Malicious application program scanning method, device and system
A technology of malicious application program and scanning method, applied in the field of scanning method, device and system of malicious application program, capable of solving the problems of consuming user traffic, traffic charges, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0099] The embodiment of the present invention provides a method for scanning malicious applications, which is applied to the PC terminal side, and completes the cloud scanning and killing of malicious applications on the mobile terminal by connecting with the mobile terminal to save traffic.
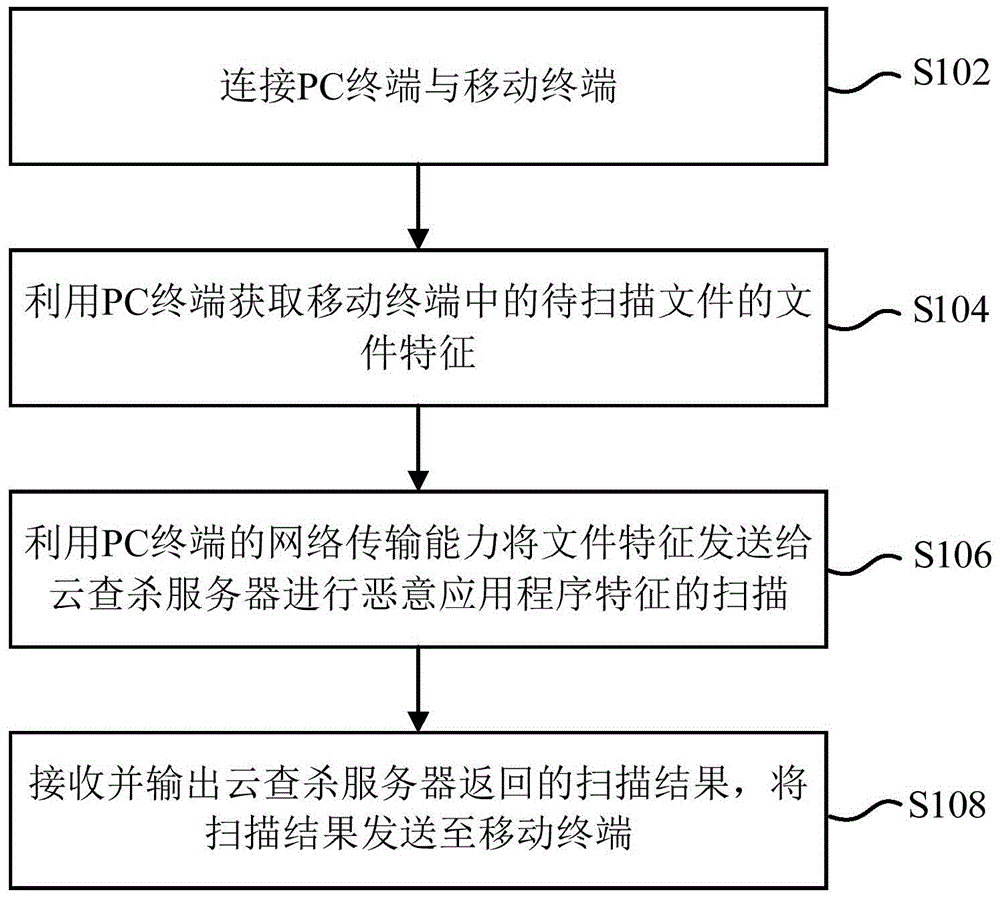
[0100] figure 1 It is a flow chart of a method for scanning malicious applications provided by an embodiment of the present invention, the method is applied to a PC terminal with network transmission capability, and includes steps S102 to S108:
[0101] S102: Connect the PC terminal and the mobile terminal.
[0102] S104: Using the PC terminal to acquire the file characteristics of the file to be scanned in the mobile terminal.
[0103] Specifically, specified features can be extracted from the Android installation package for detection, such as package name, version number, digital signature, etc., as specified features. Compared with the traditional antivirus engine on the Internet,...
Embodiment 2
[0118] An embodiment of the present invention provides a method for scanning malicious applications. The method is applied to the mobile terminal side, and through the connection with the PC terminal, it completes cloud scanning and killing of possible malicious applications in itself to save traffic.
[0119] In the present invention, the mobile terminal may be a mobile phone, a tablet computer and other devices.
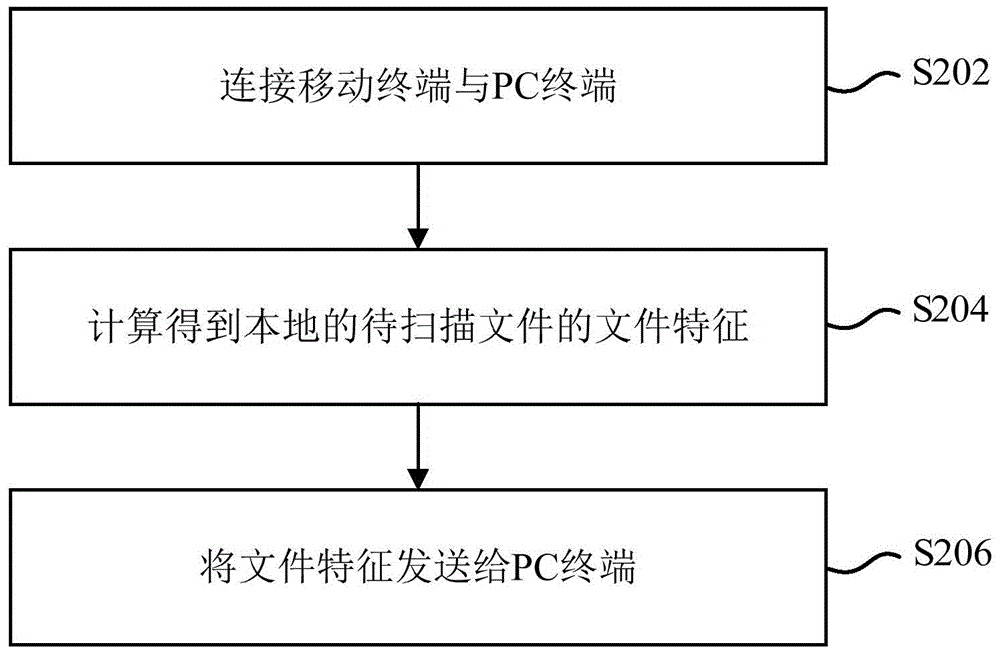
[0120] figure 2 It is a flow chart of a scanning method for a malicious application provided by an embodiment of the present invention, the method is applied to a mobile terminal, and includes steps S202 to S206:
[0121] S202: Connect the mobile terminal and the PC terminal.
[0122] S204: Calculate and obtain the file feature of the local file to be scanned.
[0123] S206: Send the file feature to the PC terminal.
[0124] Wherein, the file feature is used for the PC terminal to upload to the cloud scanning and killing server for the cloud scanning and killin...
Embodiment 3
[0128] The method for scanning malicious application programs provided by the present invention is implemented through the cooperation of PC terminals and mobile terminals, wherein, the first embodiment describes the scanning method for malicious application programs on the side of the PC terminal, and the second embodiment describes the method for scanning malicious application programs on the side of the mobile terminal. This section describes how to scan malicious applications.
[0129] Embodiment 3 is a specific application scenario of Embodiment 1 and Embodiment 2 above, and will be described in combination with PC terminal and mobile terminal side. Through this embodiment, the method provided by the present invention can be described more clearly and specifically.
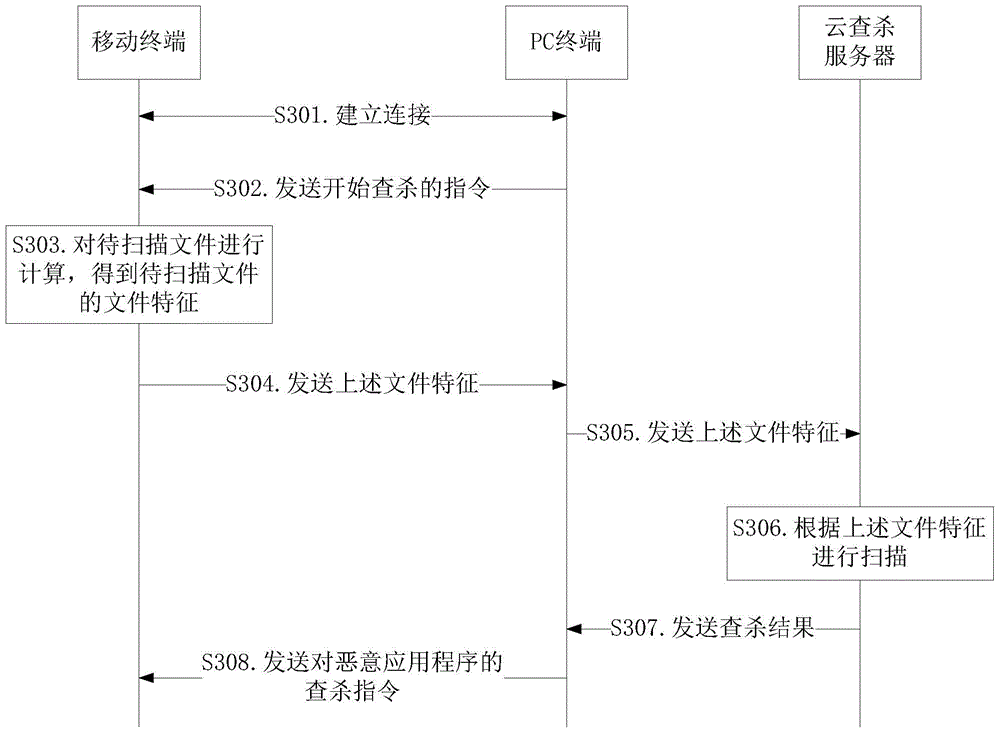
[0130] Such as image 3 As shown, it is a specific flowchart of a scanning method for a malicious application provided by an embodiment of the present invention, including steps S301 to S308.
[0131] In step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com