Method and device for ownership transfer of radio frequency identification (RFID) tag
A technology of RFID tags and transfer methods, applied in the direction of cooperative devices, instruments, computer components, etc., can solve the problems of loss of security protection, inability to resist replay attacks, etc., and achieve the effect of protecting privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] The present invention will be further described below in conjunction with the accompanying drawings of the description.
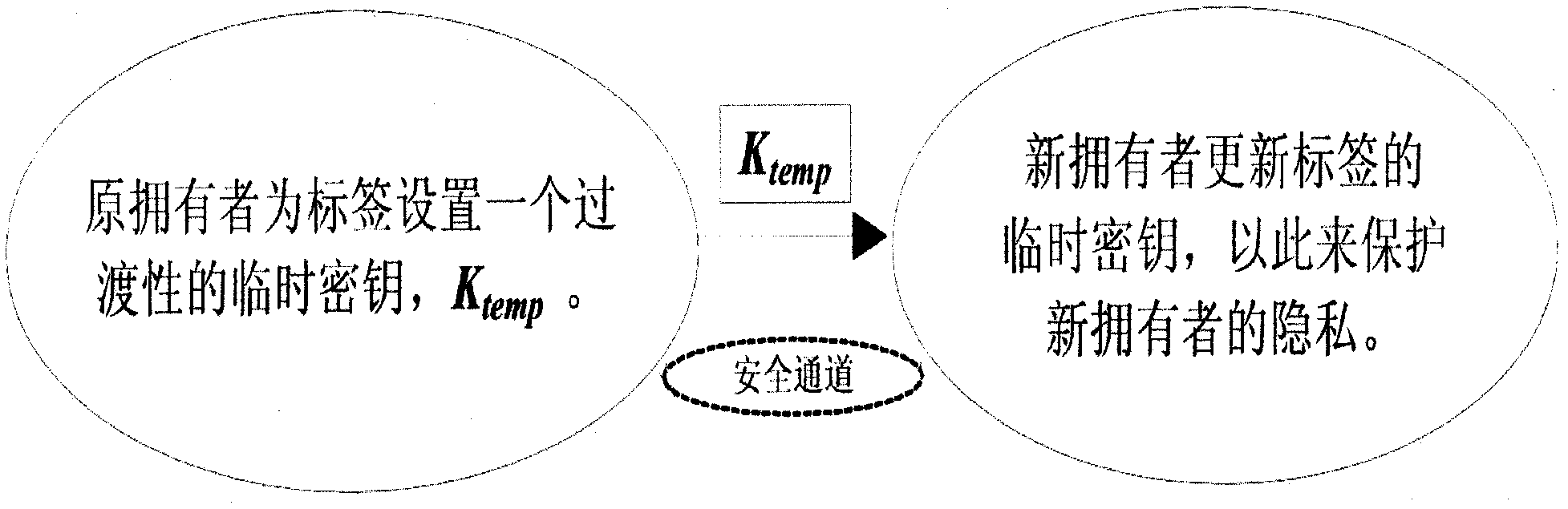
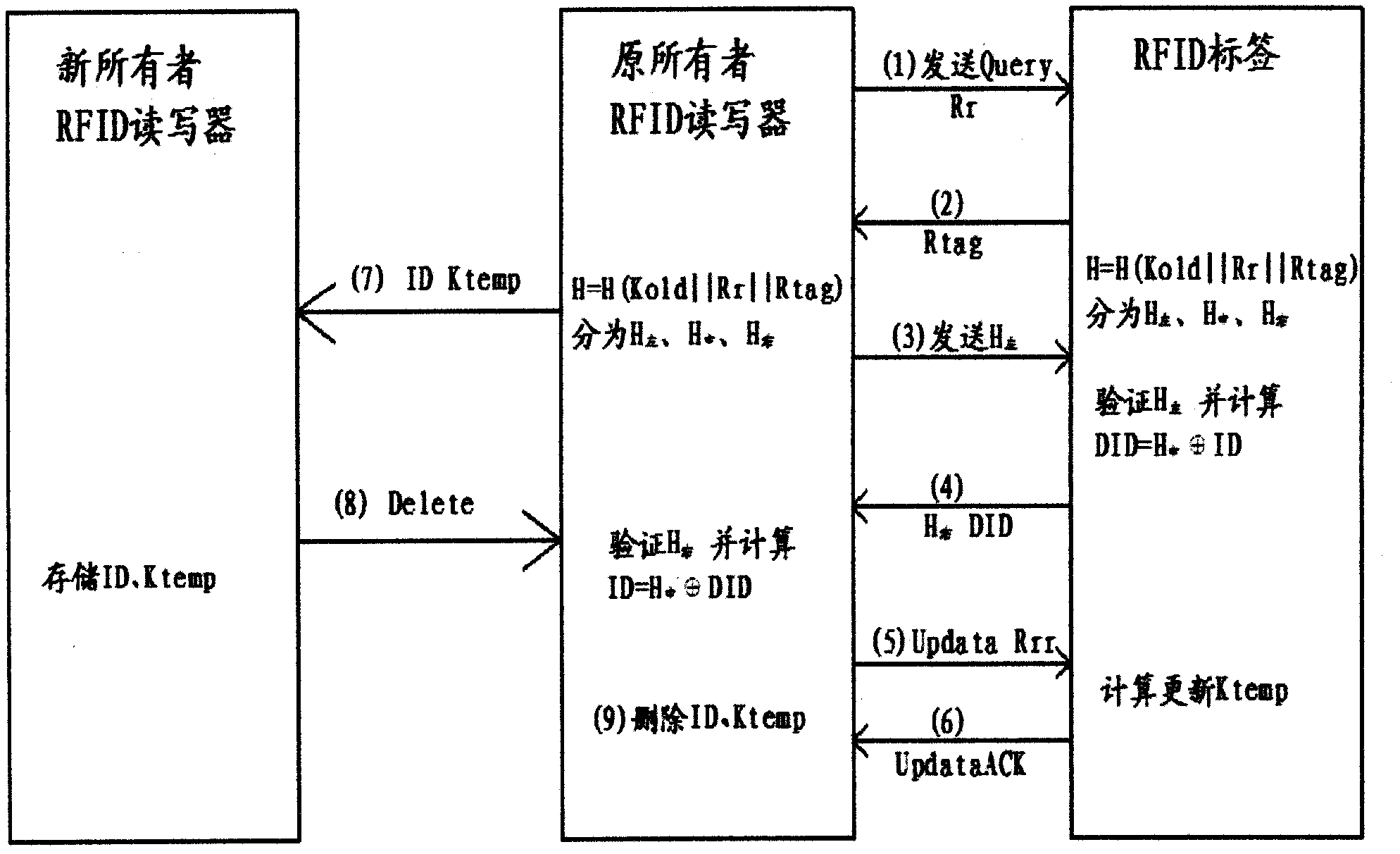
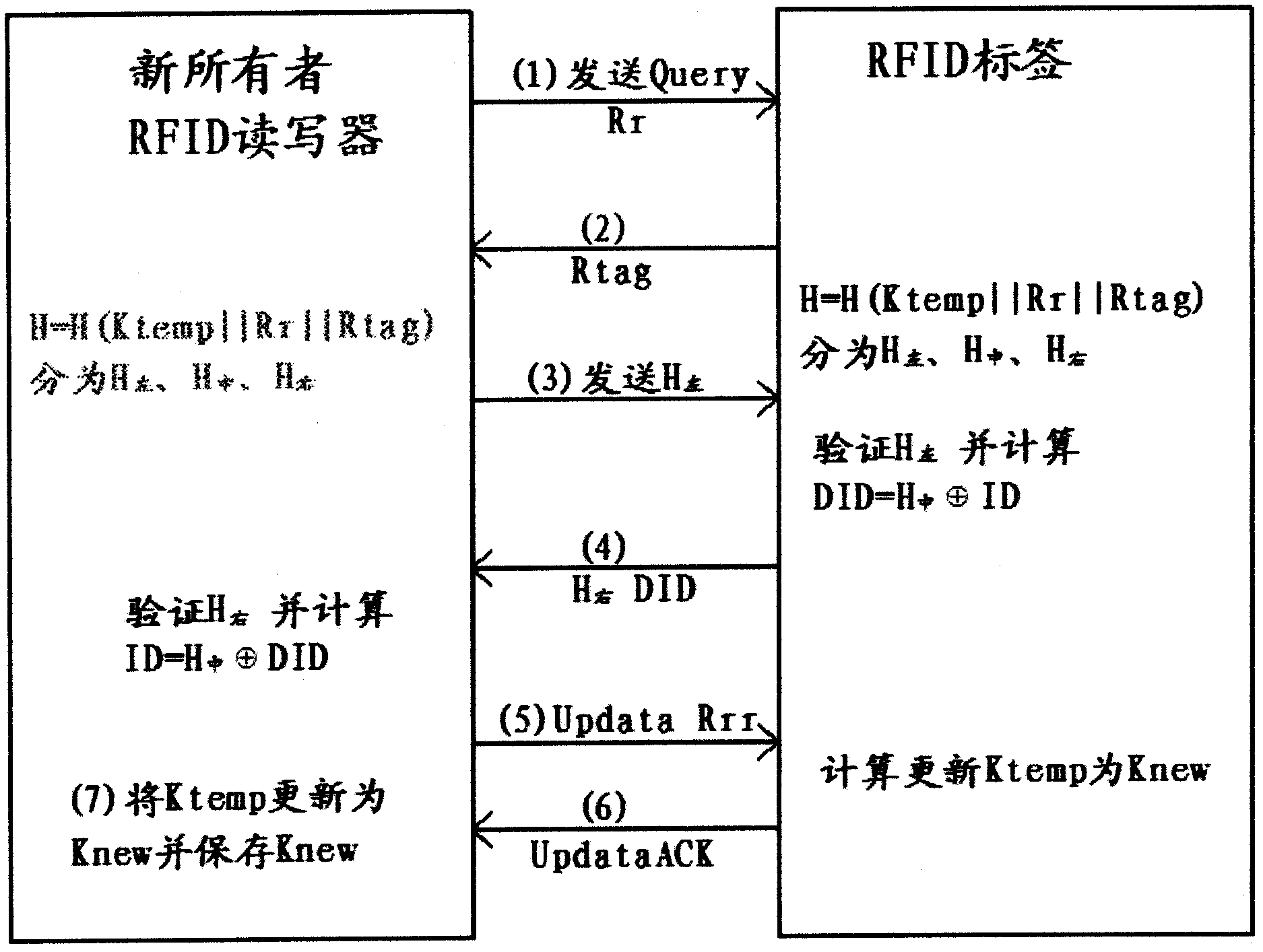
[0039] refer to figure 1 , the RFID tag ownership transfer method, through the RFID tag and the original owner's RFID reader, and with the new owner's RFID reader to renew the key, realize the RFID tag ownership transfer, the method includes the original owner's RFID reader The writer deletes the RFID tag key and the new owner’s RFID reader sets the RFID tag key. The original owner’s RFID reader sets the temporary key Ktemp for the RFID tag, and transfers Ktemp to the RFID tag through a secure channel. The temporary key is deleted after being transmitted to the RFID reader of the new owner, and the new owner's RFID reader reads the temporary key Ktemp of the authenticated RFID tag and sets a new key instead of the temporary key.
[0040] figure 2 It is a schematic flow diagram of the deletion process of the RFID tag key by the original owner's RFI...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com