IMS system based session key negotiating method
A session key and key technology, applied in the field of information security, can solve the problems of difficulty in implementation and popularization, eavesdropping on session keys, and high terminal requirements, and achieve the effects of improving transmission security, reducing performance requirements, and facilitating system upgrades.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
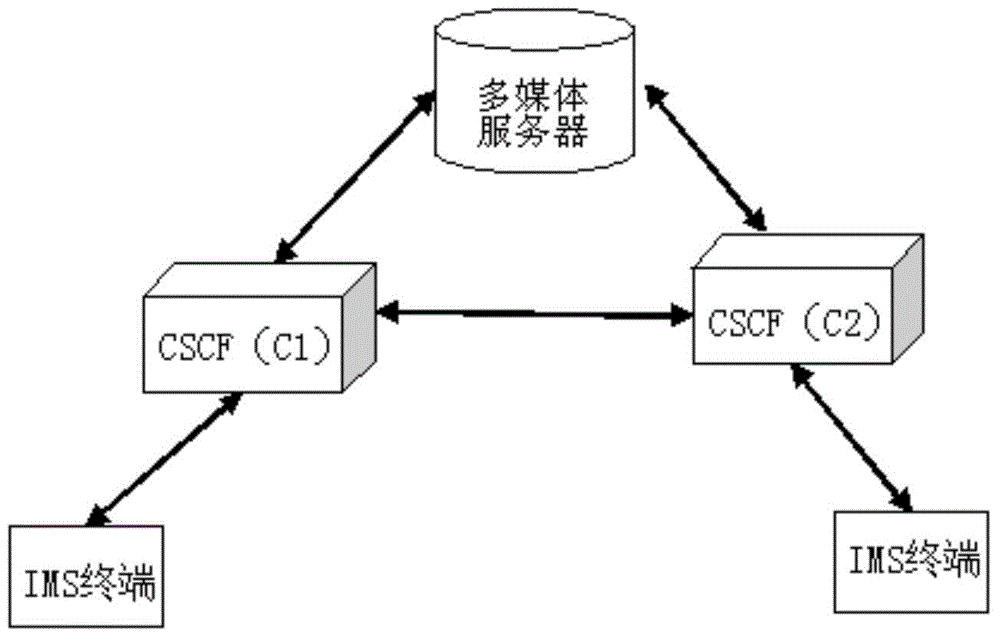
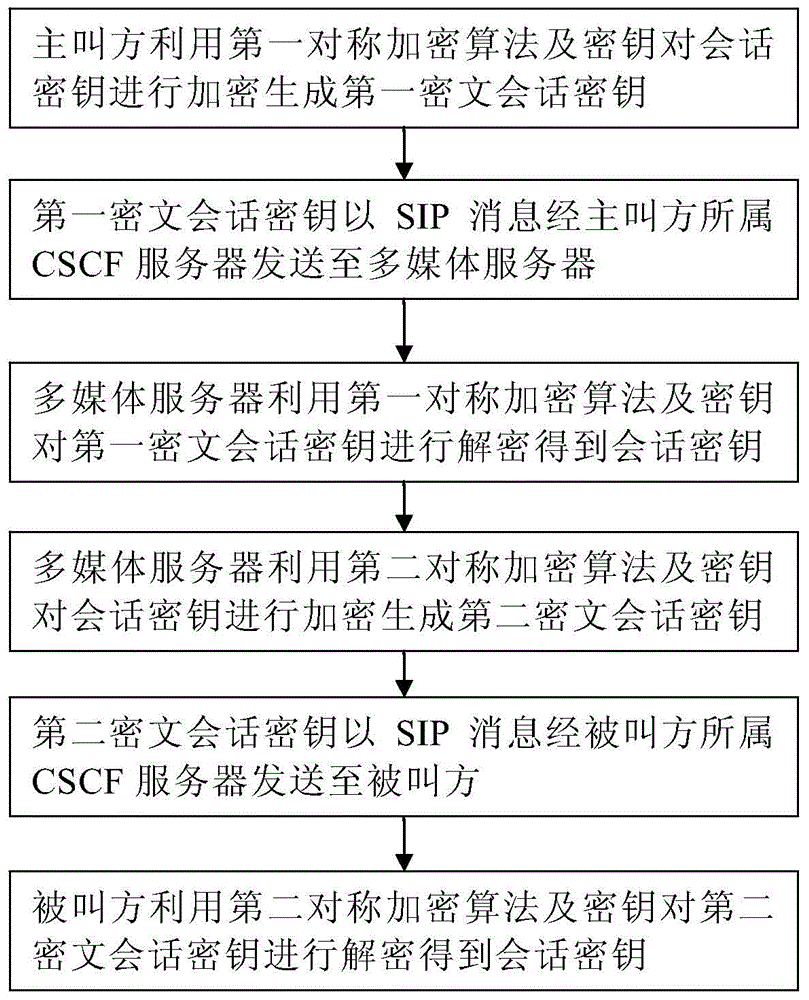
[0023] figure 2 It is a flow chart of the method of the present invention. As shown in the figure, the session key negotiation method based on the IMS system disclosed by the present invention is as follows: each terminal configures its own symmetric encryption algorithm and corresponding key in the multimedia server; Generate a session key, and use the configured first symmetric encryption algorithm and the corresponding key to encrypt the session key to generate the first ciphertext session key, and the first ciphertext session key is passed through the calling party in a SIP message The affiliated CSCF server transmits it to the multimedia server; the multimedia server receives the SIP message carrying the first ciphertext session key, and uses the first symmetric encryption algorithm configured by the calling party and the corresponding k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com