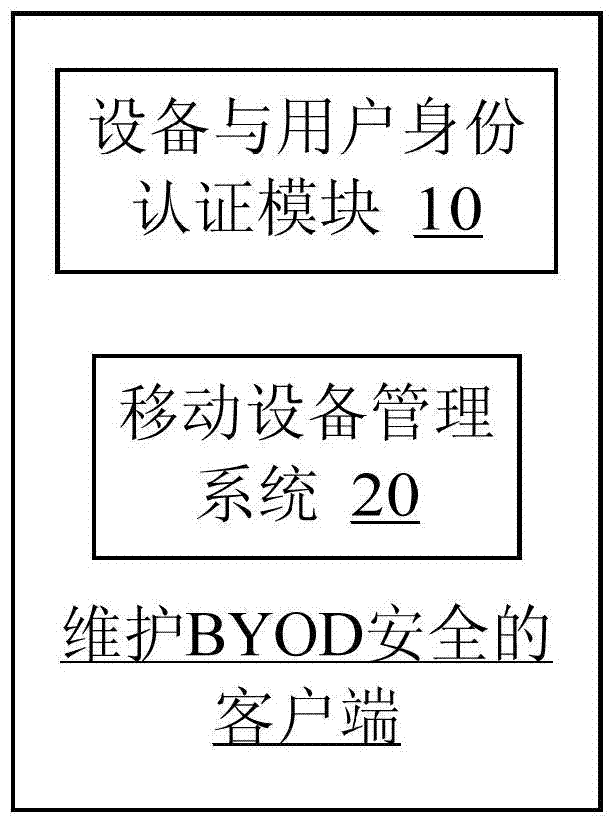
Client and method for maintaining BYOD (Bring Your Own Device) safety
A client-side and secure technology, applied in the field of communication, can solve the problems of inability to effectively balance enterprise information security and employee information security, no solution has been proposed, and no alternate authentication method has been adopted.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Hereinafter, the present invention will be described in detail with reference to the drawings and examples. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
[0032] In the BYOD application scenario, the existing technology does not provide an effective solution to the problem of how to effectively balance enterprise information security and employee information security. Embodiments of the present invention will provide a new type of security solution to solve the above technical problems. question. The main idea of the embodiment of the present invention is to integrate a user identity authentication method based on facial images. When an employee forgets the user name or password, this user identity authentication method based on facial images can be used for identity authentication. To ensure that authorized personnel can smoothly enter the enterpri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com