A wireless information security equipment system and security protection method
A technology for information security, wireless transceiver equipment, applied in the direction of program/content distribution protection, etc., can solve the problems of computer crash, stealing user privacy or other data information, data loss, etc., to achieve the effect of improving convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment 1
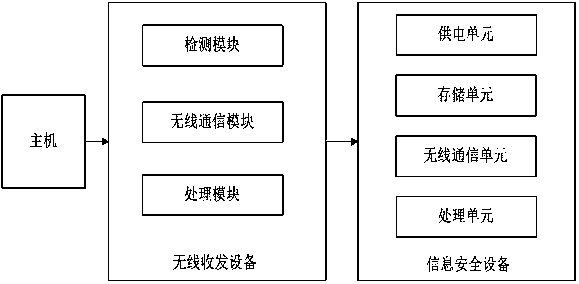
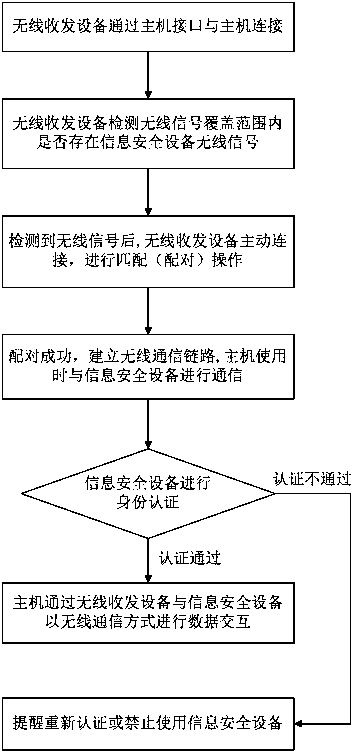
[0076] In this embodiment, the wireless transceiver device is a mini USB receiver similar to that used by a wireless mouse (hereinafter referred to as the receiver). It is connected with the computer, and the wireless communication module / unit in the wireless transceiver device and the information security device is Bluetooth (Bluetooth). It is assumed that the transmission distance is set to 3M in this embodiment.
[0077] There is software A on the host computer of the user. When using software A, the dongle needs to be called to return the data or command value required for operation. The user needs to carry the dongle with him (for example, it can be placed in a briefcase, pocket, key chain, etc.). According to an embodiment of the present invention, the specific implementation steps are:
[0078] 1. The receiver automatically detects whether there are other Bluetooth devices within its wireless signal coverage through the built-in Bluetooth communication module;
[0079]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com