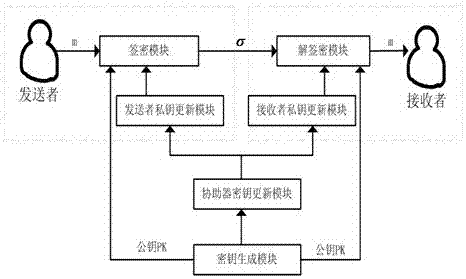
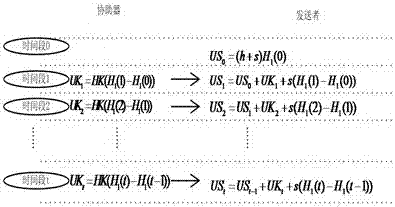
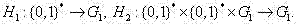A key isolation signcryption method
A key and signcryption technology, applied in the field of communication, can solve the problems of non-repudiation, forward security and public verifiability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] If Alice writes a letter, she signs the letter, then puts the letter in an envelope, and if she puts a letter without a signature in the envelope and signs the envelope, then Bob, the recipient, has reason to fear that the letter has been Instead, if Bob shows Carol Alice's letter and envelope, Carol may sue Bob for lying because the letter is not in the right envelope. Therefore, it is natural to sign before encryption. The digital signature with encryption combines the public key algorithm and digital signature Combined, unforgeability, non-repudiation, and confidentiality of communications are simultaneously achieved. However, once the private key of Alice or Bob is leaked, all their previous or subsequent operations will no longer be safe. Therefore, the present invention introduces a key isolation mechanism, and the entire life cycle of the system is divided into discrete N time segments. Throughout the life cycle, the public keys of Alice and Bob remain unchanged,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com