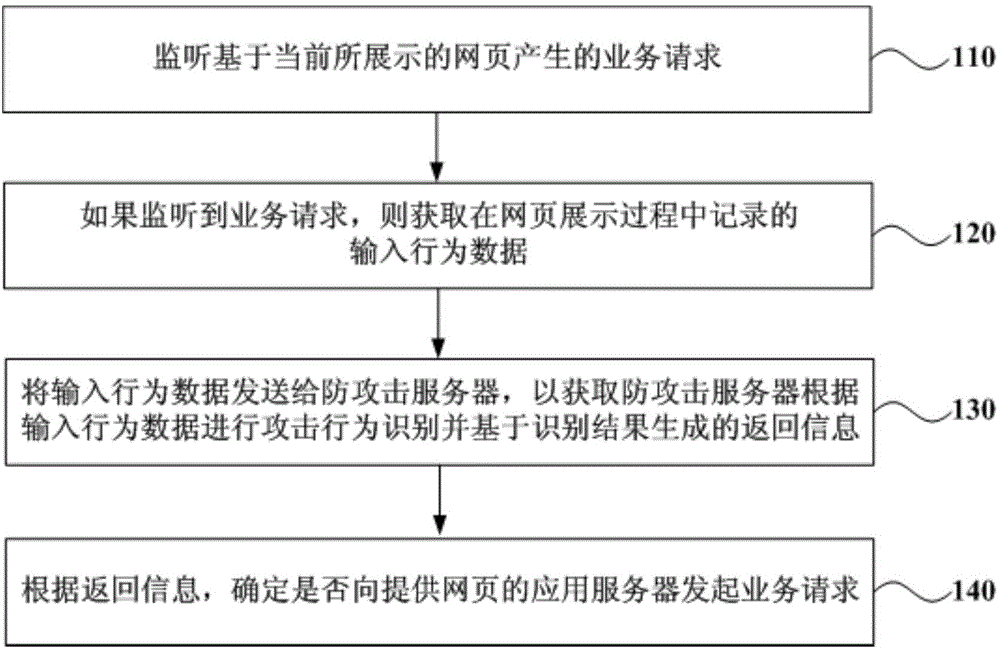
[0037] figure 1 It is a schematic flowchart of a service request processing method provided in Embodiment 1 of the present invention. This embodiment is applicable to a network architecture composed of a terminal browser, an application server, and an attack prevention server. The method can be executed by a browser on a terminal, and the terminal can be an electronic device such as a notebook computer, a desktop computer, etc., which has functions of mouse input and web page browsing. see figure 1 , the service request processing method provided in this embodiment specifically includes the following operations:
[0038] Operation 110, monitor the service request generated based on the currently displayed webpage.
[0039] The displayed webpage can be obtained by the browser from the application server. A web page contains at least one component. After obtaining a trigger event for any component in the webpage, the browser will generate one or more service requests (that ...
Embodiment 2
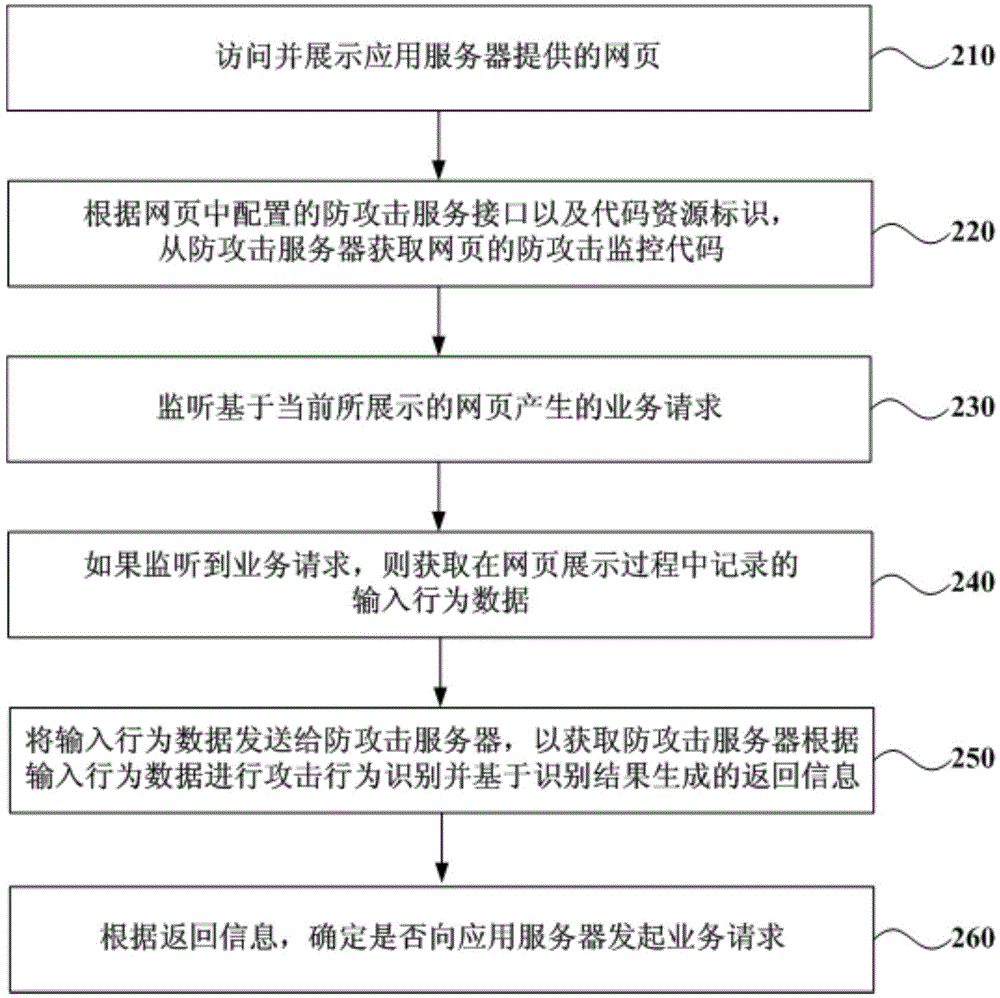
[0052] figure 2 It is a schematic flowchart of a service request processing method provided in Embodiment 2 of the present invention. In this embodiment, on the basis of the first embodiment above, an operation of acquiring the anti-attack monitoring code is added. The method provided in this embodiment can still be executed by the browser on the terminal. see figure 2 , the method provided in this embodiment specifically includes the following operations:
[0053] Operation 210, accessing and displaying the webpage provided by the application server.
[0054] Operation 220, according to the anti-attack service interface and the code resource identifier configured in the webpage, acquire the anti-attack monitoring code of the webpage from the anti-attack server.
[0055] The webpage accessed by the browser is configured with an attack prevention service interface and a code resource identifier. Wherein, the code resource identifier is a character string uniquely identif...
Embodiment 3
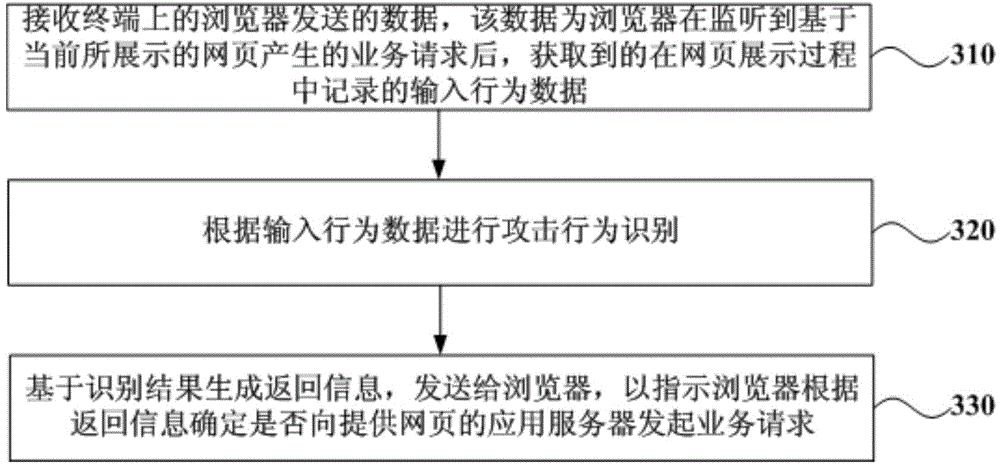
[0065] image 3 It is a schematic flowchart of a service request processing method provided in Embodiment 3 of the present invention. This embodiment is still applicable to a network architecture composed of a terminal browser, an application server, and an attack prevention server. The method can be executed by the attack defense server, and can be executed in cooperation with the service request processing method implemented by the terminal browser provided by any embodiment of the present invention. As a third-party physical device that provides anti-attack services for application servers, the anti-attack server can perform anti-attack monitoring on service requests before the terminal browser initiates service requests to the application server. see image 3 , the service request processing method provided in this embodiment specifically includes the following operations:
[0066] Operation 310, receiving the data sent by the browser on the terminal, the data is the in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com