Android system security verification method and verification device thereof
An Android system and verification method technology, applied in the field of technical security, can solve the problems of rapid expansion of the upgrade differential package size, waste of upgrade download traffic resources and speed resources, etc., and achieve the effect of improving system fluency, reducing impact, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] Android system security verification method embodiment:
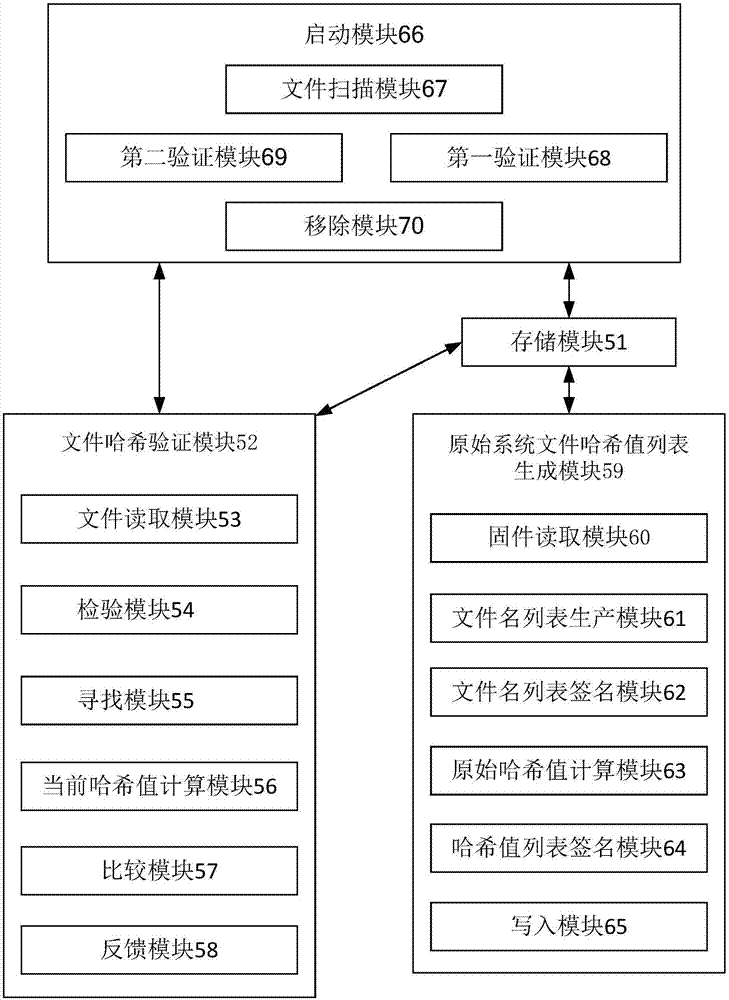
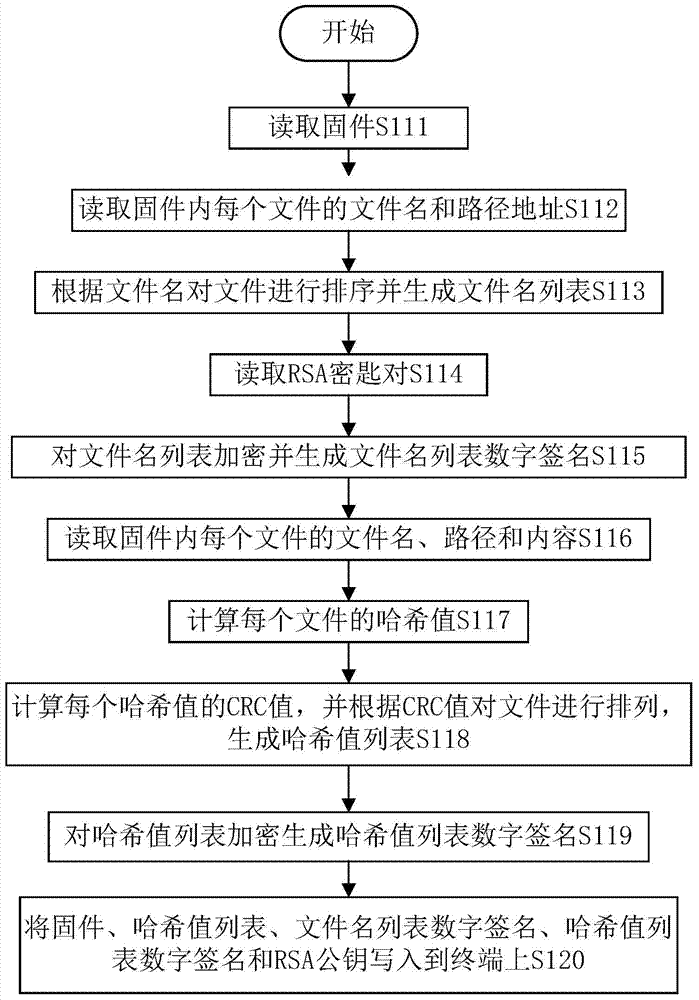
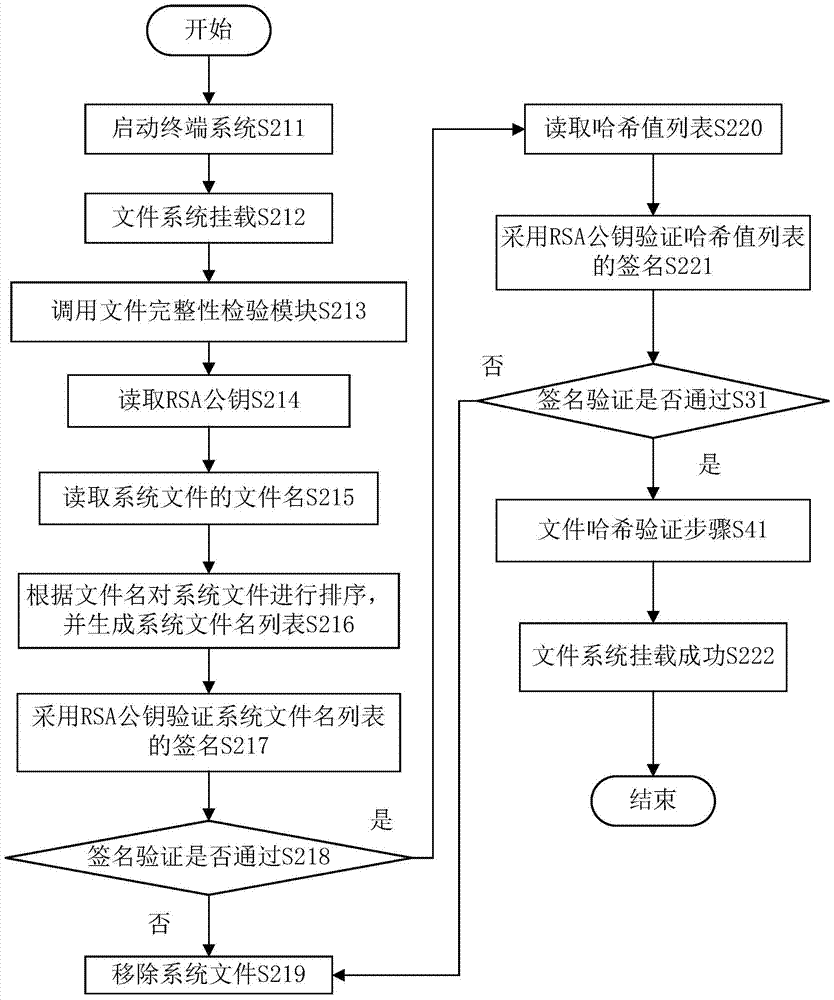
[0024] refer to figure 1 , figure 1 is a flowchart of the steps of generating the hash value list of the original system file. The original system file hash value list generation step includes, first execute step S111, read all files in the firmware, then execute step S112, read the file names and path addresses of all files in the firmware, and then execute step S113, according to the file name pair Files are sorted and a list of original system filenames is produced with filename key information.
[0025] Then execute step S114, read the RSA key pair, then execute step S115, use the RSA private key to encrypt the original system file list and generate the digital signature of the original system file list. Then execute step S116, read the file name, path and file content of all files in the firmware, then execute step S117, calculate the hash value according to the file name, path and file content of each fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com