Administrative user abnormal behavior detection method based on big data log analysis
A discovery method and user management technology, applied in special data processing applications, electrical digital data processing, instruments, etc., can solve problems such as incompetence in log analysis, and achieve the effects of easy promotion, strong practicability, and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
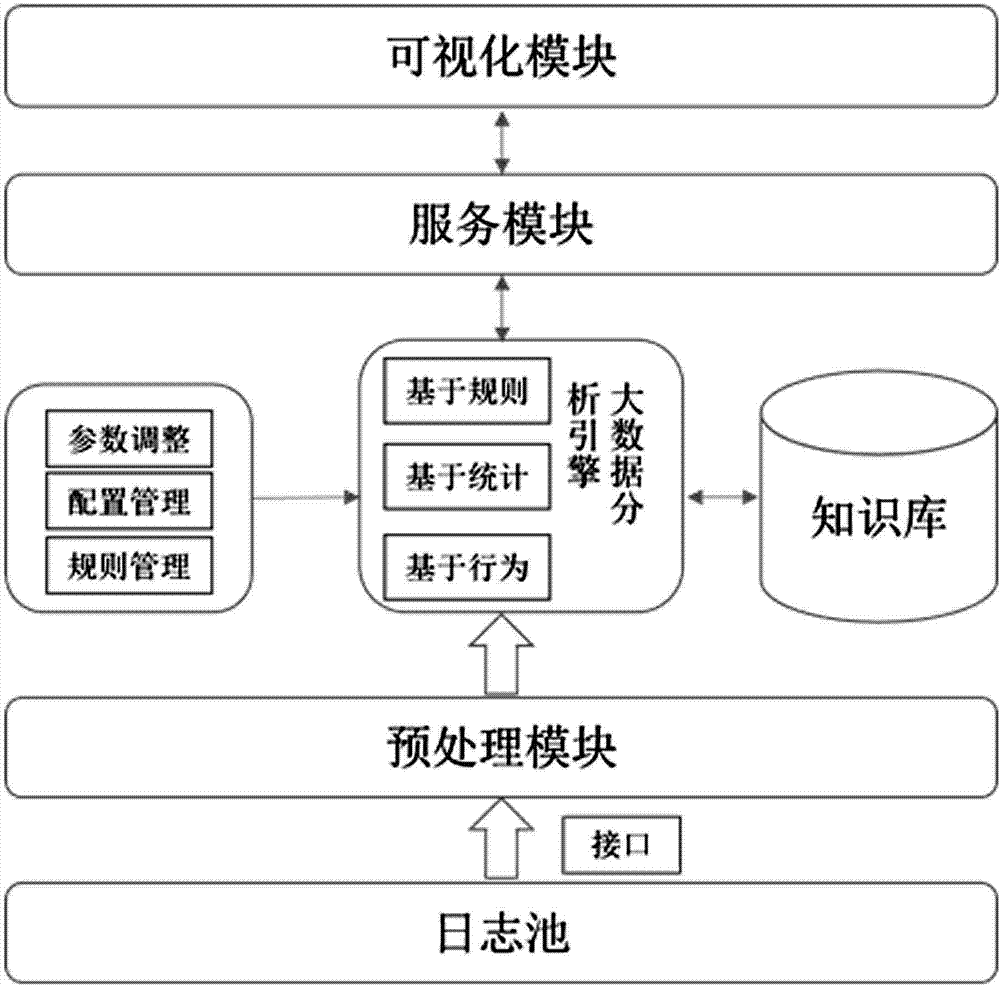
[0024] The present invention provides a method for discovering abnormal behaviors of management users based on big data log analysis. The big data processing framework is used to deeply mine and analyze the management logs of the internal management personnel of the information system to discover the abnormal behavior of the management personnel, that is, to discover the abnormality of the management personnel. Behaviors and illegal operations, and trace the source of abnormalities. as attached figure 1 As shown, the specific implementation process is:
[0025] 1. The logs to be analyzed are stored in the log pool;
[0026] Two, the log pool is connected to the preprocessing module through the interface module, and the log in the log pool enters the preprocessing module to complete the log preprocessing, that is, the actions of cleaning and i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com