Mode-based dynamic vulnerability discovery integrated system and mode-based dynamic vulnerability discovery integrated method
A technology that integrates systems and vulnerabilities, applied in the fields of software engineering and information security, can solve the problems of blind black-box testing, difficult static analysis, poor pertinence, etc., and achieve the effects of improving test coverage, easy expansion, and controllable vulnerability detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
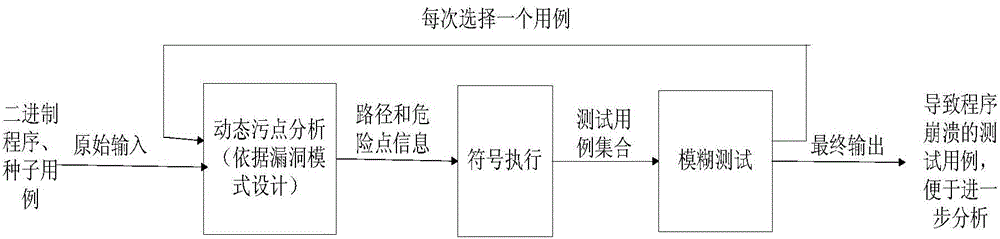
[0035] Such as figure 1 As shown, the present invention adopts the task pipeline mechanism to clarify the cross-validation relationship and mutual data support capabilities between different vulnerability mining technologies and tools, and organize the core process of vulnerability mining according to the pipeline mode according to the specific vulnerability mode. Finally, three technologies of dynamic taint analysis, symbolic execution and fuzz testing are integrated, and an integrated system of dynamic vulnerability mining for binary programs is realized.
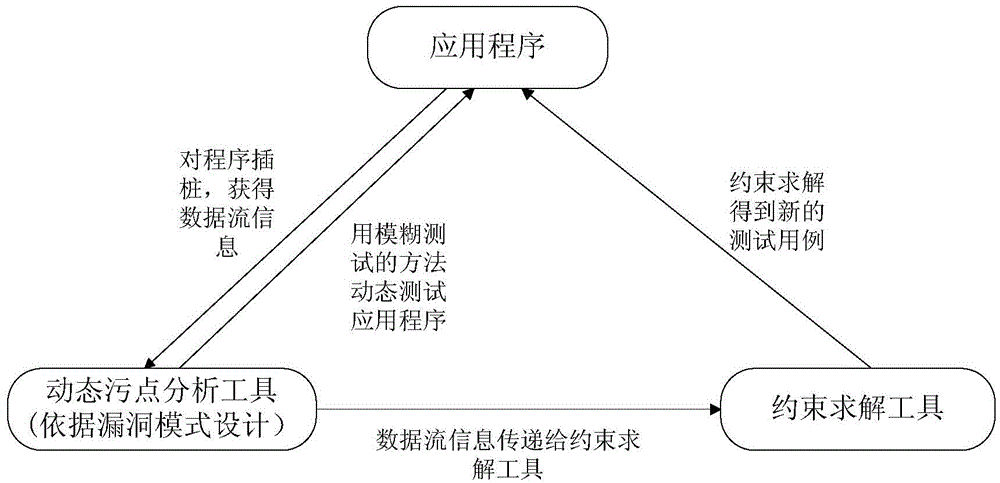
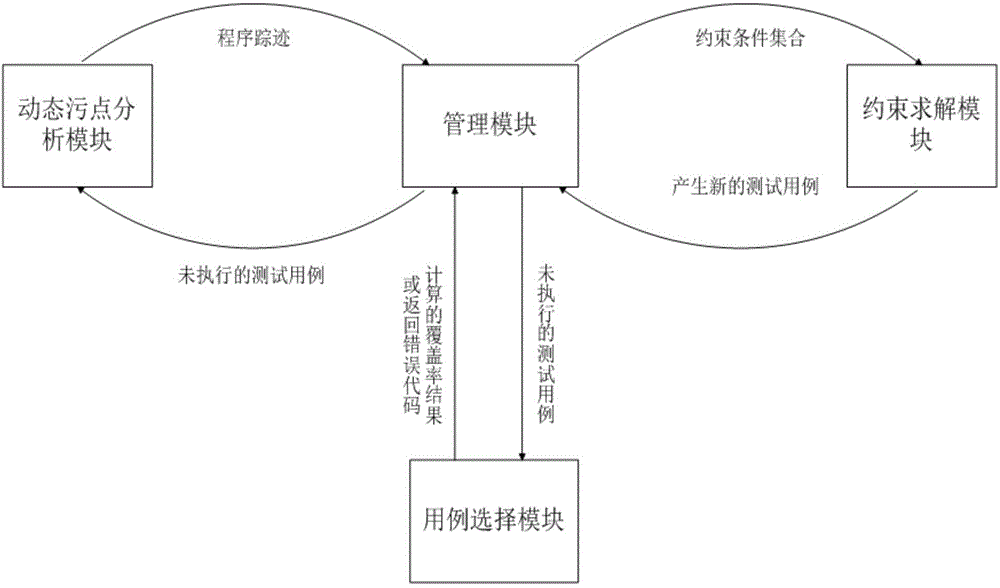
[0036] Functional structure of the present invention such as figure 2 As shown in , it presents the specific interaction and information transfer process among the system-integrated dynamic taint analysis technology, symbolic execution technology and fuzzing technology. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com