System protecting method based on data security
A system protection and data security technology, applied in the redundancy of computing for data error detection, protection of storage content to prevent loss, response to errors, etc. Achieve the effect of ensuring security, small impact on reading and writing, and improving speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
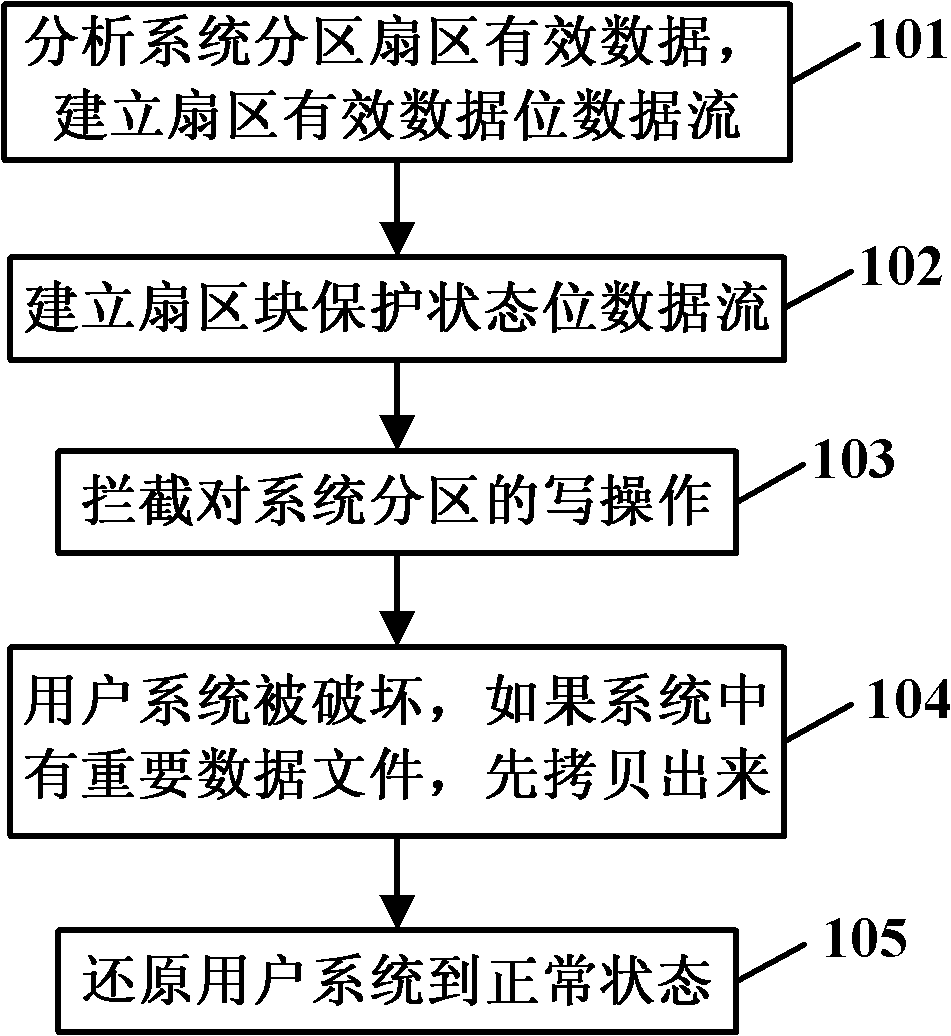
[0031] see figure 1 As shown, the system protection method based on data security provided by the embodiment of the present invention includes the following steps:
[0032] Step 101: Analyze the valid data of the system partition, and establish a sector valid data bit data stream. The sector valid data bit data stream is a data stream used to indicate whether the hard disk partition sector is valid data, 1 byte=8 bits, Wherein each 1 bit represents 1 sector, if the sector is valid data, the corresponding bit is marked as 1; otherwise, it is marked as 0.
[0033] Step 102: In order to improve the operating efficiency of the system, the sectors in the hard disk partition are divided into blocks according to every 128 sectors as a sector block, the 0-127 sectors in the partition are a sector block, and the 128-255 sectors are A sector block, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com