Authentication method based on USB-key
An authentication method and basic technology, applied in the usage of multiple keys/algorithms, user identity/authority verification, digital transmission systems, etc., can solve problems such as PIN code leakage, prevent PIN code leakage, avoid eavesdropping, improve safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
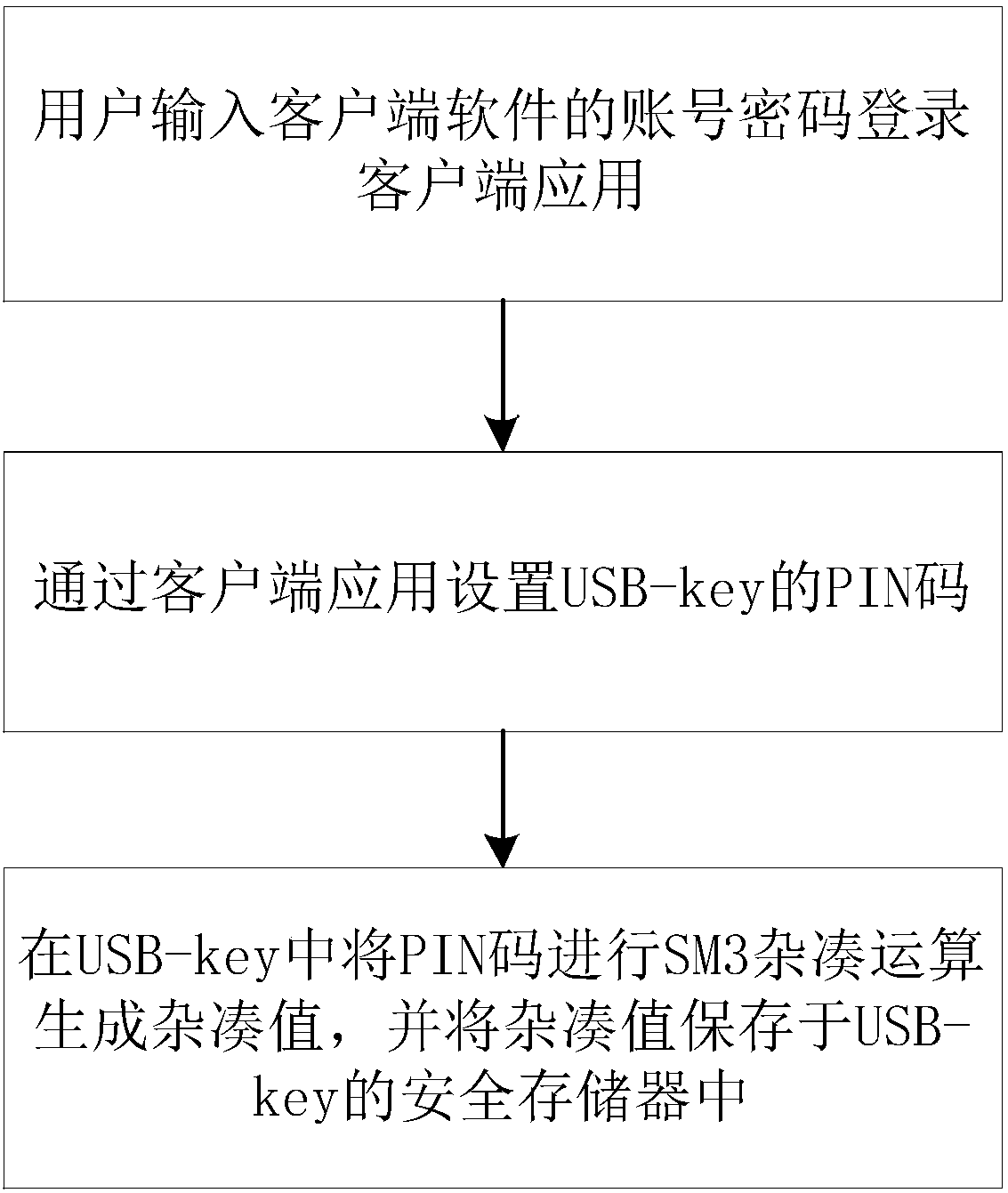
[0019] The present invention is described below in conjunction with embodiment.
[0020] According to an embodiment of the invention, a USB-key-based authentication method includes the steps of: establishing a basic verification system between the client and the USB-key based on PKI and generating a session key; presetting the first PIN code and calculating its corresponding hash value, store the hash value in the USB-key; the client obtains the second PIN code and outputs a verification instruction, encrypts the verification instruction based on the session key to obtain the first encryption code; USB-key analysis The first encryption code is used to obtain the verification instruction, a first random code is randomly generated, and the first random code is encrypted based on the session key to obtain a second encryption code; the client parses the second encryption code to obtain Obtaining a first random code, encrypting the first random code based on the hash value to obtai...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com