A flow backup method and device
A device and backup technology, applied in the field of communication, can solve the problems of unable to monitor user-side traffic, not realizing user-side traffic backup, not providing user-side traffic backup, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
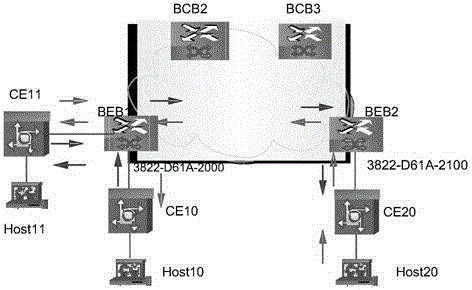
[0048] An embodiment of the present invention provides a traffic backup method, and describes the connection between a monitoring CE device and a monitored CE device connected to the same BEB device. In this embodiment, the monitoring CE device is connected to the monitoring server and the BEB device respectively, and the monitored CE device is connected to the monitored host and the BEB device respectively. by figure 1 It is a schematic diagram of an application scenario of the embodiment of the present invention, Host11 is a monitoring server, Host10 is a monitored host, CE11 is configured as a monitoring CE device, and CE10 is configured as a monitored CE device.
[0049] Further, the AC (Attachment Circuit, access link) between the monitored CE device and the BEB device is divided into two types: the monitored AC and other ACs. The monitored AC is used to transmit the packets corresponding to the monitored host, and the other AC is used to transmit messages corresponding ...
Embodiment 2
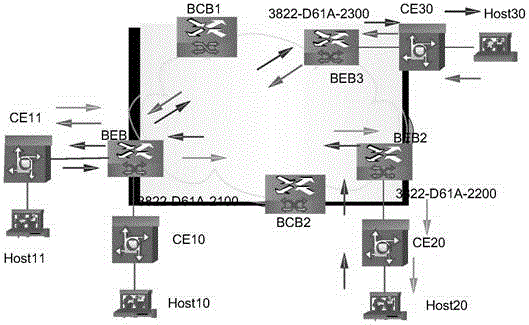
[0093] An embodiment of the present invention provides a traffic backup method, and describes the connection between a monitoring CE device and a monitored CE device connected to different BEB devices. In this embodiment, the monitoring CE device is connected to the monitoring server and the first BEB device respectively, and the monitored CE device is connected to the monitored host and the second BEB device respectively. by image 3 It is a schematic diagram of the application scenario of the embodiment of the present invention, Host11 is a monitoring server, Host20 is a monitored host, CE11 is configured as a monitoring CE device, and CE20 is configured as a monitored CE device; in addition, BEB1 is the first BEB device, and BEB2 is the second BEB equipment.
[0094] Further, the AC between the monitored CE device and the second BEB device is divided into two types: the monitored AC and other ACs. The monitored AC is used to transmit messages corresponding to the monitored...
Embodiment 3
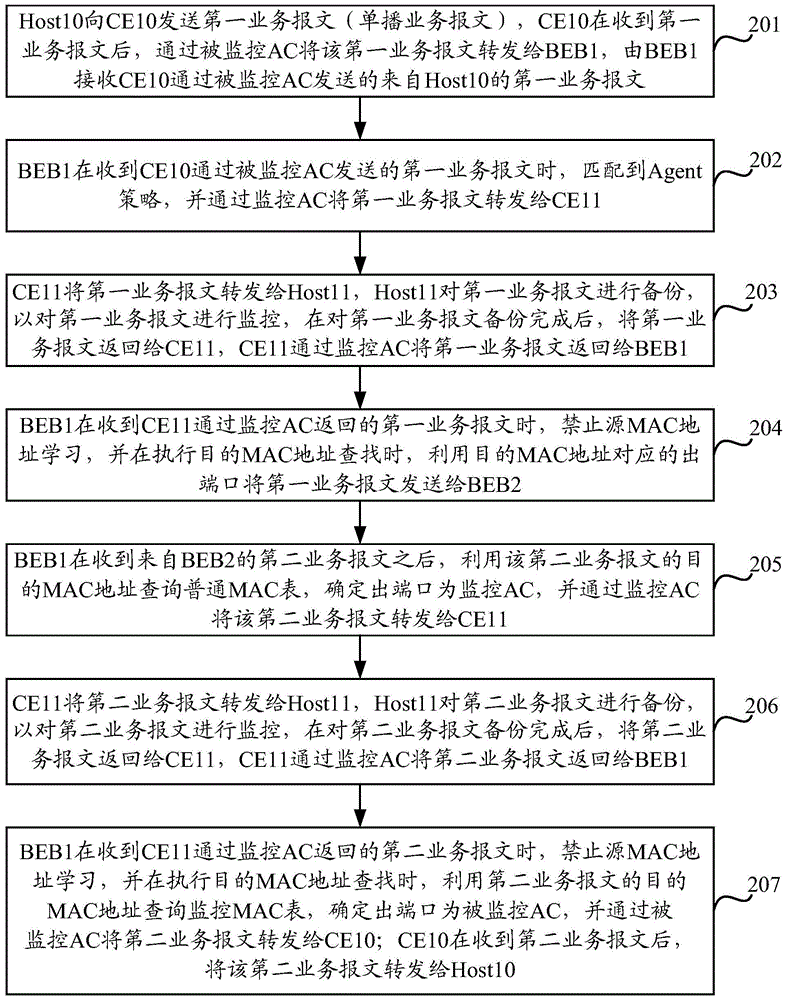
[0158] Based on the same inventive concept as the above method, an embodiment of the present invention also provides a backbone network edge bridge BEB device, which is applied to a network including a monitoring user network edge CE device, a monitored CE device, and the BEB device. The monitoring CE equipment, the monitored CE equipment is connected to the BEB equipment, such as Figure 5 As shown, the BEB equipment specifically includes:
[0159] The maintenance module 11 is used to configure the Agent strategy, and maintain the monitoring media access control MAC table and the common MAC table; the Agent strategy is used to make the BEB device receive the message sent by the monitored CE device through the monitored access link AC, The packet is forwarded to the monitoring CE device through the monitoring AC; the monitoring MAC table is used to record the correspondence between the MAC address of the monitored host and the monitored AC; the ordinary MAC table is used to re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com