RFID (radio frequency identification) digital information read-write security control method and device, and reader-writer
A technology of security control and digital information, applied in the field of data information security, can solve problems such as major security and hidden dangers, and achieve the effect of ensuring security and avoiding the impact of security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 4
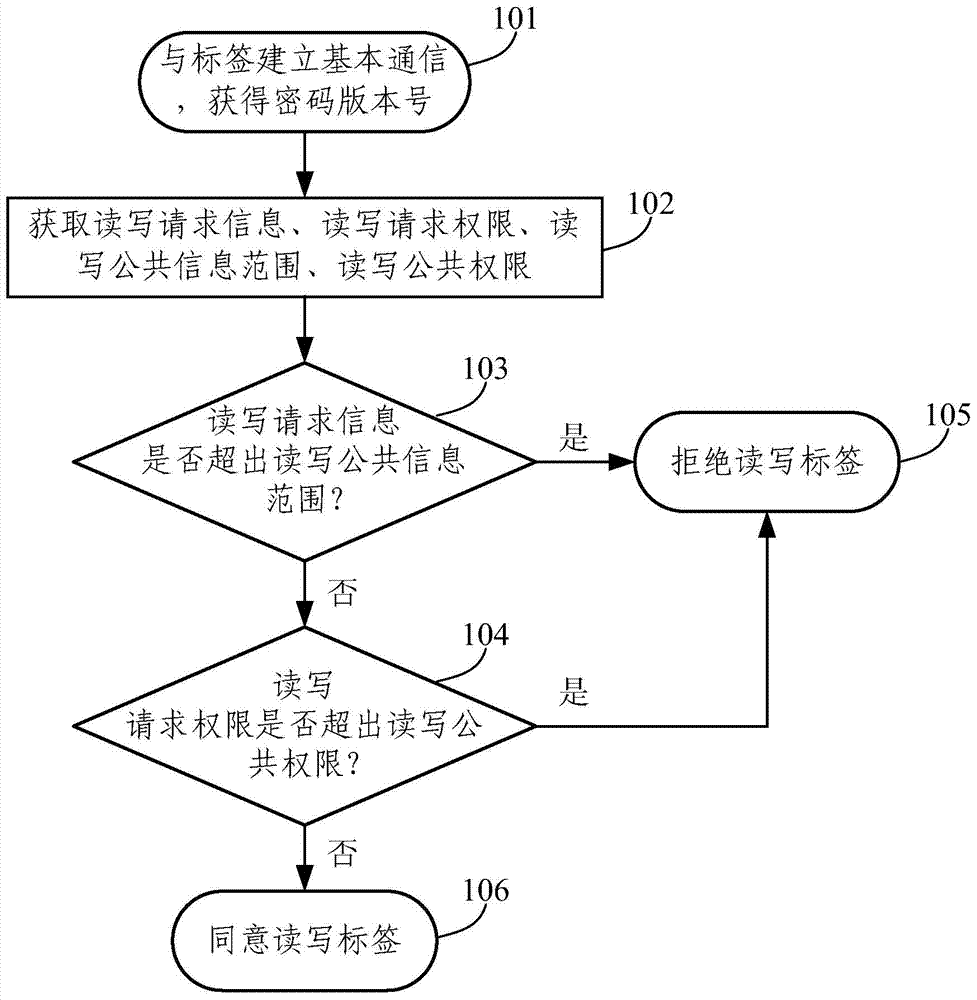
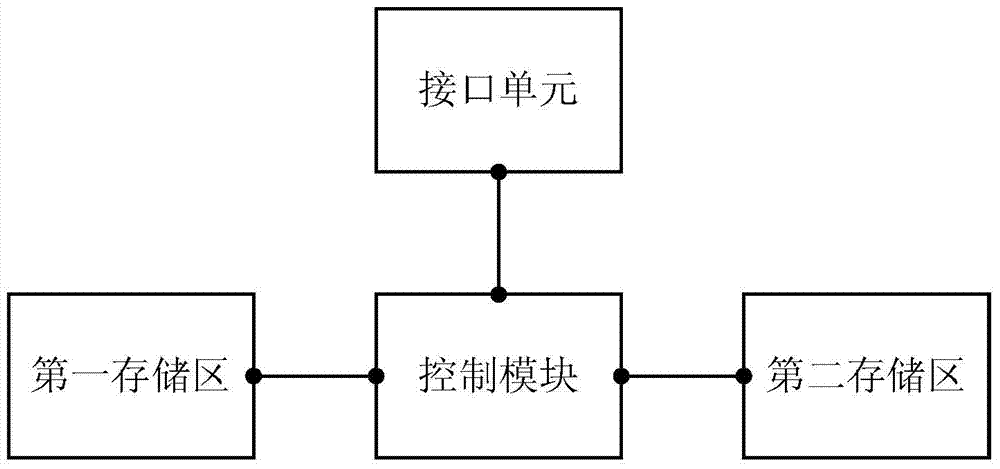
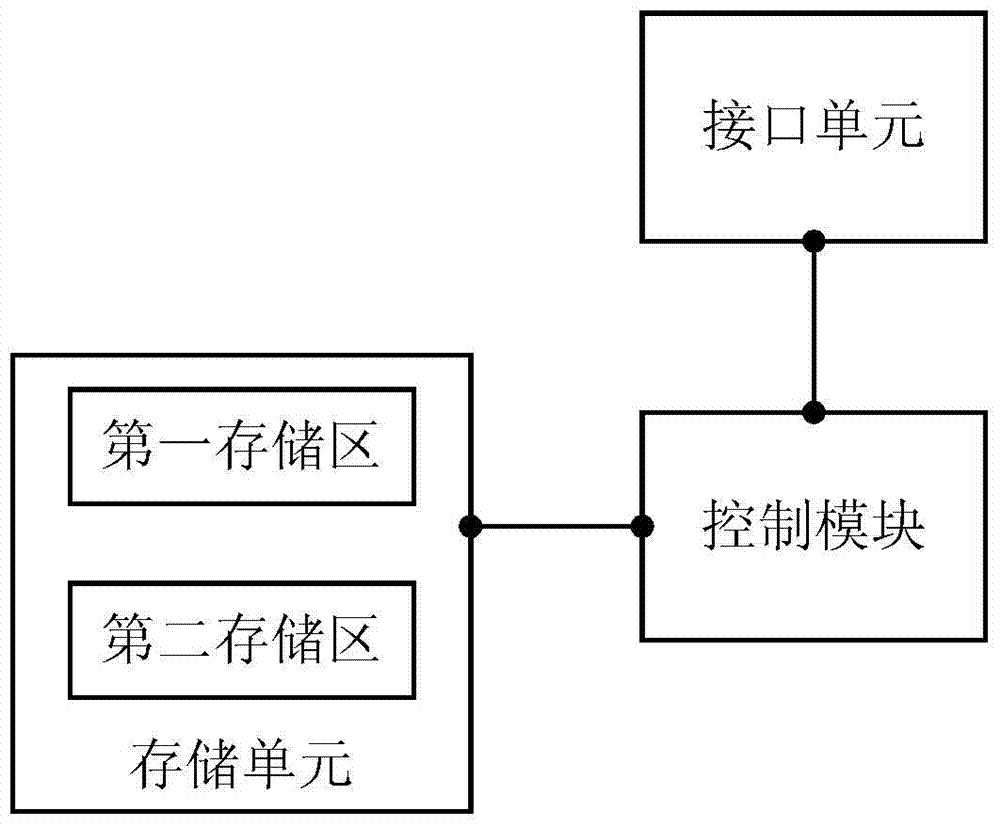
[0104] The present invention also provides RFID reader-writer, as Figure 5 As shown, it includes a communication module connected to the central processing unit CPU and any read-write safety control device as described above;
[0105] The communication module includes an RF radio frequency interface and a remote communication module. The RF radio frequency interface establishes a communication connection with the label and performs read and write operations to the label. The remote communication module is used to communicate with the central information system in a wired or wireless manner. Any one of RJ232 interface, RJ45 interface or RS485 interface, or any one of wireless Bluetooth interface, infrared interface, WIFI interface, ZIGBEE interface, CDMA interface or LTE interface.
[0106] It should be pointed out that the control module of the above-mentioned read-write security control device is a logical structural unit. In order to save hardware expenses, the functions of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com