Two-way set top box intrusion detection system and detection method thereof
An intrusion detection system and a two-way set-top box technology, applied in the field of radio and network security, can solve problems such as interruption of legal programs, storage of illegal applications, destruction, etc., to achieve the effect of ensuring normal and uninterrupted operation, ensuring links, and ensuring network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
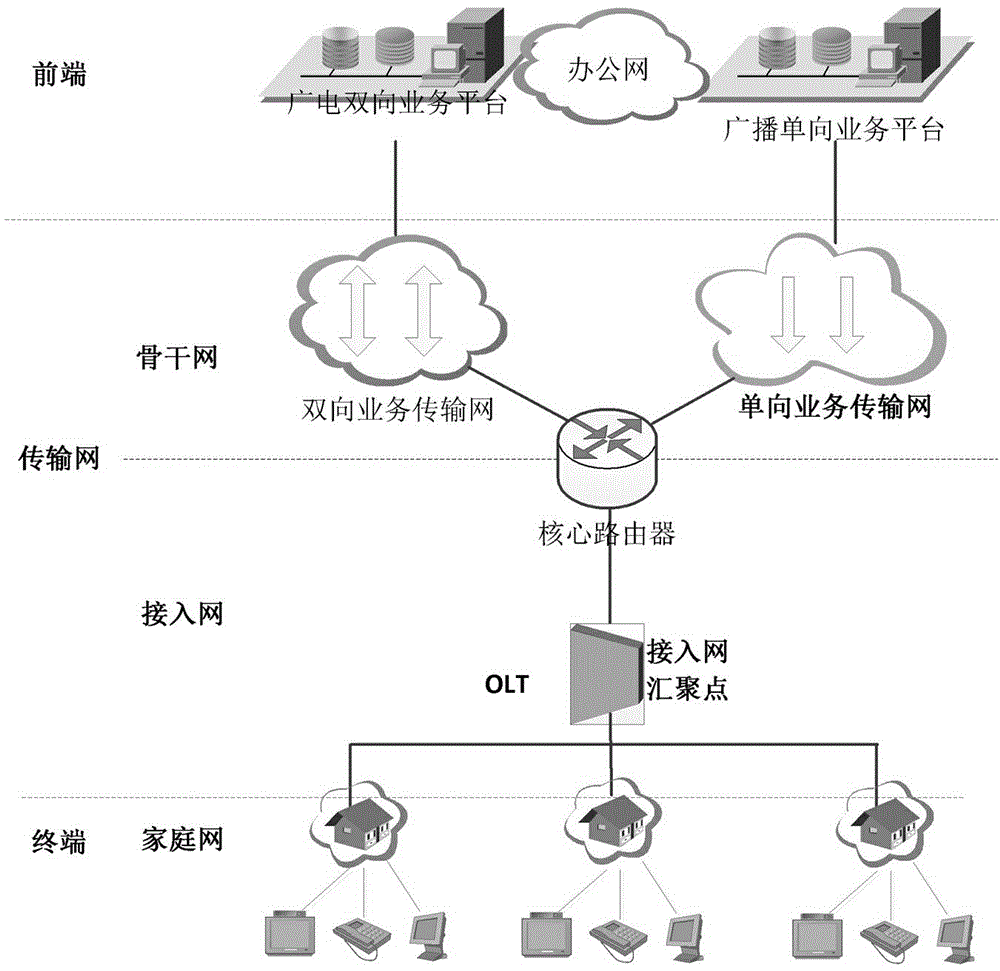
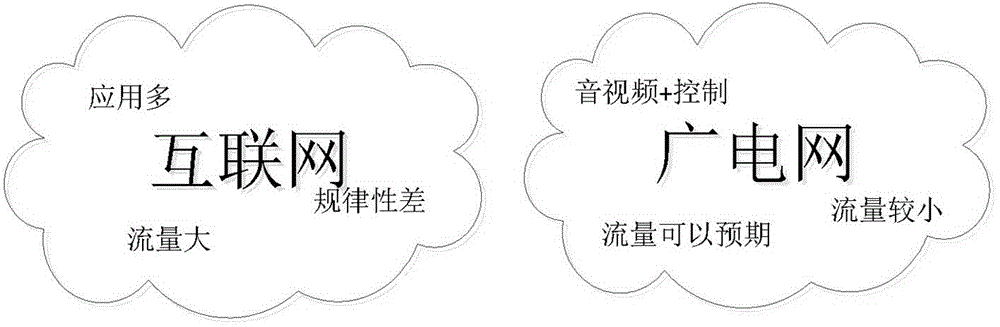
[0043] Embodiment one, see Figure 2~4 as shown, figure 2 The traffic comparison chart of the Internet and the radio network is given. The traffic components in the Internet are quite complex, the applications are numerous, and the traffic regularity is poor. This also prompts the use of various relatively complex detection methods to detect attacks at the Internet access network end. Ensure security; unlike the Internet, broadcast network traffic is small and its components are relatively simple, mainly just some video streams, customer on-demand streams, and set-top box recording streams that operators need to recycle within a certain period of time. These predictable broadcast network traffic can be processed It is not as complicated as the Internet; therefore, the radio network access network does not need to follow the security mechanism of the Internet access network, and it can directly use a simpler detection system or method to complete the security detection of the ...
Embodiment 2
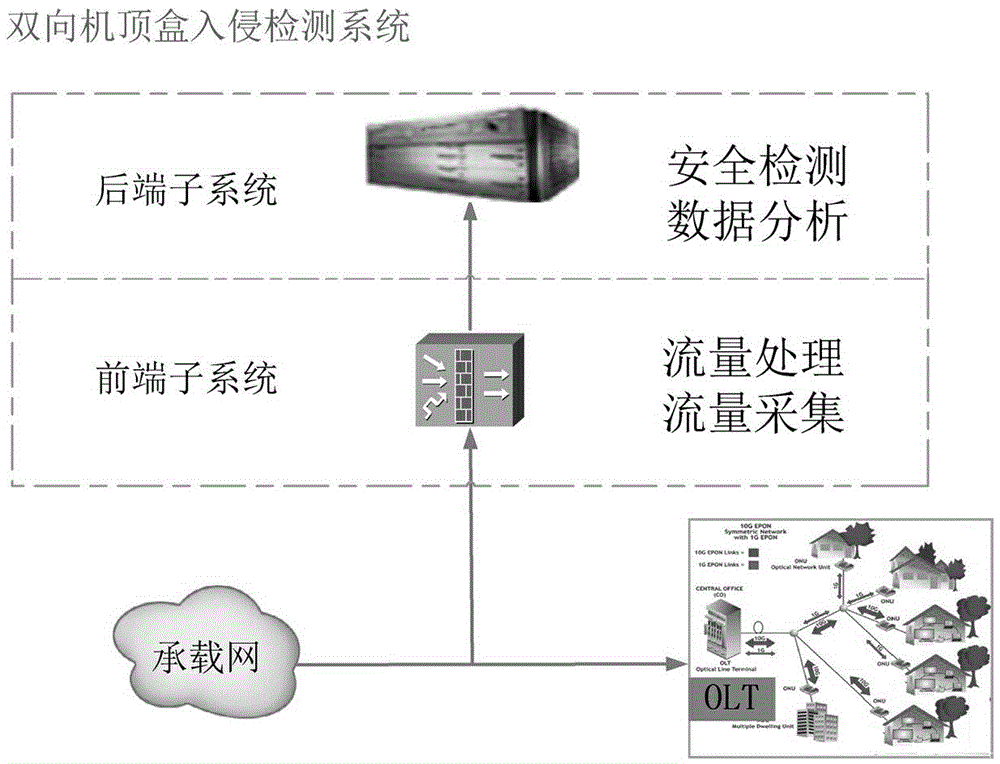
[0044] Embodiment two, see Figure 5 As shown, it is basically the same as Embodiment 1, except that the rear subsystem further includes a security detection module, which compares and detects security threats based on a security threat database, and notifies the front subsystem in real time. The back-end system is equipped with a safety detection module, including a safety detection module with known threat characteristics and a safety detection module with unknown threat characteristics. The security detection module with known threat characteristics maintains various security threat databases with known characteristics, and performs security threat detection on input traffic according to known characteristics. The security detection module of unknown threat characteristics uses the method of big data association analysis newly proposed in recent years to detect security threats, analyze the threat characteristics of the detected threats, and add the analysis results to the ...
Embodiment 3
[0045] Embodiment 3 is basically the same as Embodiment 1, except that the two-way set-top box intrusion detection system also includes a wire-speed serial connection optical / electrical switching protection module, and the wire-speed serial connection optical / electrical switching protection module is connected in series upstream of the OLT The interruption problem in the bidirectional link ensures the smooth flow of the link. When a fault occurs, the link can be switched to the transparent transmission mode in real time, and the fault point can be automatically avoided in real time, thereby ensuring the normal and uninterrupted operation of the access network.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com