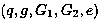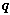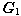Aggregation method and system for electricity privacy and integrity protection in smart grid
An integrity protection, smart grid technology, applied in transmission systems, digital transmission systems, digital data protection, etc., can solve the problems of fuzzy data characteristics, inability to accurately locate data integrity, and poor operability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0067] The present invention will be further described in detail below in combination with specific embodiments.
[0068] An aggregation method for electricity privacy and integrity protection in a smart grid, in which the smart meter installed in the user records and reports the user's electricity consumption in real time; the gateway with computing power is responsible for the data aggregation function and relay function ;The control center is responsible for collecting, processing and analyzing real-time power consumption data of each user, and providing reliable services; the trusted center is responsible for managing the entire system, the specific steps are as follows:
[0069] System initialization phase:
[0070] 1) The trusted center runs the following algorithm Gen(k) according to the input security parameter k to obtain the parameter , where q is a large safe prime of length k, and chooses the generator of the group G1 ;
[0071] Gen(k): Select two cyclic group...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com