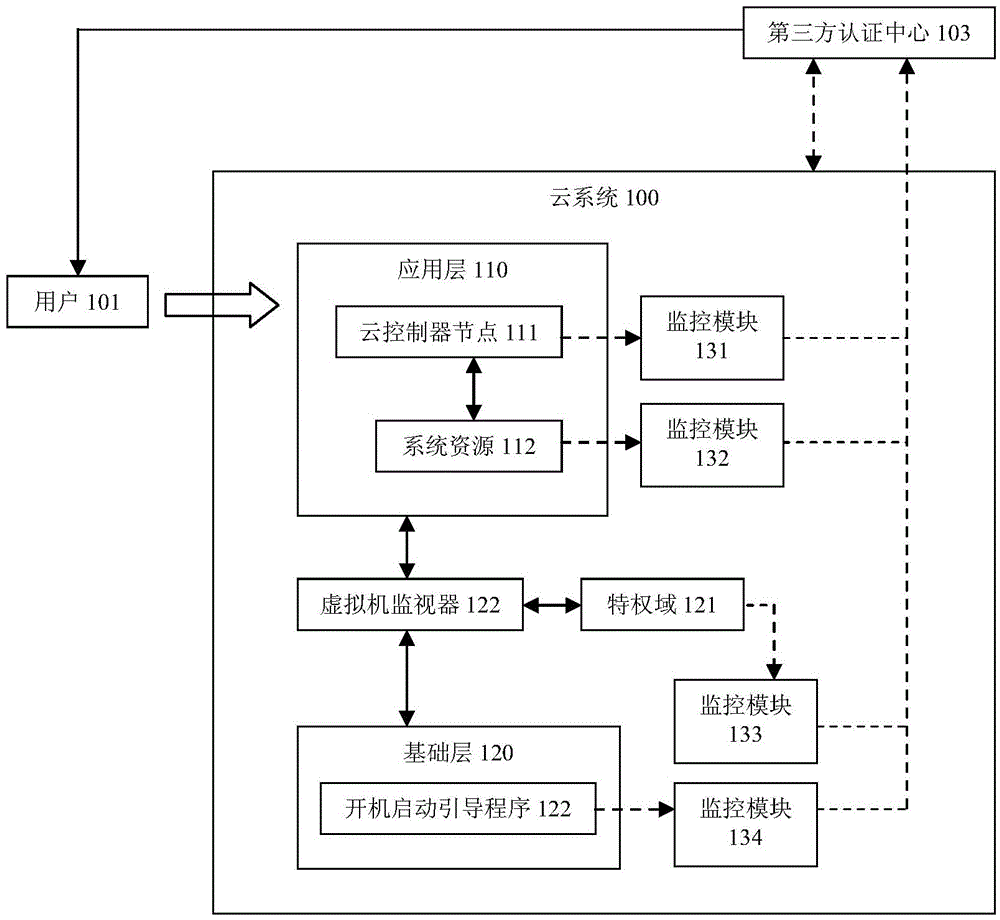
Security monitoring method for protecting cloud system
A security monitoring and cloud system technology, applied in the computer field, can solve problems such as privacy leakage, cloud service providers or other official institutions cannot view, cloud system has no clear answer, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The implementation of the present invention will be described in detail below in conjunction with the accompanying drawings and examples, so that implementers of the present invention can fully understand how the present invention uses technical means to solve technical problems, and achieve the realization process of technical effects and according to the above-mentioned realization process The present invention is implemented concretely. It should be noted that, as long as there is no conflict, each embodiment and each feature in each embodiment of the present invention can be combined with each other, and the formed technical solutions are all within the protection scope of the present invention.
[0036] With the deepening of the application of cloud computing technology, users pay more and more attention to the security of cloud products while paying attention to the convenience of using cloud system products. Especially the security issues of the data that you put...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com