Modeled software key behavior tracking method based on memory management
A technology of memory management and behavior, which is applied in the field of computer information security and information security, can solve problems such as increasing the workload of developers, reducing management flexibility, and affecting normal operation, so as to improve flexibility and adaptability, and improve adaptability , to avoid the effect of defining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The specific embodiment of the present invention will be described in further detail below with reference to the accompanying drawings.
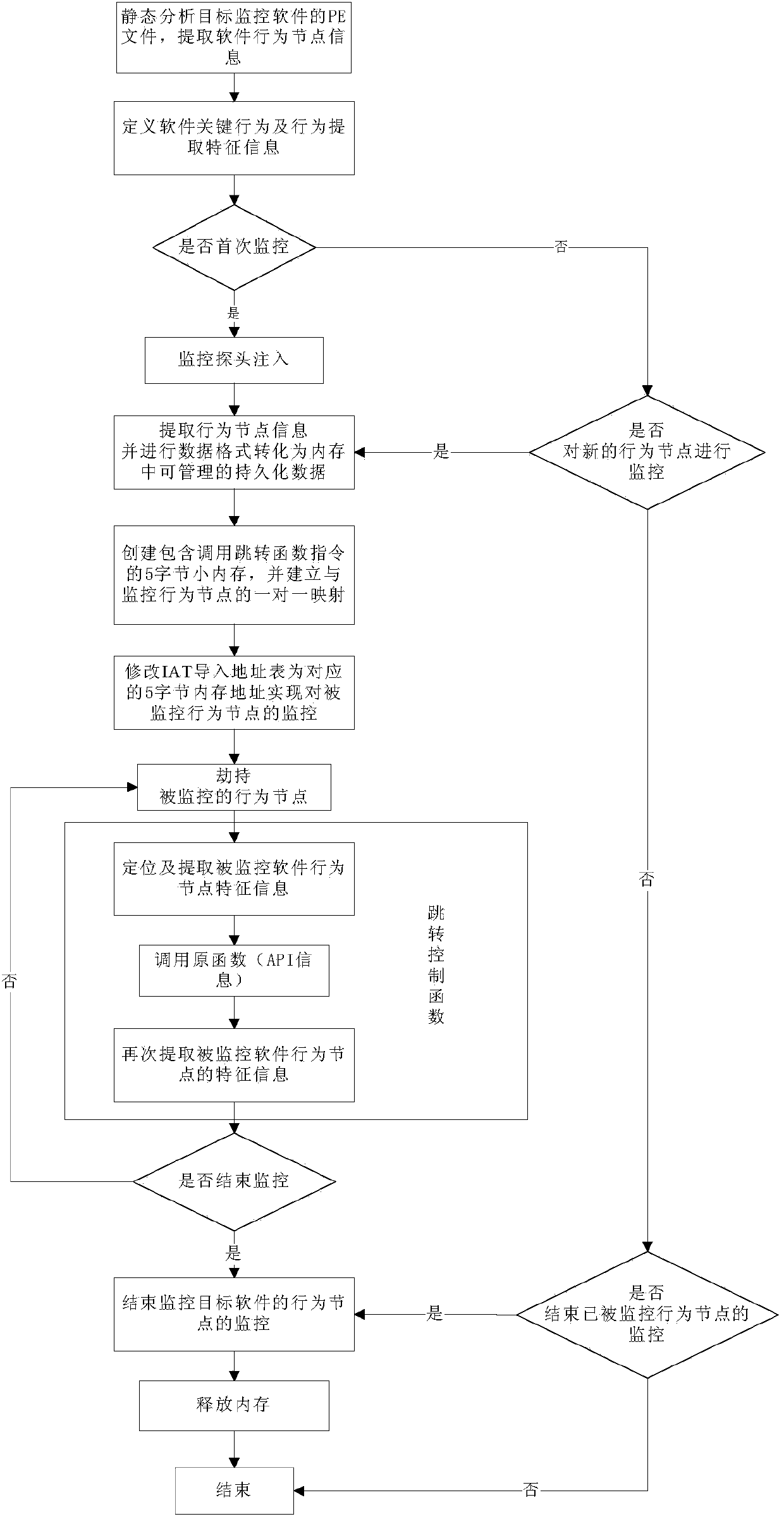
[0052] Such as figure 1 As shown, a method for tracking key behaviors of patterned software based on memory management in the present invention, the specific implementation steps are as follows:
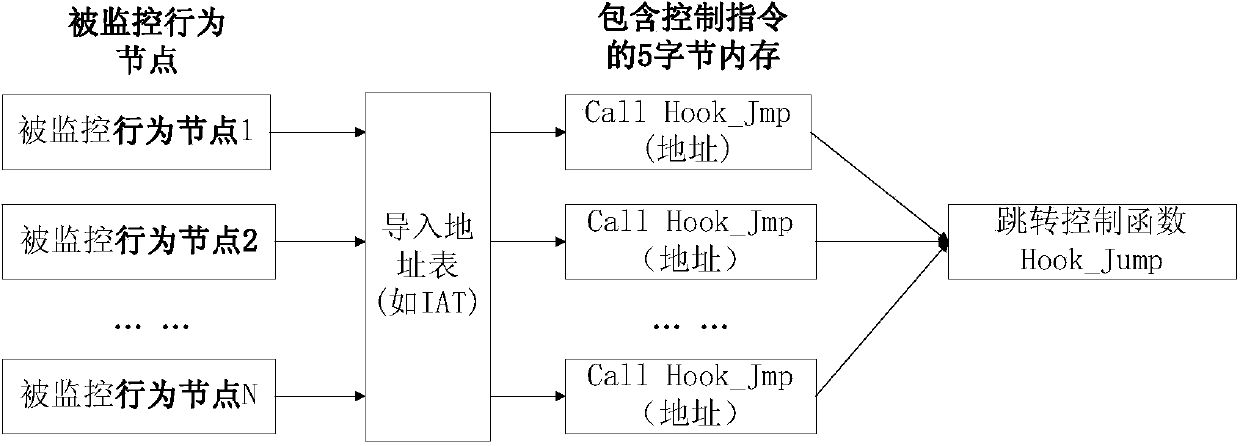
[0053] (1) The monitoring console first loads the PE file of the monitoring target software, and analyzes the behavior node information of the PE file through static mapping; the behavior node information refers to the operating system and other user-defined APIs referenced by the PE file Information, behavior node information is stored in the IAT import address table of the PE file;
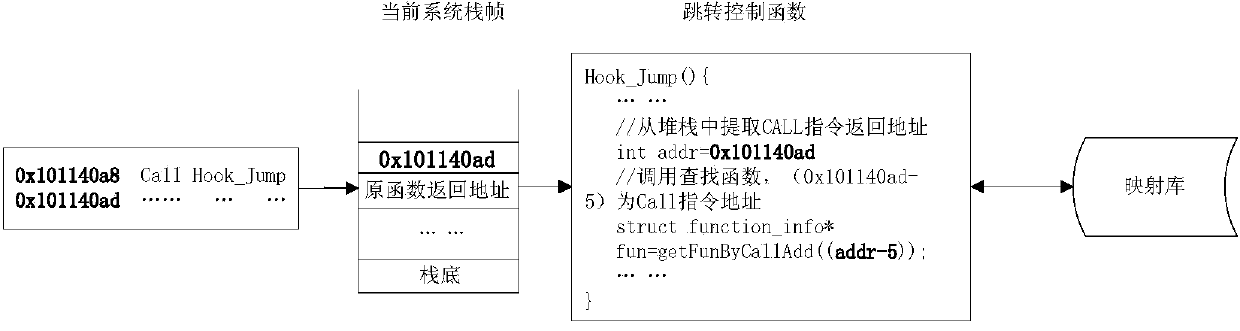
[0054] (2) According to the behavior node information obtained in step (1), the key behavior of the monitoring software is formed by adding and removing behavior nodes and stored in the database, and the key behavior feature information to be extracted is det...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com