Anti-attack malicious software identification method and system
A malware and identification method technology, applied in the field of anti-attack malware identification methods and systems, can solve problems such as non-normal use, problems, system malicious attacks, etc., and achieve the effect of stable identification performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to make the purpose, technical solution, and advantages of the present invention clearer, the specific implementation examples of a service function authorization method and system involved in the present invention will be further described in detail below with reference to the accompanying drawings.
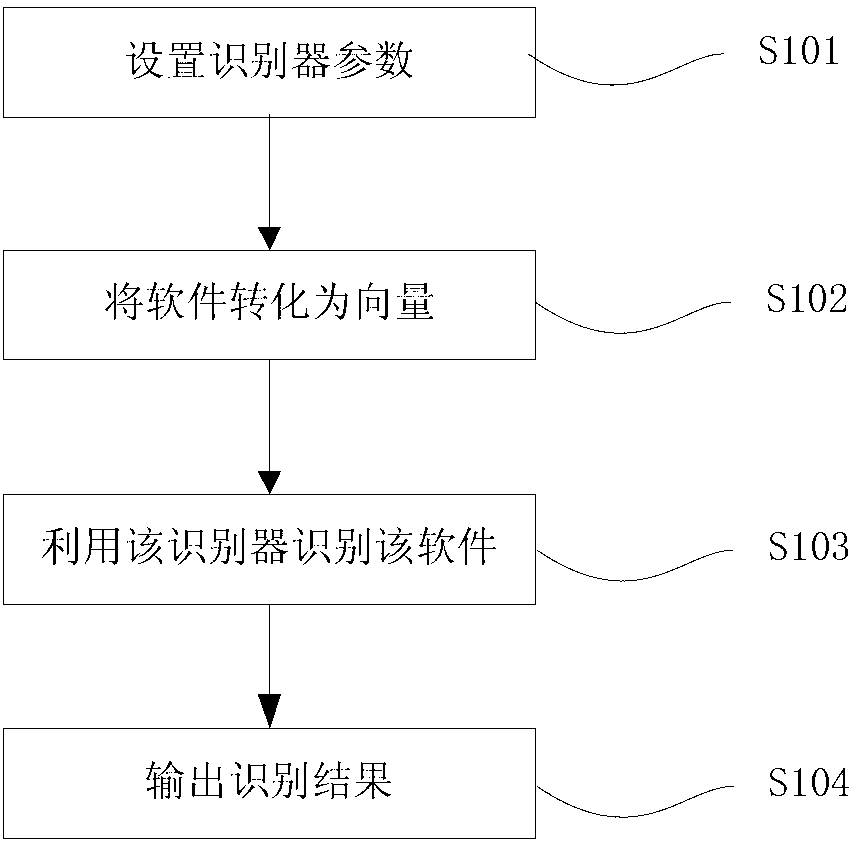
[0038] refer to figure 1 , the method flowchart of a preferred embodiment of the present invention,
[0039] Step S101, setting recognizer parameters,
[0040] Step S102, converting the software into vectors,
[0041] Step S103, using the identifier to identify the software,
[0042] Step S104, outputting the recognition result.
[0043] The invention converts each binary software program into a vector representation by using N-grams representation, and then carries out intelligent identification. Before it is applied to identify unknown software, the recognizer needs to be trained. The training process is the process of using existing software vector data, i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com