Abnormity monitoring method and abnormity monitoring device
An abnormality monitoring and abnormality technology, applied in the computer field, can solve the problems that the system operating environment cannot be monitored, cannot realize automatic monitoring, etc., and achieves the effect of being convenient to carry.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
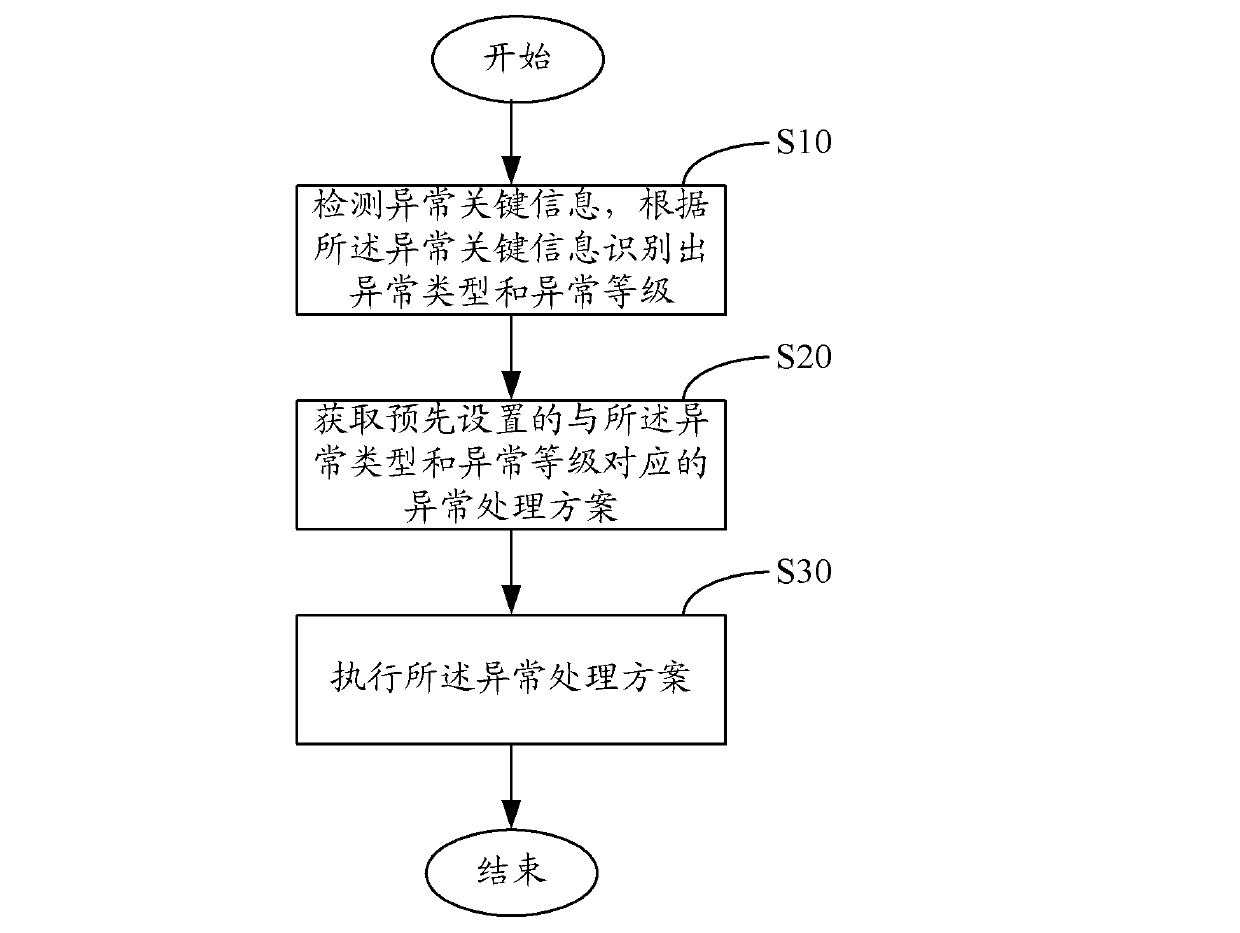
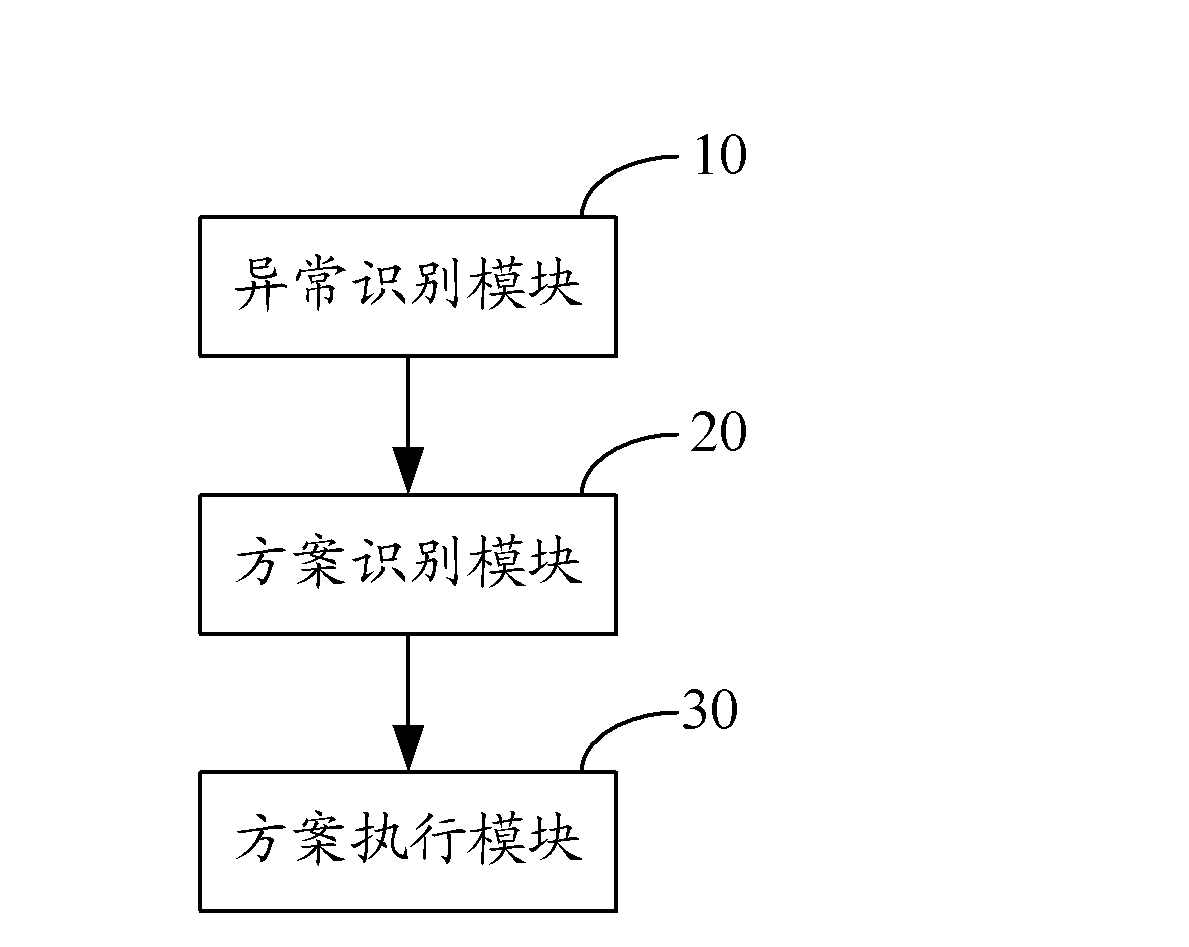
[0036] Such as figure 1 As shown, in one embodiment, a method for anomaly monitoring, comprising the following steps:
[0037] Step S10 , detecting abnormal key information, and identifying the abnormal type and abnormal level according to the abnormal key information.
[0038] Abnormal key information is the monitoring information dynamically obtained during the process of monitoring the system running status, including the running information of application software and environmental information such as CPU usage rate, memory usage rate, port status, and network bandwidth.
[0039] The abnormal key information in the present invention does not refer to the error information when an error occurs, but the information related to the abnormality. As long as the abnormal key information does not meet the set conditions, it is considered that an abnormality has occurred and needs to be repaired.
[0040] In one embodiment, exception types and exception levels can be set. The exce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com