Gateway system and method for encrypting and decoding files
An encryption and decryption, encryption and decryption module technology, applied in the field of information processing, can solve problems such as inability to file encryption and decryption processing, and achieve the effect of facilitating demand upgrade and application expansion, data processing unification, and quantity saving
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
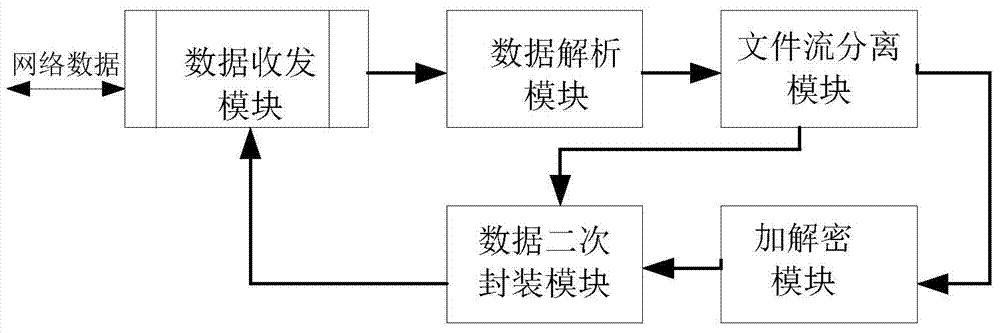
[0028] In Embodiment 1, the gateway system provided by the present invention is deployed between the switch and the server. The server stores plaintext file data, and the client requests the server to upload and download files to be detected by the gateway. The specific deployment location is as follows: figure 2 shown. The following takes the system's decryption of uploaded files and encryption of downloaded files as an example to specifically describe the workflow of the gateway system in Embodiment 1:
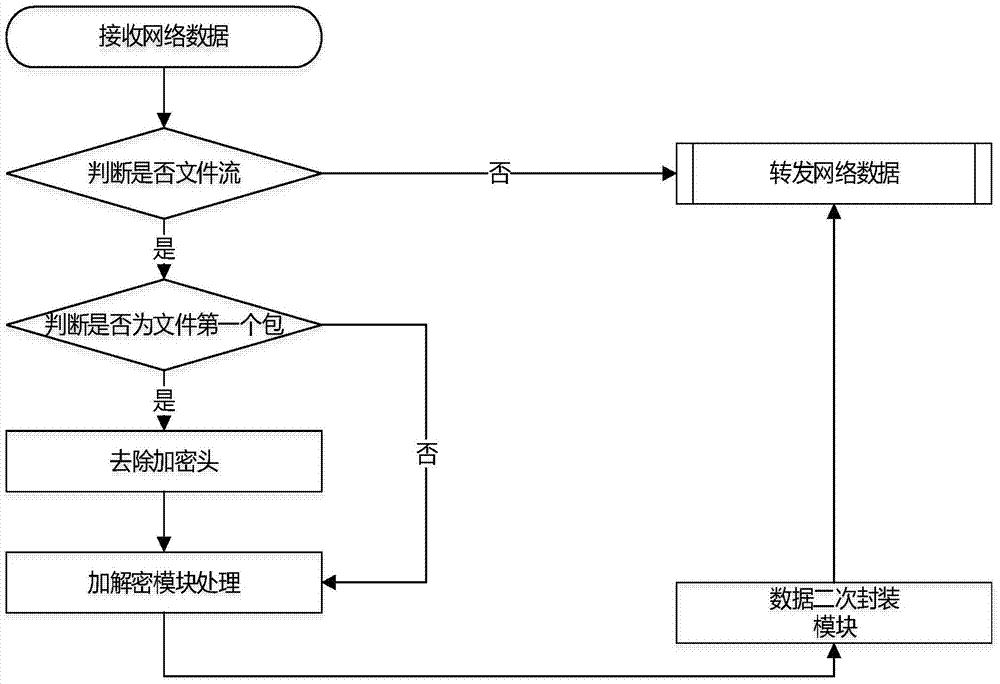
[0029] Such as image 3 As shown, the method of decrypting the uploaded file is as follows:
[0030] (1) The client sends an upload request to the server, and when the server passes the verification of the upload request, the client starts to upload files to the server; wherein, the upload request is a HTTP, FTP or CIFS protocol type request;
[0031] (2) The gateway system receives the file data and performs data analysis. When it recognizes the upload request and recogn...
Embodiment 2
[0037] Embodiment 2 is the application of the gateway system and the encryption and decryption method provided by the present invention in application uploading and downloading, specifically as follows:
[0038] a. Determine whether the client request is uploading or downloading; if it is uploading, go to step (b); if it is downloading, go to step e;
[0039] b, judging whether the file is a file encrypted by the gateway system of the present invention, if not, then not processing; if so, then enter step c;
[0040] c. Judging whether there is decryption authority according to the key level contained in the file header, if not, do not process, if there is authority, then enter step d;
[0041] d, strip the encrypted header of the file, and decrypt the received encrypted file according to the key information in the encrypted header; transmit the plaintext file to the server;
[0042] e. Add encrypted information in the file header according to the preset key level; send the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com