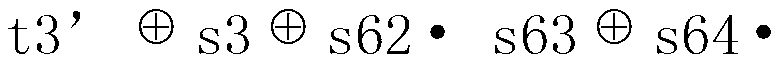Method for encrypting four non-linear driven light-weight stream ciphers
An encryption method and a lightweight technology, applied in the field of information security, can solve the problems of poor internal scrambling effect, vulnerability to attacks, and difficulty in implementing internal operations of stream cipher encryption algorithms, achieving the effect of easy internal operations.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
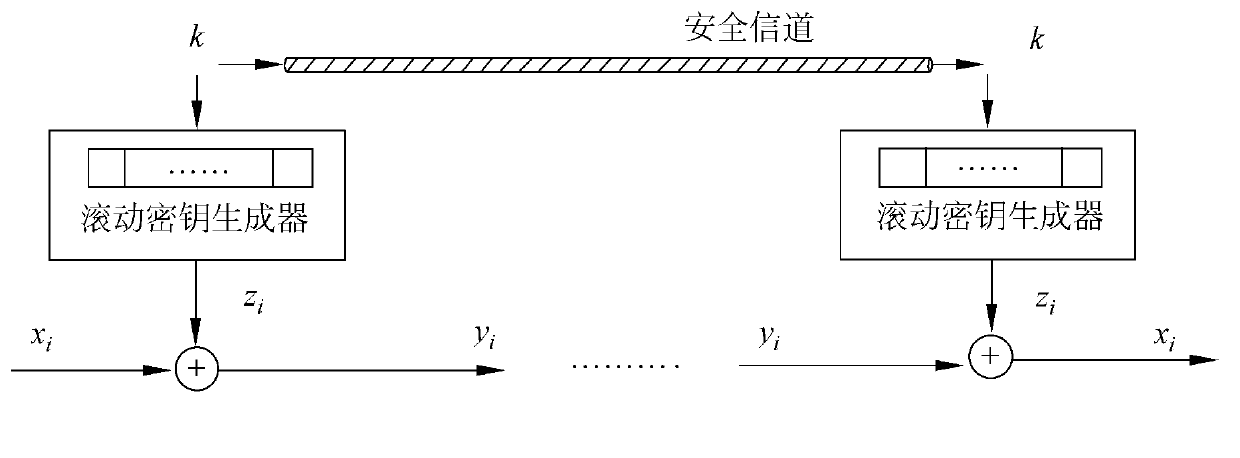
[0047] A light-weight stream cipher encryption method with four non-linear drivers, comprising the following steps:
[0048] The first stage is the internal state initialization stage.
[0049] (1.1) Randomly select a variable 88-bit seed key K=(k1, k2,...,k88), a variable 88-bit initial vector V=(v1, v2,...,v80 ), a fixed 80-bit constant value C=(c1, c2, ..., c80). In the present invention, the seed key K is always kept secret. The initial vector V is an arbitrary value agreed upon by both the sender and the receiver. The initial vector V can be kept secret or made public. In this embodiment, the constant value C is specifically (1, 0, 1, 0, . . . , 1, 0).
[0050] (1.2) Inject the above 88-bit seed key K, 88-bit initial vector V and 80-bit constant value C into a 256-bit long register (s1, s2, ..., s256). in
[0051] The state of registers (s1, s2, ..., s64) is injected by bits (k1, k2, ..., k22, v1, v2, ..., v22, c1, c2, ..., c20),
[0052] The state of registers (s6...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com