Hardware Trojan horse detection method and hardware Trojan horse detection system
A technology of hardware Trojan detection and hardware Trojan, applied in the direction of platform integrity maintenance, etc., can solve the problem of low resolution of hardware Trojan detection, achieve the effect of improving detection resolution and detection efficiency, simple algorithm, and short detection time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
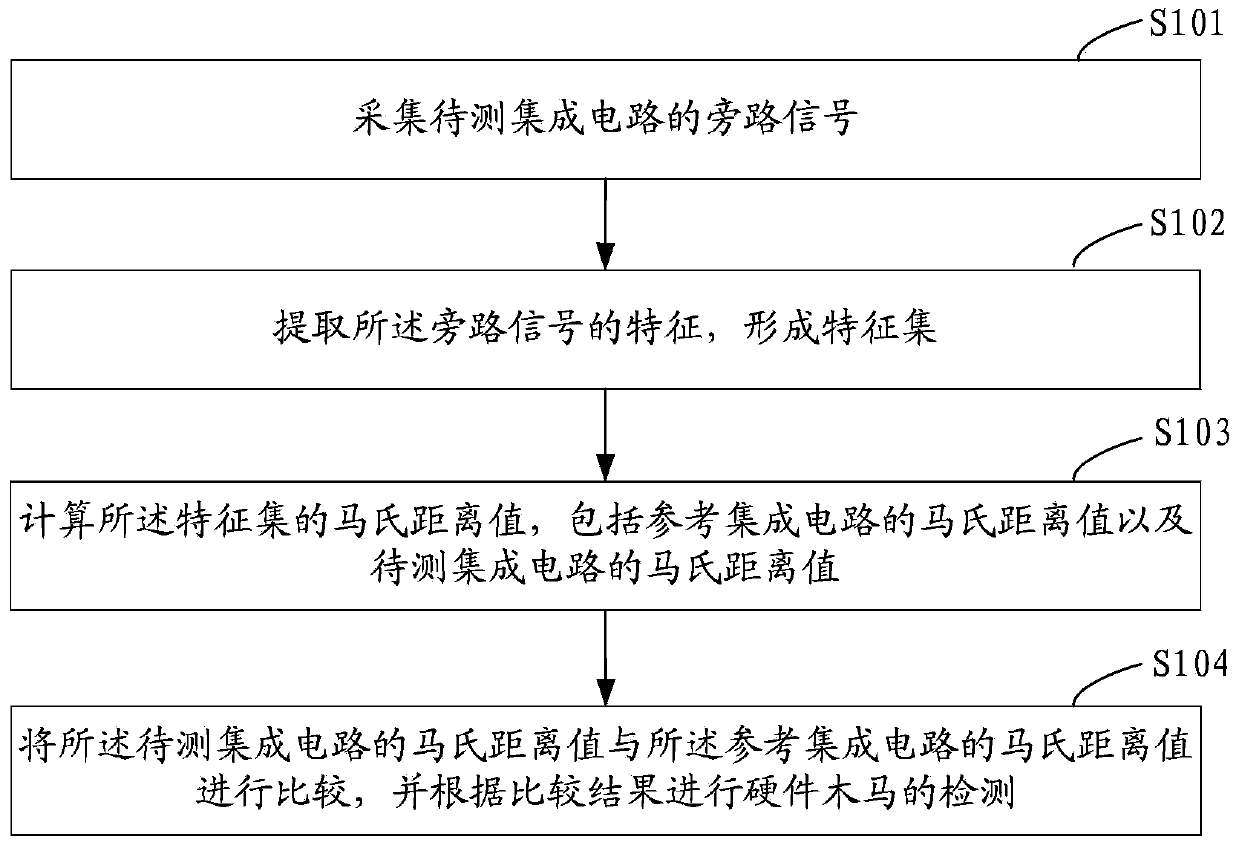
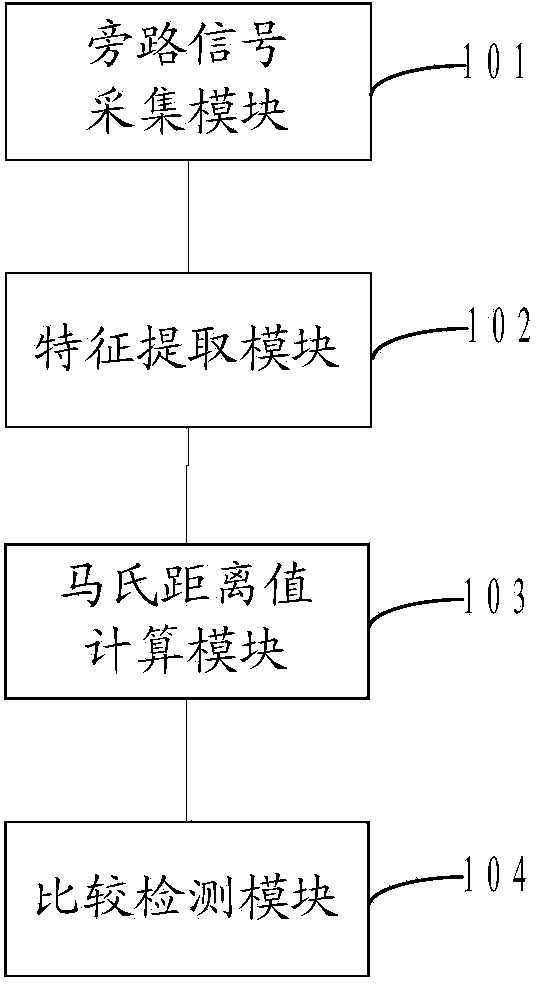
[0022] see figure 1 Shown, a kind of hardware Trojan detection method comprises the following steps:
[0023] Step S101, collect the bypass signal of the integrated circuit under test, and then go to step S102.
[0024] As a better embodiment, the bypass signal collected in the embodiment of the present invention may include the following: heat signal, electromagnetic radiation signal, power consumption signal, time delay signal, quiescent current signal, transient power supply current signal, etc., the following Common instruments suitable for these bypass signal measurements are listed in Table 1.
[0025] Table 1 Bypass signals of integrated circuits and their measuring instruments
[0026]
[0027]
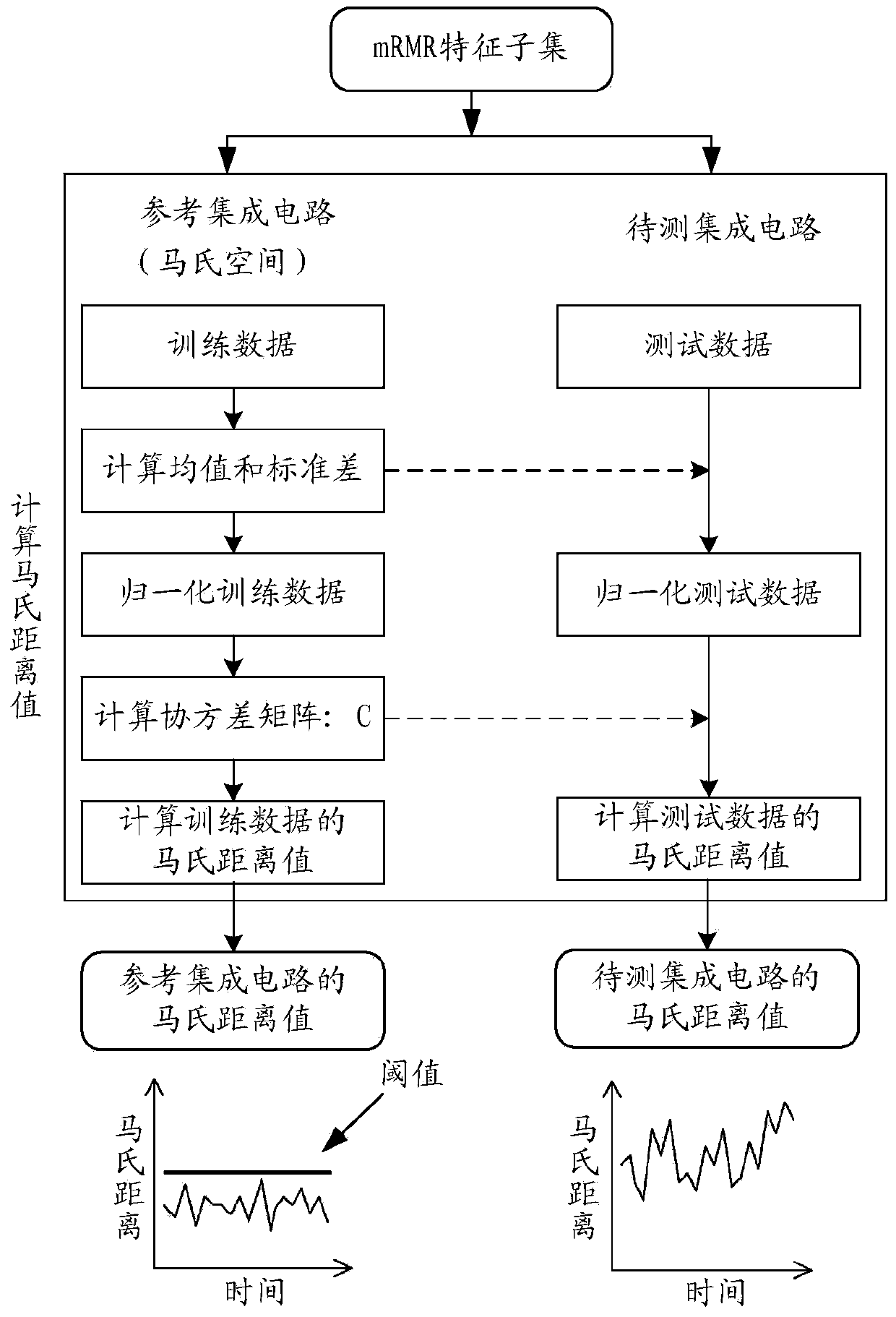
[0028] Step S102, extracting features of the bypass signal to form a feature set, and then proceed to step...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com