Method for discovering Web intranet agent bugs
A technology of loopholes and intranets, applied in electrical digital data processing, instruments, computer security devices, etc., can solve the problem of impossible to achieve a high detection rate, and achieve the effect of improving Web security and reducing detection difficulty.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
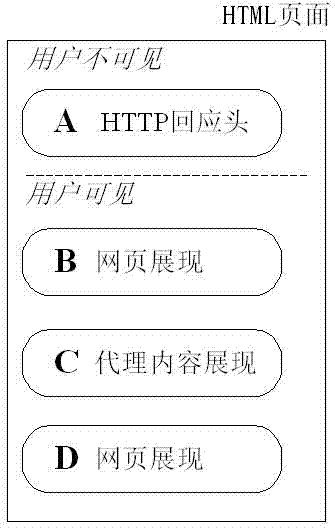
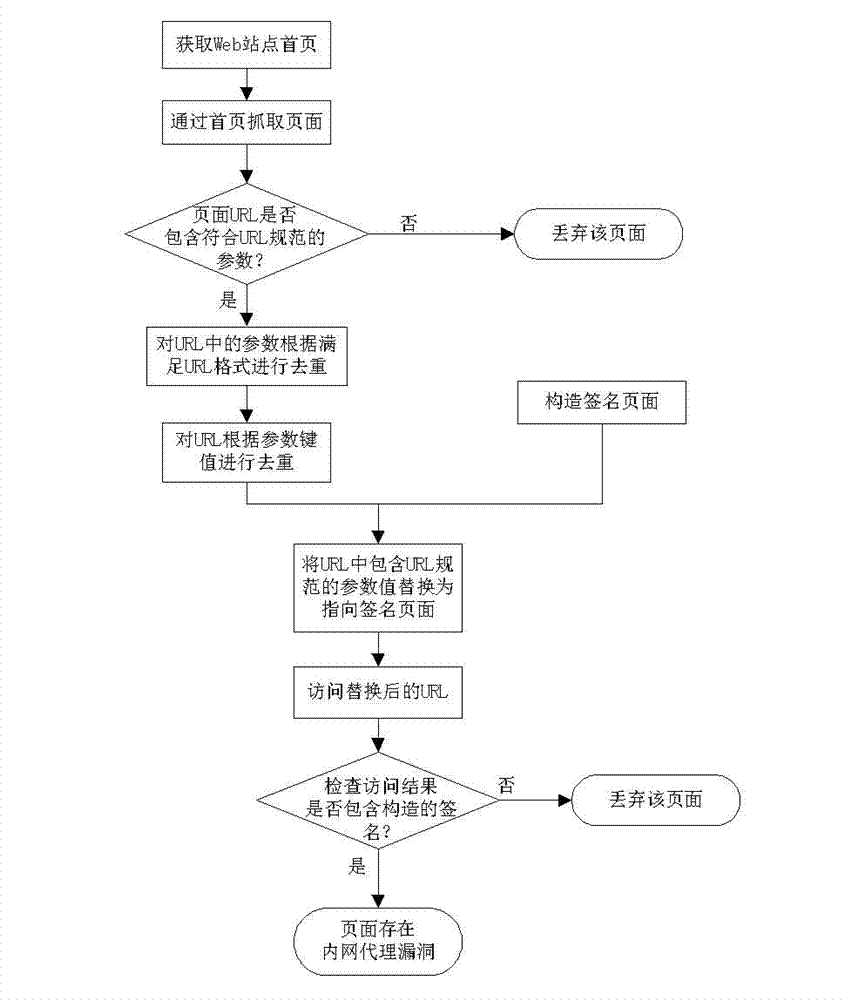
[0021] The invention uses a programmed method to discover and determine the loopholes of the intranet agent. When in use, the operator only needs to start the detection program.
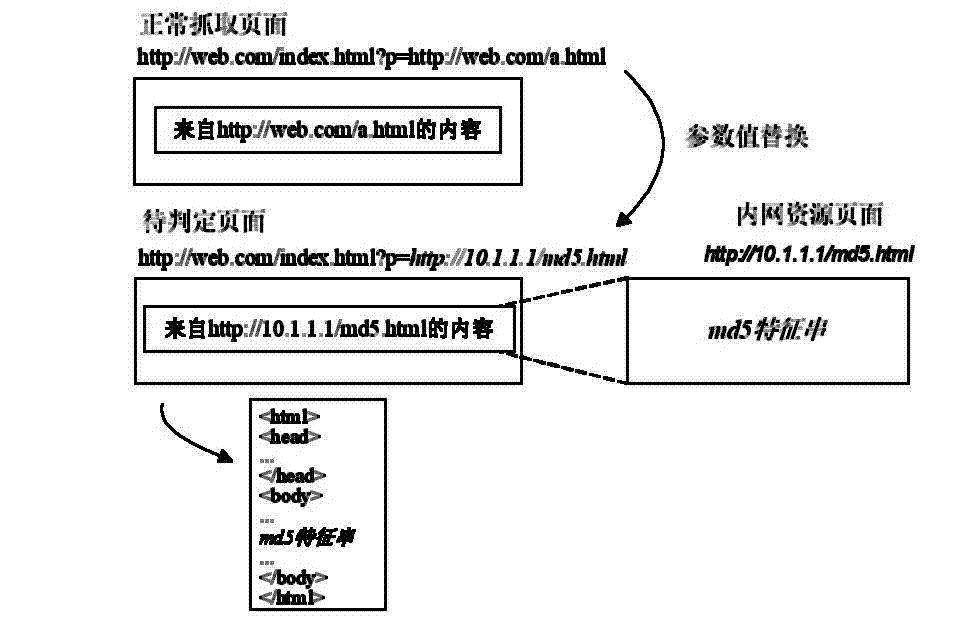
[0022] The present invention takes black-box testing as a starting point, and summarizes the black-box testing process into two parts: URL discovery and loophole verification.
[0023] URL discovery is used to extract all pages from a web application. Considering the variation of URL parameters, a typical web application usually contains tens of thousands to hundreds of thousands of independent URLs. Analyzing each URL independently would take a lot of time. Therefore, applying a filtering strategy based on the extracted results reduces the number of analyzes required to make the analysis time acceptable. If the URL is not filtered, the web intranet proxy vulnerability can also be found, but the execution of the program will take more time.
[0024] In the black box testing method, vulnerability ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com