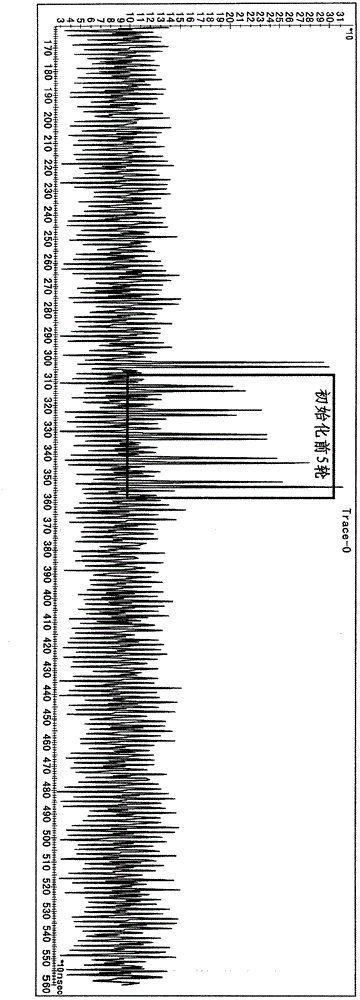
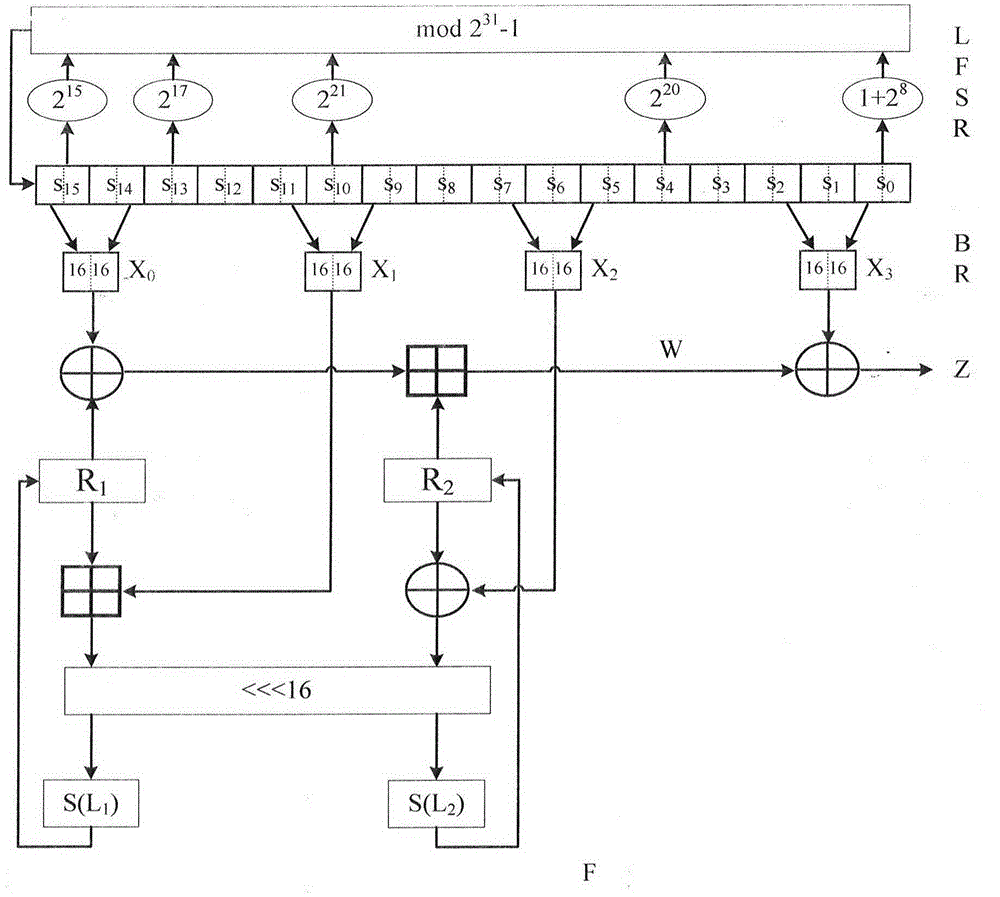
Side channel energy analysis method for ZUC cryptographic algorithm with mask protection
A cryptographic algorithm, energy analysis technology, applied in wireless communication, secure communication device, security device, etc., can solve the problem of not being able to know the mask and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
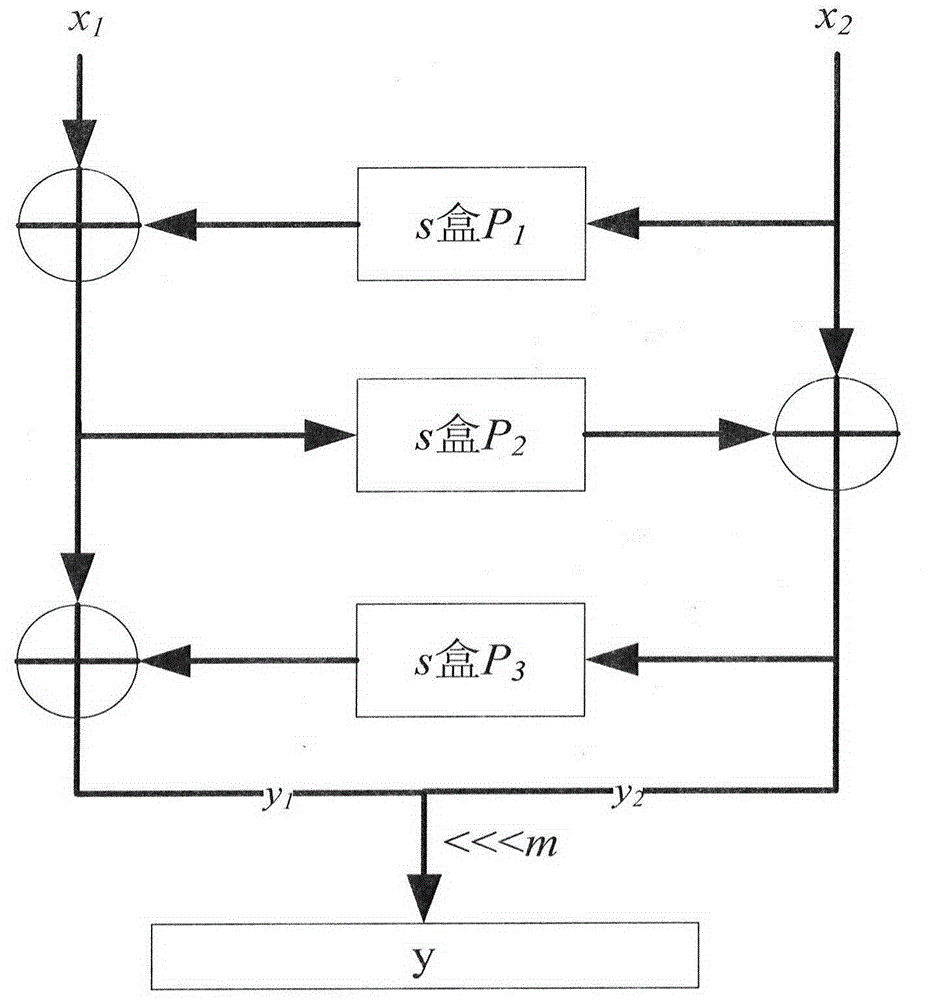
[0104] The technical solution of the present invention is described in detail below. First, the first-order simple mask protection method is introduced. In order to save the storage space of the S box and speed up the efficiency of the mask, the designer will use one S box on the left and right sides of the F function of the ZUC algorithm 32-bit random number m for mask pre-calculation, output Then the output of 8 S-boxes only needs to pre-calculate 4 S-boxes. If the realization is more efficient, m=(m 0 , m 1 , m 0 , m 1 ), where m 0 , m 1 are all 8-bit random numbers, only two S-boxes need to be preprocessed. Such as image 3 The first-order mask S-box defense mode of the ZUC algorithm is shown, and the inputs of the left and right S-boxes are respectively S _ in R ′ = S _ in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com