System and method for identifying and preventing DDoS attacks on basis of SDN framework
A technology of SDN architecture and protection system, applied in the field of network security, can solve problems such as network security, achieve the effect of reducing coupling correlation, efficient detection and flexible processing, and improving high cohesion characteristics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Embodiment 1 is a technical solution for a DDoS attack identification and protection system.
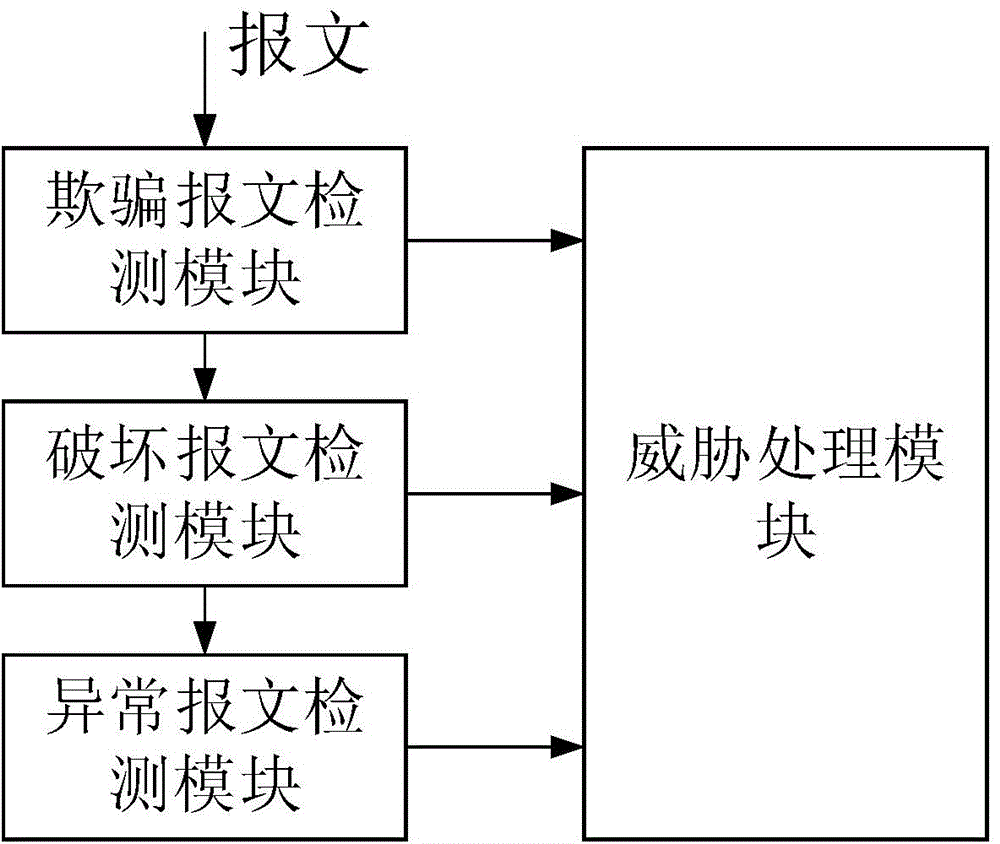
[0057] figure 2 It shows the functional block diagram of the DDoS attack identification and protection system based on the SDN architecture.
[0058] Such as figure 2 As shown, a DDoS attack identification and protection system based on SDN architecture includes: a controller, which includes: a fraudulent message detection module, a corrupted message detection module, an abnormal message detection module, and a threat processing module.
[0059] The spoofed message detection module detects spoofing behavior of link layer and Internet layer addresses.
[0060] The corrupted message detection module detects the abnormal behaviors set by the flag bits of the Internet layer and the transport layer.
[0061] The abnormal packet detection module detects the flood attack behavior of the application layer and the transport layer.
[0062] The fraudulent message detection module,...
Embodiment 2
[0146] The method for identifying and protecting DDoS attacks based on the SDN architecture based on Embodiment 1 solves the technical problem of effectively defending against DDOS attacks.
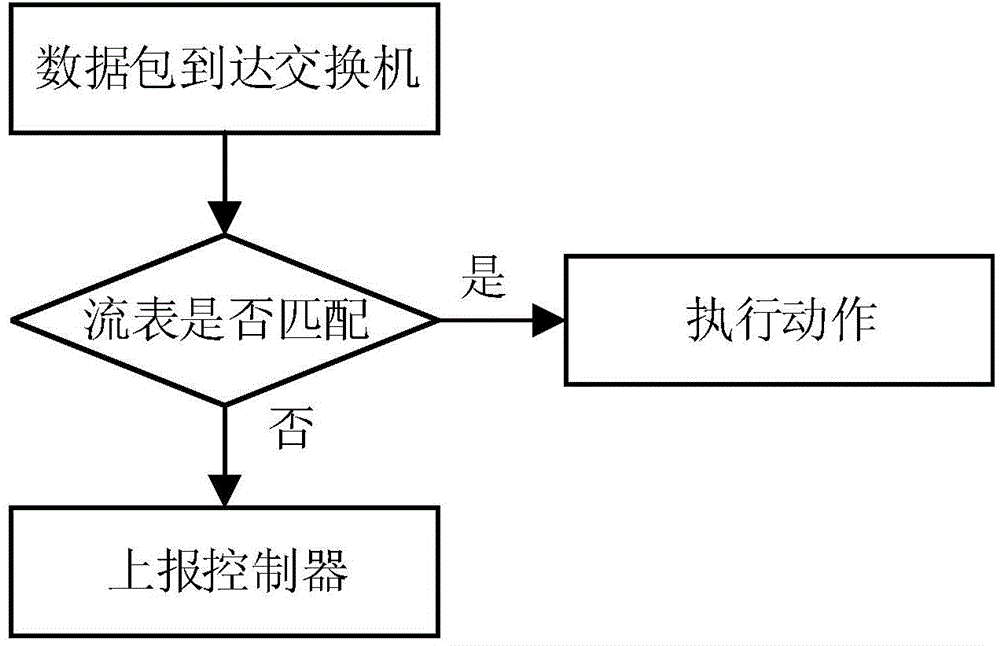
[0147] The method of described DDoS attack identification and protection method comprises: the spoofing behavior of link layer and Internet layer address, the abnormal behavior of Internet layer and transport layer flag position setting, and the flooding type attack behavior of application layer and transport layer are detected successively ; If any detection step in the above process determines that the message has a corresponding behavior, then transfer the message to the threat processing module to discard the message and shield the program and / or host that sent the message.
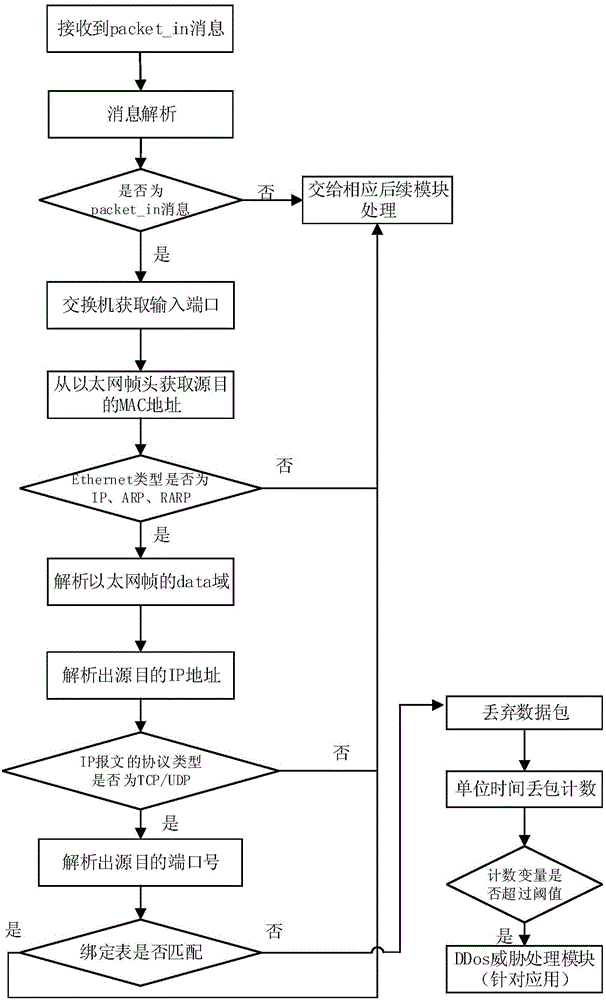
[0148] Figure 8 A flow chart of a DDoS attack identification and protection method based on the SDN architecture is shown.
[0149] Such as Figure 8 As shown, the specific implementation steps include:
[01...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com