Personal code managing tool and method under open cloud platform
A technology for password management and management tools, which is applied in the field of open platform authorization mechanisms to achieve real-time maintenance and management, good cross-platform performance, and improved security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
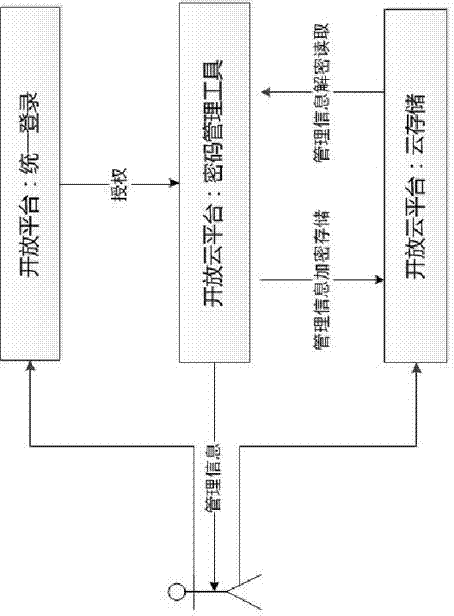
[0032] like figure 1 As shown, a personal password management tool under the open cloud platform includes: a third-party authorized login module, a management tool design and development module, a data information encryption and decryption module, and a user data cloud storage module for development and implementation, wherein:
[0033] The third-party authorized login module, which authenticates the user's identity, creates an open platform application based on the current large-scale user volume of Internet products, and implements the development of the third-party authorized login function through the API interface provided by it. When the user successfully completes the authorized login Then, record the attribute value used to uniquely identify the user's identity, and use this attribute value to generate a key for encrypting the management personal information content. (Note: When choosing third-party product support, you need to choose a product that provides cloud stor...
Embodiment 2
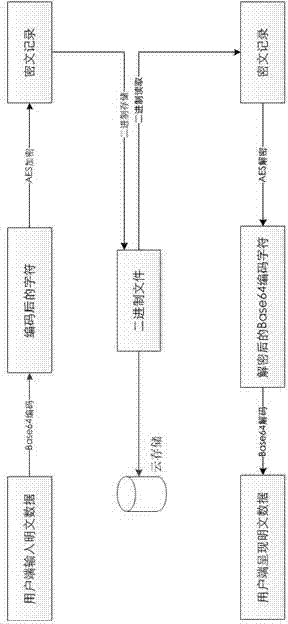
[0038] In the data information encryption and decryption module, at the same time, considering that the management tool requires high real-time performance, the encryption and decryption time needs to be controlled at the millisecond level, therefore, the core encryption algorithm of the module is AES. The specific implementation steps are:
[0039] 1. Format the record content entered by the user as a string;
[0040] 2. Base64 encode the formatted string;
[0041] 3. For the encoded characters, use the HASH value generated by the user's unique identity identifier as the key, and generate the ciphertext through the AES encryption algorithm;
[0042] 4. The ciphertext is stored in a binary stream;
[0043] The decryption process is the opposite of the encryption process, and the specific implementation steps are as follows:
[0044] 1. Read binary files as binary streams;
[0045] 2. Decrypt the read ciphertext records through the AES algorithm;
[0046] 3. Perform Base64...
Embodiment 3
[0049] The third-party authorization login module adopts the OAuth2.0 method generally provided by the current major third-party open platforms for authentication.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com