Distributed network telephone system
A technology of distributed network and telephone system, applied in the field of distributed network telephone system, can solve the problems of low connectivity rate and communication quality, high probability of data interception and tampering, low security, etc. The effect of enhancing network adaptability and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
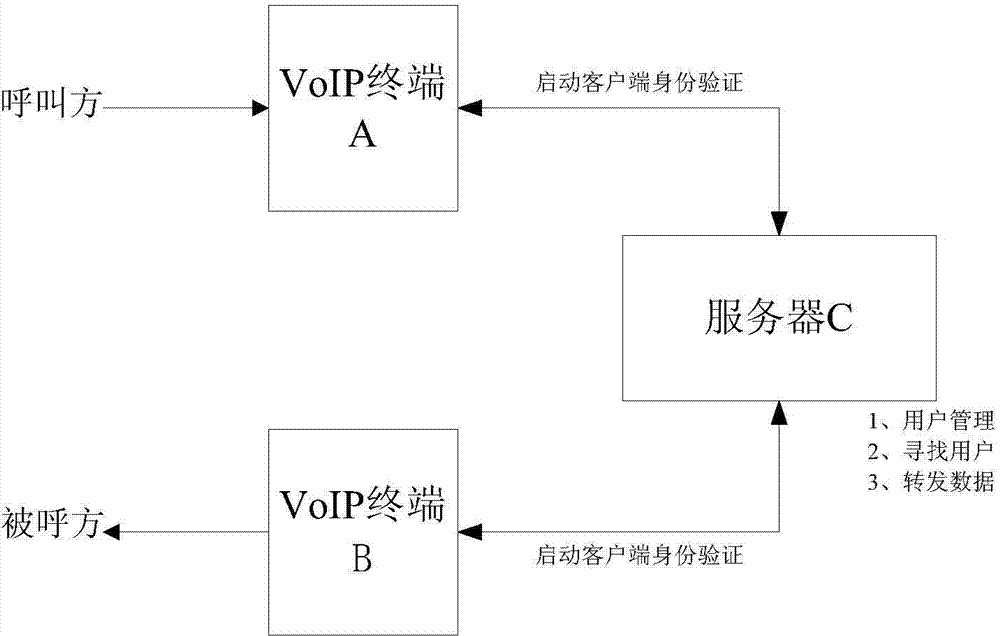
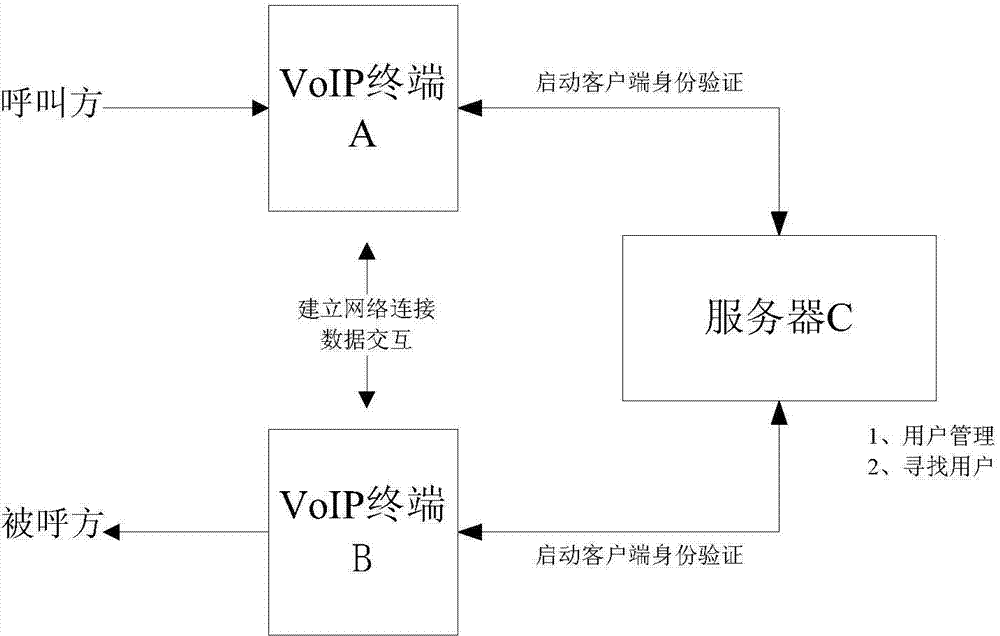
[0067] refer to Figure 5 , a distributed Internet telephone system, comprising a VoIP terminal A and a VoIP terminal B, said VoIP terminal A and VoIP terminal B are connected through n servers C, and its specific steps are as follows:
[0068] (1) When VoIP terminal A and VoIP terminal B are started, servers C1, C2...Cn verify VoIP terminal A and VoIP terminal B respectively;
[0069] (2) VoIP terminal A requests to call VoIP terminal B from servers C1, C2...Cn;
[0070] (3) Servers C1, C2...Cn receive the request from VoIP terminal A, find VoIP terminal B, and establish a connection;
[0071] (4) VoIP terminal B confirms the answer;
[0072] (5) VoIP terminals A and B are forwarded by servers C1, C2...Cn for voice communication, and the data streams to be sent by VoIP terminals A and B are divided into multiple data fragments, and the data fragments are formed according to the set traffic strategy. Each data block is encrypted with a different encryption method / different ...
Embodiment 2
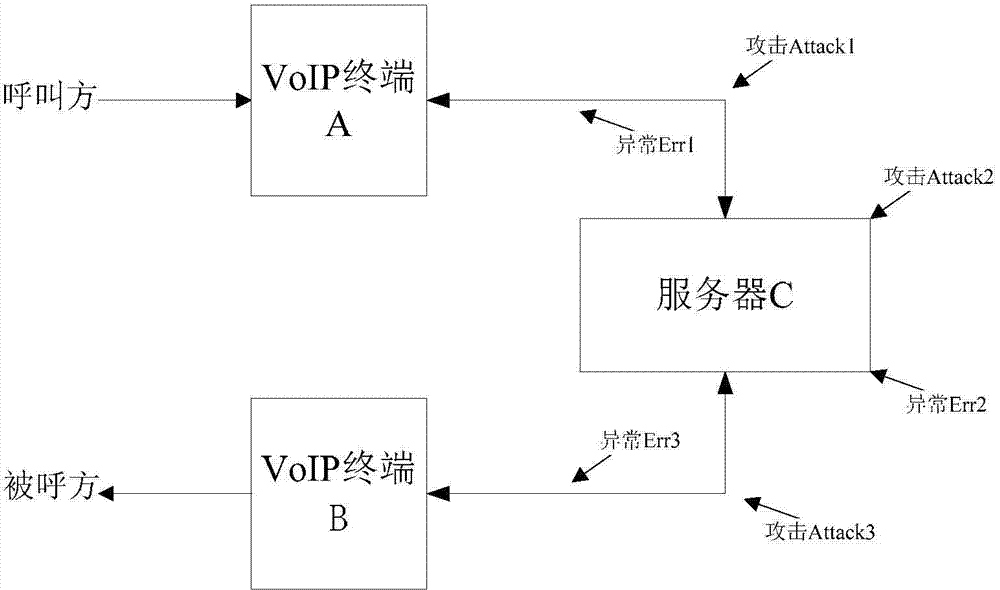
[0097] The difference between this embodiment and Embodiment 1 is that when any encryption key in step (5) needs to be modified, the modified key message is encrypted twice, and then forwarded by a different server C. The modification key message stores the content of the encryption key modified through negotiation between the communication parties. The modification key message itself is generally an encrypted message with certain security, but the present invention uses secondary encryption and random physical path , making it difficult for attackers to obtain and crack such sensitive messages, thus making the entire communication more secure.
[0098] see Figure 8 , taking the case of 3 servers as an example, showing the process of modifying the key K2:
[0099] 1. The data sent by VoIP terminal A through server C2 is encrypted by K2;
[0100] 2. VoIP terminal A wishes to modify the secret key K2;
[0101] 3. VoIP terminal A performs K1 encryption on the update K2 secret...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com