Identification method for network access equipment and implementation system for identification method
A technology for device identification and system implementation, applied in the field of Internet applications, can solve problems such as distrust, affect honest customer transaction experience, hurt customer conversion rate, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in combination with examples of implementation and accompanying drawings.
[0031] The user of the present invention does not need to install software or a server, and only needs to use the client (or user) Internet device to access the website application program, insert HTML configuration tags and an HTTPS API call function to the client's web application server. User administrators can access the device fingerprint management platform to customize models and rules suitable for customers.
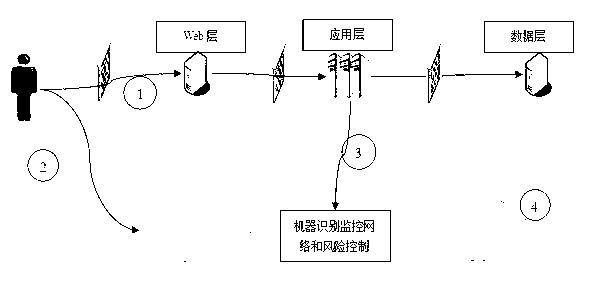
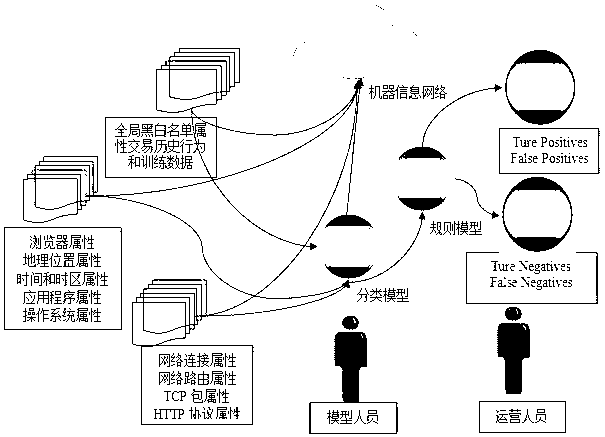
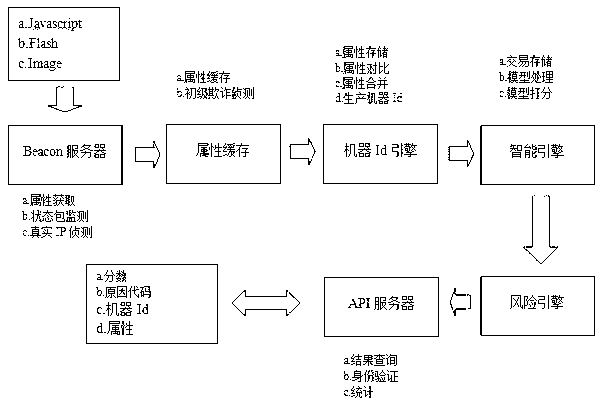
[0032] like figure 1 As shown, it is a system architecture diagram for realizing the Internet-connected device identification technology in the present invention, and the workflow of the whole Internet-connected device identification method can be summarized as the following steps through the system architecture diagram:
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com